A refined phishing campaign is using a Microsoft Word doc lure to distribute a trifecta of threats, specifically Agent Tesla, OriginBotnet, and OriginBotnet, to gather a extensive assortment of facts from compromised Windows equipment.
“A phishing email delivers the Word doc as an attachment, presenting a intentionally blurred picture and a counterfeit reCAPTCHA to lure the receiver into clicking on it,” Fortinet FortiGuard Labs researcher Cara Lin claimed.
Clicking on the impression potential customers to the supply of a loader from a distant server that, in convert, is made to distribute OriginBotnet for keylogging and password recovery, RedLine Clipper for cryptocurrency theft, and Agent Tesla for harvesting delicate info.
The loader, composed in .NET, employs a procedure called binary padding by introducing null bytes to enhance the file’s sizing to 400 MB in an endeavor to evade detection by security software program.

The activation of the loader triggers a multi-phase course of action to create persistence on the host and extract a dynamic-url library (DLL) which is responsible for unleashing the last payloads.
A person between them is RedLine Clipper, a .NET executable for thieving cryptocurrencies by tampering with the user’s method clipboard to substitute the vacation spot wallet tackle with an attacker-controlled one particular.
“To carry out this procedure, RedLine Clipper utilizes the ‘OnClipboardChangeEventHandler’ to regularly check clipboard alterations and verify if the copied string conforms to the frequent expression,” Lin stated.
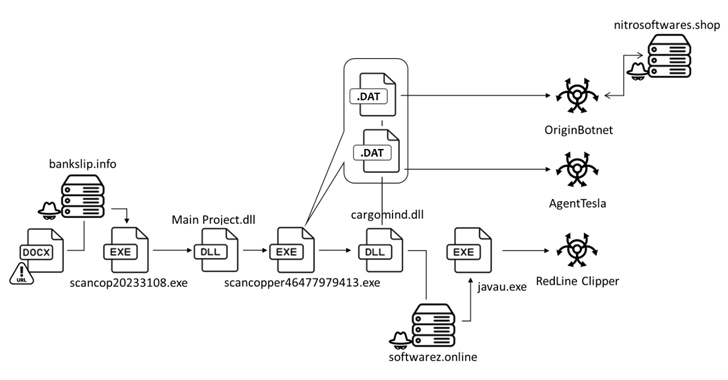
Agent Tesla, on the other hand, is a .NET-based mostly remote accessibility trojan (RAT) and data stealer for getting initial entry and exfiltrating sensitive data these types of as keystrokes and login qualifications applied in web browsers to a command-and-command (C2) server about SMTP protocol.
Also shipped is a new malware dubbed OriginBotnet, which packs in a extensive range of attributes to obtain facts, create communications with its C2 server, and down load supplementary plugins from the server to execute keylogging or password restoration functions on compromised endpoints.
Forthcoming WEBINARWay Also Vulnerable: Uncovering the Condition of the Identification Attack Floor
Achieved MFA? PAM? Services account defense? Come across out how very well-outfitted your group definitely is from identification threats
Supercharge Your Expertise
“The PasswordRecovery plugin retrieves and organizes the credentials of numerous browser and application accounts,” Lin said. “It data these results and reviews them by using HTTP Post requests.”
It is really well worth noting that Palo Alto Networks Unit 42, in September 2022, in-depth an Agent Tesla successor termed OriginLogger, which comes with identical functions as that of OriginBotnet, suggesting that they could be each the operate of the very same threat actor.
“This cyberattack campaign […] concerned a elaborate chain of functions,” Fortinet explained. “It began with a destructive Phrase doc dispersed by way of phishing e-mail, top victims to download a loader that executed a collection of malware payloads. The attack demonstrated innovative procedures to evade detection and maintain persistence on compromised units.”
Located this write-up attention-grabbing? Stick to us on Twitter and LinkedIn to examine more distinctive content material we article.
Some parts of this article are sourced from:
thehackernews.com


 Beware: MetaStealer Malware Targets Apple macOS in Recent Attacks
Beware: MetaStealer Malware Targets Apple macOS in Recent Attacks