Governmental entities in the Middle East and Africa have been at the acquiring end of sustained cyber-espionage attacks that leverage by no means-just before-viewed and exceptional credential theft and Trade email exfiltration procedures.
“The most important purpose of the assaults was to receive very private and delicate data, exclusively related to politicians, military things to do, and ministries of foreign affairs,” Lior Rochberger, senior danger researcher at Palo Alto Networks, explained in a complex deep dive printed previous 7 days.
The firm’s Cortex Menace Exploration staff is monitoring the exercise underneath the non permanent name CL-STA-0043 (where by CL stands for cluster and STA stands for condition-backed motivation), describing it as a “correct highly developed persistent risk.”
The an infection chain is induced by the exploitation of susceptible on-premises Internet Information Services (IIS) and Microsoft Exchange serves to infiltrate target networks.

Palo Alto Networks stated it detected failed tries to execute the China Chopper web shell in a person of the assaults, prompting the adversary to change techniques and leverage an in-memory Visible Essential Script implant from the Trade Server.
A successful split-in is followed by reconnaissance action to map out the network and single out critical servers that hold data of worth, like area controllers, web servers, Exchange servers, FTP servers, and SQL databases.
CL-STA-0043 has also been observed leveraging native Windows resources for privilege escalation, thus enabling it to create admin accounts and operate other plans with elevated privileges.
Another privilege escalation technique entails the abuse of accessibility characteristics in Windows – i.e., the “sticky keys” utility (sethc.exe) – that would make it attainable to bypass login necessities and backdoor the programs.
“In the attack, the attacker ordinarily replaces the sethc.exe binary or pointers/references to these binaries in the registry, with cmd.exe,” Rochberger explained. “When executed, it presents an elevated command prompt shell to the attacker to operate arbitrary commands and other equipment.”
A comparable strategy using the Utility Manager (utilman.exe) to build persistent backdoor access to a victim’s environment was documented by CrowdStrike previously this April.
Approaching WEBINAR🔐 Mastering API Security: Comprehending Your Genuine Attack Floor
Explore the untapped vulnerabilities in your API ecosystem and take proactive actions in the direction of ironclad security. Sign up for our insightful webinar!
Be part of the Session.wn-button,.wn-label,.wn-label:immediately aftershow:inline-block.check_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px solid #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top rated-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-proper-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-measurement:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.wn-label:right afterwidth:50pxheight:6pxcontent:”border-leading:2px solid #d9deffmargin: 8px.wn-titlefont-dimension:21pxpadding:10px 0font-excess weight:900textual content-align:leftline-peak:33px.wn-descriptiontext-align:leftfont-sizing:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-sizing:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-body weight:500letter-spacing:.2px
In addition to using Mimikatz for credential theft, the risk actor’s modus operandi stands out for using other novel techniques to steal passwords, carry out lateral movement, and exfiltrate sensitive data, these as –
- Making use of network suppliers to execute a destructive DLL to harvest and export plaintext passwords to a remote server
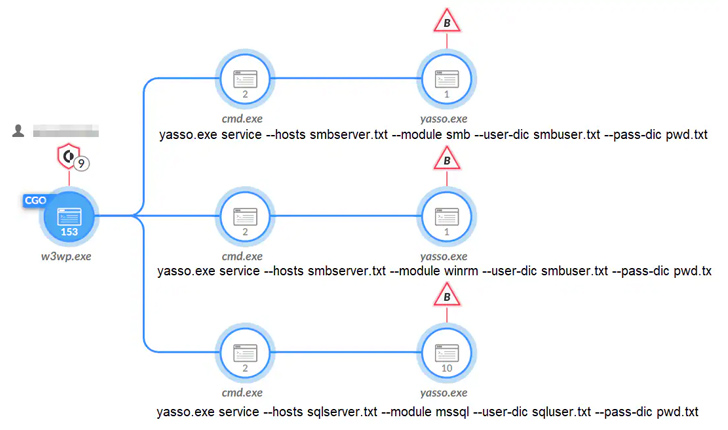
- leveraging an open up-source penetration testing toolset referred to as Yasso to spread throughout the network, and
- Using benefit of the Trade Administration Shell and PowerShell snap-ins to harvest e-mail of curiosity
It really is well worth pointing out that the use of Trade PowerShell snap-ins to export mailbox knowledge has been previously claimed in the circumstance of a Chinese point out-sponsored team dubbed Silk Storm (formerly Hafnium), which 1st came to light in March 2021 in relationship with the exploitation of Microsoft Exchange Server.
“This activity group’s degree of sophistication, adaptiveness, and victimology suggest a highly capable APT threat actor, and it is suspected to be a nation-condition menace actor,” Rochberger reported.
Uncovered this posting interesting? Comply with us on Twitter and LinkedIn to examine a lot more special information we article.
Some parts of this article are sourced from:
thehackernews.com


 Microsoft Blames Massive DDoS Attack for Azure, Outlook, and OneDrive Disruptions
Microsoft Blames Massive DDoS Attack for Azure, Outlook, and OneDrive Disruptions