As numerous as 165 shoppers of Snowflake are mentioned to have had their information perhaps exposed as component of an ongoing campaign developed to aid knowledge theft and extortion, indicating the procedure has broader implications than beforehand considered.
Google-owned Mandiant, which is aiding the cloud info warehousing system in its incident reaction efforts, is tracking the as-nonetheless-unclassified activity cluster beneath the title UNC5537, describing it as a economically enthusiastic menace actor.
“UNC5537 is systematically compromising Snowflake shopper situations using stolen consumer credentials, advertising victim data for sale on cybercrime discussion boards, and attempting to extort lots of of the victims,” the risk intelligence business explained on Monday.
“UNC5537 has focused hundreds of companies all over the world, and frequently extorts victims for financial gain. UNC5537 operates under various aliases on Telegram channels and cybercrime boards.”
There is proof to counsel that the hacking team is produced up of associates primarily based in North The usa. It is also believed to collaborate with at least just one added party centered in Turkey.

This is the to start with time that the selection of influenced consumers has been formally disclosed. Previously, Snowflake had observed that a “restricted variety” of its customers were impacted by the incident. The business has additional than 9,820 international customers.
The marketing campaign, as earlier outlined by Snowflake, stems from compromised customer credentials obtained from cybercrime forums or acquired through information-thieving malware this sort of as Lumma, MetaStealer, Raccoon, RedLine, RisePro, and Vidar. It truly is considered to have commenced on April 14, 2024.
In several instances, the stealer malware bacterial infections have been detected on contractor methods that were also applied for own things to do, this sort of as gaming and downloading pirated computer software, the latter of which has been a experimented with-and-analyzed conduit for distributing stealers.
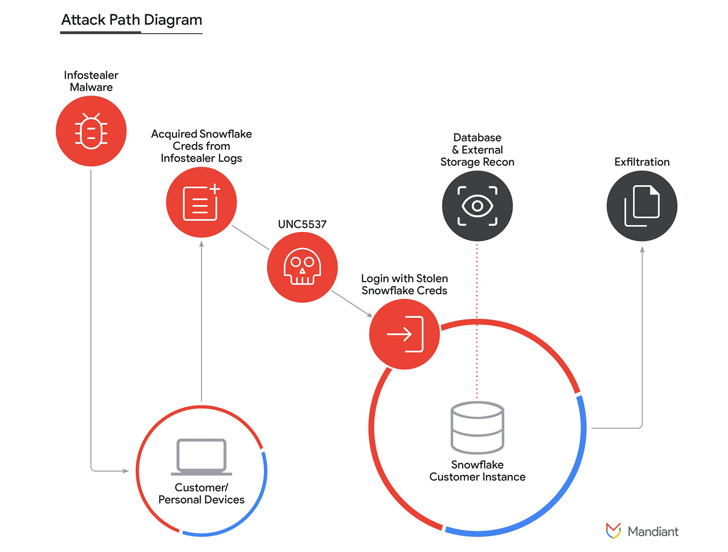
The unauthorized obtain to customer circumstances has been located to pave the way for a reconnaissance utility dubbed FROSTBITE (aka “rapeflake”) that’s made use of to operate SQL queries and glean details about the end users, existing roles, recent IPs, session IDs, and corporation names.
Mandiant stated it has been unable to acquire a comprehensive sample of FROSTBITE, with the organization also spotlighting the risk actor’s use of a authentic utility termed DBeaver Greatest to link and operate SQL queries throughout Snowflake occasions. The last stage of the attack entails the adversary functioning instructions to stage and exfiltrate knowledge.
Snowflake, in an up-to-date advisory, mentioned it’s performing intently with its customers to harden their security steps. It also said it really is producing a plan to require them to put into action advanced security controls, like multi-aspect authentication (MFA) or network insurance policies.
The attacks, Mandiant pointed out, have turn out to be hugely prosperous because of to three major reasons: deficiency of multi-element authentication (MFA), not rotating credentials periodically, and lacking checks to guarantee obtain only from dependable spots.

“The earliest infostealer infection date observed related with a credential leveraged by the menace actor dated again to November 2020,” Mandiant reported, incorporating it “identified hundreds of client Snowflake credentials exposed via infostealers considering the fact that 2020.”
“This campaign highlights the implications of huge quantities of credentials circulating on the infostealer market and could be consultant of a specific focus by risk actors on equivalent SaaS platforms.”
The results provide to underscore the burgeoning marketplace need for data stealers and the pervasive risk they pose to companies, ensuing in the common emergence of new stealer variants like AsukaStealer, Cuckoo, Iluria, k1w1, SamsStealer, and Seidr that are available for sale to other legal actors.
“In February, Sultan, the name driving Vidar malware, shared an image showcasing the Lumma and Raccoon stealers, depicted jointly in beat from antivirus methods,” Cyfirma explained in a latest analysis. “This indicates collaboration amongst risk actors, as they be part of forces and share infrastructure to realize their plans.”
Uncovered this article attention-grabbing? Adhere to us on Twitter and LinkedIn to go through far more special content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Arm Warns of Actively Exploited Zero-Day Vulnerability in Mali GPU Drivers
Arm Warns of Actively Exploited Zero-Day Vulnerability in Mali GPU Drivers