A new phishing marketing campaign has set its sights on European entities to distribute Remcos RAT and Formbook by way of a malware loader dubbed DBatLoader.
“The malware payload is dispersed by means of WordPress websites that have licensed SSL certificates, which is a widespread tactic made use of by danger actors to evade detection engines,” Zscaler scientists Meghraj Nandanwar and Satyam Singh explained in a report released Monday.
The findings establish on a past report from SentinelOne last month that in-depth phishing e-mails made up of destructive attachments that masquerade as economical files to activate the infection chain.
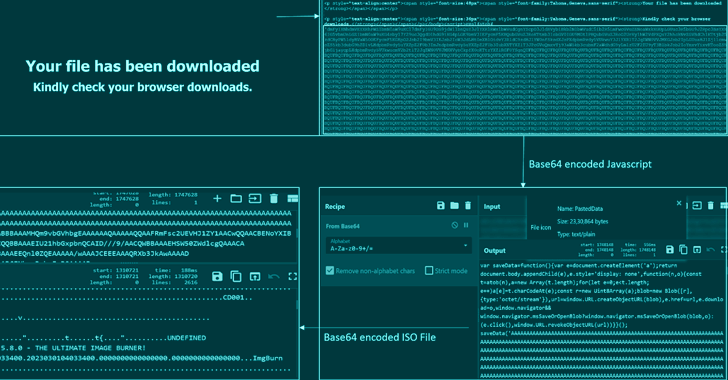
Some of the file formats applied to distribute the DBatLoader payload worry the use of a multi-layered obfuscated HTML file and OneNote attachments.
The advancement adds to growing abuse of OneNote information as an first vector for malware distribution considering that late past 12 months in reaction to Microsoft’s choice to block macros by default in information downloaded from the internet.
DBatLoader, also termed ModiLoader and NatsoLoader, is a Delphi-primarily based malware that is able of providing stick to-on payloads from cloud solutions like Google Travel and Microsoft OneDrive, when also adopting graphic steganography techniques to evade detection engines.
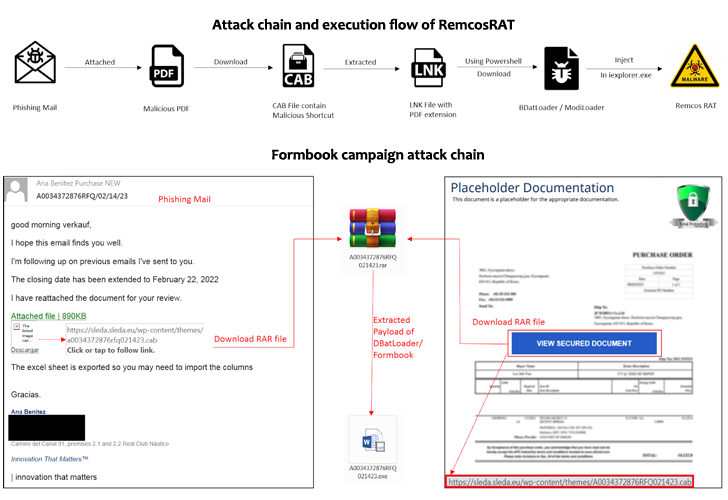
One particular noteworthy aspect of the attack is the use of mock trustworthy directories these kinds of as “C:Windows Procedure32” (take note the trailing space just after Windows) to bypass User Account Management (UAC) and escalate privileges.
WEBINARDiscover the Concealed Dangers of 3rd-Occasion SaaS Applications
Are you knowledgeable of the hazards affiliated with third-occasion application entry to your company’s SaaS applications? Be a part of our webinar to understand about the varieties of permissions remaining granted and how to lessen risk.
RESERVE YOUR SEAT
A caveat below is that the directories are unable to be specifically produced from in the Windows Explorer user interface, as an alternative necessitating the attacker to depend on a script to carry out the process and duplicate to the folder a rogue DLL and a legitimate executable (easinvoker.exe) which is susceptible to DLL hijacking in buy to load the DLL payload.
This enables the attackers to perform elevated pursuits without the need of alerting users, which include creating persistence and incorporating the “C:End users” listing to the Microsoft Defender exclusion checklist to stay away from obtaining scanned.
To mitigate pitfalls posed by DBatLoader, it’s suggested to monitor approach executions that contain filesystem paths with trailing areas and take into account configuring Windows UAC to Always notify.
Located this report interesting? Abide by us on Twitter and LinkedIn to read through much more exclusive content we publish.
Some parts of this article are sourced from:
thehackernews.com

 Four Years Behind Bars for Prolific BEC Scammer
Four Years Behind Bars for Prolific BEC Scammer