An up-to-date model of a complex backdoor framework called MATA has been applied in attacks aimed at over a dozen Japanese European firms in the oil and gas sector and protection marketplace as aspect of a cyber espionage operation that took location involving August 2022 and May possibly 2023.
“The actors guiding the attack applied spear-phishing mails to goal various victims, some ended up infected with Windows executable malware by downloading information as a result of an internet browser,” Kaspersky said in a new exhaustive report printed this 7 days.
“Every phishing document is made up of an exterior website link to fetch a distant website page that contains a CVE-2021-26411 exploit.”
CVE-2021-26411 (CVSS rating: 8.8) refers to a memory corruption vulnerability in Internet Explorer that could be triggered to execute arbitrary code by tricking a target into visiting a specifically crafted web site. It was formerly exploited by the Lazarus Team in early 2021 to focus on security scientists.
The cross-system MATA framework was very first documented by the Russian cybersecurity business in July 2020, linking it to the prolific North Korean condition-sponsored crew in assaults focusing on different sectors in Poland, Germany, Turkey, Korea, Japan, and India due to the fact April 2018.
The use of a revamped edition of MATA to strike protection contractors was formerly disclosed by Kaspersky in July 2023, though attribution to the Lazarus Group remains tenuous at ideal due to the presence of techniques made use of by Five Eyes APT actors these kinds of as Purple Lambert, Magenta Lambert, and Environmentally friendly Lambert.

That explained, a majority of the destructive Microsoft Term documents created by the attackers attribute a Korean font termed Malgun Gothic, suggesting that the developer is possibly common with Korean or will work in a Korean surroundings.
Russian cybersecurity firm Beneficial Technologies, which shared information of the exact same framework late previous thirty day period, is tracking the operators below the moniker Dark River.
“The group’s most important device, the MataDoor backdoor, has a modular architecture, with a complex, extensively built procedure of network transports and flexible choices for interaction involving the backdoor operator and an contaminated machine,” security researchers Denis Kuvshinov and Maxim Andreev claimed.
“The code examination suggests that the developers invested sizeable means into the resource.”
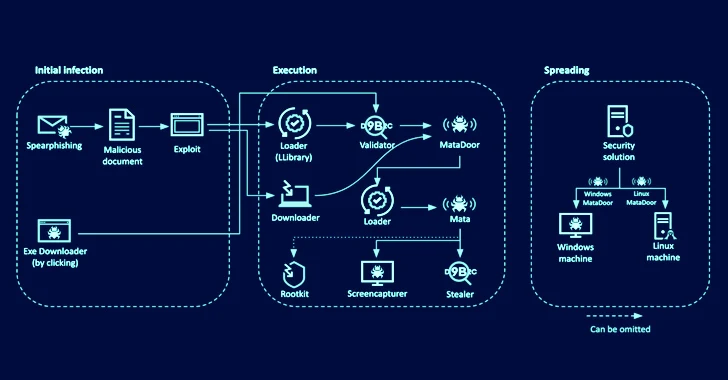
The latest attack chains start with the actor sending spear-phishing paperwork to targets, in some conditions by impersonating legitimate staff, indicating prior reconnaissance and comprehensive preparing. These files contain a backlink to an HTML site that embeds an exploit for CVE-2021-26411.
A effective compromise prospects to the execution of a loader that, in transform, retrieves a Validator module from a distant server to deliver technique information and facts and download and upload data files to and from the command-and-management (C2) server.
The Validator is also developed to fetch MataDoor, which, according to Kasperksy, is MATA era 4 that is geared up to operate a vast assortment of commands capable of gathering delicate facts from compromised units.
The attacks are further more characterised by the use of stealer malware to capture written content from clipboard, record keystrokes, choose screenshots, and siphon passwords and cookies from the Windows Credential Supervisor and Internet Explorer.
Yet another noteworthy device is a USB propagation module that lets for sending commands to the contaminated system by means of removable media, very likely enabling the danger actors to infiltrate air-gapped networks. Also employed is an exploit known as CallbackHell to elevate privileges and bypass endpoint security items so as to realize their targets with no attracting focus.

Kaspersky stated it also found out a new MATA variant, dubbed MATA era 5 or MATAv5, that is “completely rewritten from scratch” and “reveals an highly developed and sophisticated architecture producing use of loadable and embedded modules and plugins.”
“The malware leverages inter-method conversation (IPC) channels internally and employs a varied range of instructions, enabling it to establish proxy chains across many protocols – also within just the victim’s atmosphere,” the firm additional.
In overall, the MATA framework and its cocktail of plugins integrate help for above 100 instructions pertaining to info accumulating, celebration monitoring, procedure administration, file management, network reconnaissance, and proxy performance.
“The actor demonstrated superior capabilities of navigating as a result of and leveraging security methods deployed in the victim’s natural environment,” Kaspersky reported.
“Attackers employed several tactics to conceal their activity: rootkits and susceptible drivers, disguising data files as respectable programs, applying ports open for conversation among purposes, multi-degree encryption of documents and network activity of malware, [and] location prolonged wait occasions amongst connections to regulate servers.”
Observed this report attention-grabbing? Observe us on Twitter and LinkedIn to read extra exclusive material we submit.
Some parts of this article are sourced from:
thehackernews.com

 Vulnerability Scanning: How Often Should I Scan?
Vulnerability Scanning: How Often Should I Scan?