A new exploitation approach termed Uncomplicated Mail Transfer Protocol (SMTP) smuggling can be weaponized by danger actors to deliver spoofed emails with fake sender addresses although bypassing security actions.
“Threat actors could abuse susceptible SMTP servers worldwide to mail destructive emails from arbitrary email addresses, letting specific phishing assaults,” Timo Longin, a senior security guide at SEC Seek the advice of, said in an analysis revealed last month.
SMTP is a TCP/IP protocol utilised to send and get email messages in excess of a network. To relay a concept from an email customer (aka mail user agent), an SMTP connection is recognized between the customer and server in get to transmit the actual material of the email.

The server then depends on what’s named a mail transfer agent (MTA) to check out the domain of the recipient’s email deal with, and if it can be different from that of the sender, it queries the area title program (DNS) to seem up the MX (mail exchanger) history for the recipient’s area and total the mail trade.
The crux of SMTP smuggling is rooted in the inconsistencies that crop up when outbound and inbound SMTP servers deal with conclusion-of-data sequences otherwise, potentially enabling danger actors to break out of the concept knowledge, “smuggle” arbitrary SMTP commands, and even deliver individual e-mails.
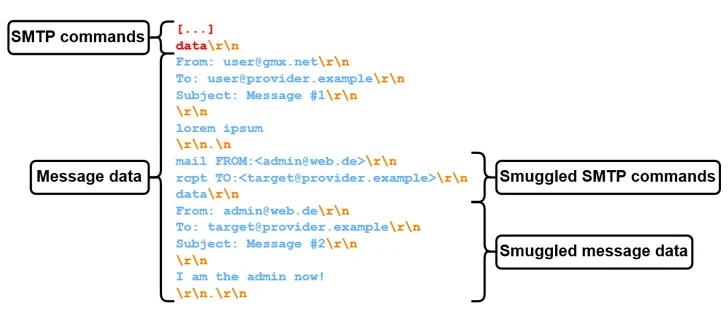
It borrows the thought from a known attack strategy known as HTTP request smuggling, which requires gain of discrepancies in the interpretation and processing of the “Content material-Length” and “Transfer-Encoding” HTTP headers to prepend an ambiguous ask for to the inbound request chain.
Precisely, it exploits security flaws in messaging servers from Microsoft, GMX, and Cisco to ship emails spoofing hundreds of thousands of domains. Also impacted are SMTP implementations from Postfix and Sendmail.

This allows for sending forged emails that seemingly search like they are originating from genuine senders and defeat checks in place erected to ensure the authenticity of incoming messages – i.e., DomainKeys Identified Mail (DKIM), Area-dependent Concept Authentication, Reporting and Conformance (DMARC), and Sender Policy Framework (SPF).
Even though Microsoft and GMX have rectified the issues, Cisco claimed the findings do not represent a “vulnerability, but a element and that they will not adjust the default configuration.” As a final result, inbound SMTP smuggling to Cisco Secure Email occasions is nonetheless achievable with default configurations.
As a repair, SEC Check with recommends Cisco buyers adjust their settings from “Cleanse” to “Allow for” in purchase to stay clear of obtaining spoofed e-mail with legitimate DMARC checks.
Found this write-up interesting? Observe us on Twitter and LinkedIn to read through additional exclusive material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 DOJ Slams XCast with $10 Million Fine Over Massive Illegal Robocall Operation
DOJ Slams XCast with $10 Million Fine Over Massive Illegal Robocall Operation