The Android banking trojan known as SpyNote has been dissected to reveal its diverse data-collecting characteristics.
Usually spread via SMS phishing campaigns, attack chains involving the adware trick possible victims into setting up the app by clicking on the embedded website link, in accordance to F-Protected.
Moreover requesting invasive permissions to accessibility connect with logs, digital camera, SMS messages, and exterior storage, SpyNote is acknowledged for hiding its existence from the Android home monitor and the Recents monitor in a bid to make it complicated to stay away from detection.

“The SpyNote malware app can be launched through an external cause,” F-Safe researcher Amit Tambe reported in an evaluation printed very last 7 days. “On acquiring the intent, the malware application launches the main action.”
But most importantly, it seeks accessibility permissions, subsequently leveraging it to grant alone more permissions to file audio and phone calls, log keystrokes, as perfectly as seize screenshots of the phone by means of the MediaProjection API.
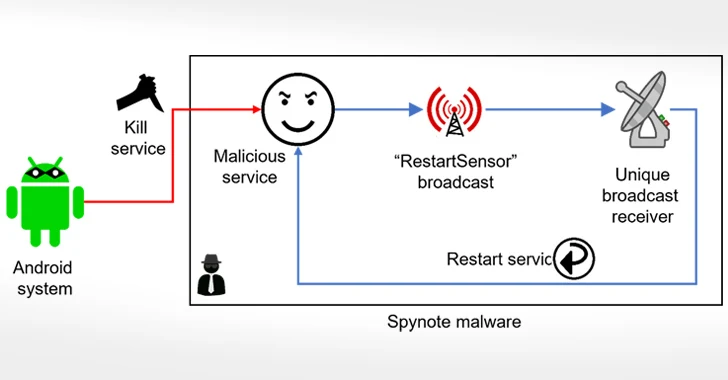
A closer assessment of the malware has unveiled the existence of what are called diehard companies that aim to resist attempts, both created by the victims or by the operating procedure, at terminating it.
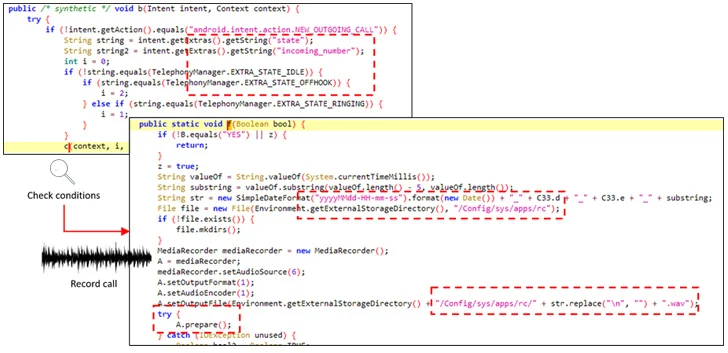
This is achieved by registering a broadcast receiver which is developed to restart it routinely when it is about to be shut down. What is extra, buyers who attempt to uninstall the malicious app by navigating to Options are prevented from accomplishing so by closing the menu display through its abuse of the accessibility APIs.
“The SpyNote sample is spy ware that logs and steals a selection of facts, such as crucial strokes, phone logs, information on set up purposes, and so on,” Tambe said. “It stays hidden on the victim’s device building it demanding to observe. It also will make uninstallation particularly tough.”

“The victim is at some point left only with the solution of executing a factory reset, getting rid of all knowledge, thereby, in the method.”
The disclosure comes as the Finnish cybersecurity agency comprehensive a bogus Android app that masquerades as an running process update to entice targets into granting it accessibility solutions permissions and exfiltrate SMS and lender facts.
Discovered this posting appealing? Abide by us on Twitter and LinkedIn to read through extra unique content we submit.
Some parts of this article are sourced from:
thehackernews.com

 The Fast Evolution of SaaS Security from 2020 to 2024 (Told Through Video)
The Fast Evolution of SaaS Security from 2020 to 2024 (Told Through Video)