A new custom backdoor dubbed Stealth Soldier has been deployed as section of a set of hugely-specific espionage assaults in North Africa.
“Stealth Soldier malware is an undocumented backdoor that principally operates surveillance features these kinds of as file exfiltration, display and microphone recording, keystroke logging and stealing browser information,” cybersecurity business Verify Stage said in a technological report.
The ongoing operation is characterized by the use of command-and-regulate (C&C) servers that mimic web sites belonging to the Libyan Ministry of Foreign Affairs. The earliest artifacts involved with the campaign day again to Oct 2022.

The assaults begin with prospective targets downloading bogus downloader binaries that are delivered by using social engineering attacks and act as a conduit for retrieving Stealth Soldier, even though simultaneously exhibiting a decoy vacant PDF file.
The personalized modular implant, which is considered to be made use of sparingly, permits surveillance abilities by collecting directory listings and browser credentials, logging keystrokes, recording microphone audio, using screenshots, uploading documents, and managing PowerShell commands.
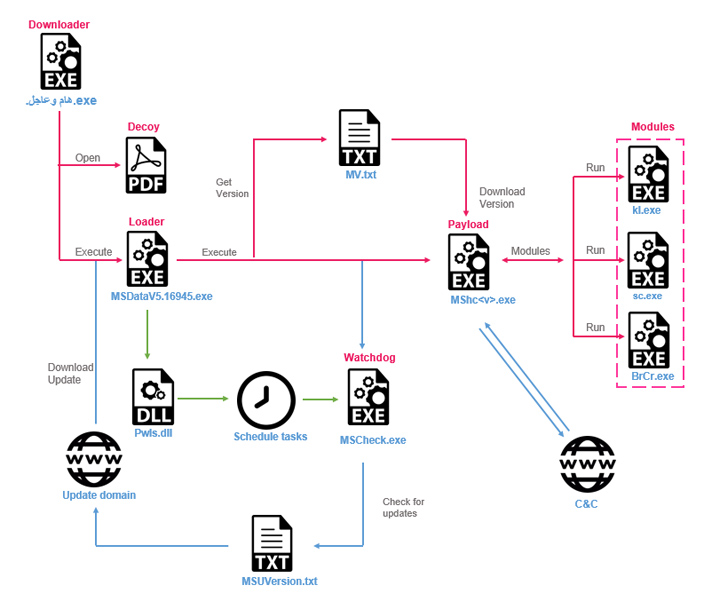
“The malware takes advantage of unique kinds of commands: some are plugins that are downloaded from the C&C and some are modules inside of the malware,” Check out Place explained, including the discovery of three variations of Stealth Soldier implies that it is really staying actively taken care of by its operators.
Some of the factors are no lengthier obtainable for retrieval, but the screen capture and browser credential stealer plugins are reported to have been influenced by open source assignments out there on GitHub.
Impending WEBINAR🔐 Mastering API Security: Knowing Your Accurate Attack Surface
Explore the untapped vulnerabilities in your API ecosystem and acquire proactive techniques in the direction of ironclad security. Sign up for our insightful webinar!
Be part of the Session.wn-button,.wn-label,.wn-label:afterdisplay:inline-block.check_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-correct-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.wn-label:soon afterwidth:50pxheight:6pxcontent:”border-leading:2px stable #d9deffmargin: 8px.wn-titlefont-dimensions:21pxpadding:10px 0font-pounds:900text-align:leftline-peak:33px.wn-descriptiontext-align:leftfont-measurement:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-sizing:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-weight:500letter-spacing:.2px
What is actually more, the Stealth Soldier infrastructure displays overlaps with infrastructure associated with an additional phishing marketing campaign dubbed Eye on the Nile, which qualified Egyptian journalists and human legal rights activists in 2019.
The improvement indicators the “1st attainable re-appearance of this menace actor” because then, suggesting the group is geared to surveillance in opposition to Egyptian and Libyan targets.
“Specified the modularity of the malware and the use of numerous levels of infection, it is probably that the attackers will proceed to evolve their ways and approaches and deploy new versions of this malware in the in the vicinity of long term,” Look at Point explained.
Uncovered this write-up fascinating? Abide by us on Twitter and LinkedIn to read more special written content we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Pharmaceutical Giant Eisai Hit By Ransomware Incident
Pharmaceutical Giant Eisai Hit By Ransomware Incident