A fiscally inspired campaign has been focusing on on the net payment companies in the Asia Pacific, North The usa, and Latin The us with web skimmers for more than a year.
The BlackBerry Study and Intelligence Team is tracking the activity below the name Silent Skimmer, attributing it to an actor who is proficient in the Chinese language. Outstanding victims include on the internet businesses and stage-of-sale (PoS) service providers.
“The campaign operators exploit vulnerabilities in web apps, especially these hosted on Internet Details Services (IIS),” the Canadian cybersecurity organization said. “Their most important aim is to compromise the payment checkout web site, and swipe visitors’ delicate payment details.”
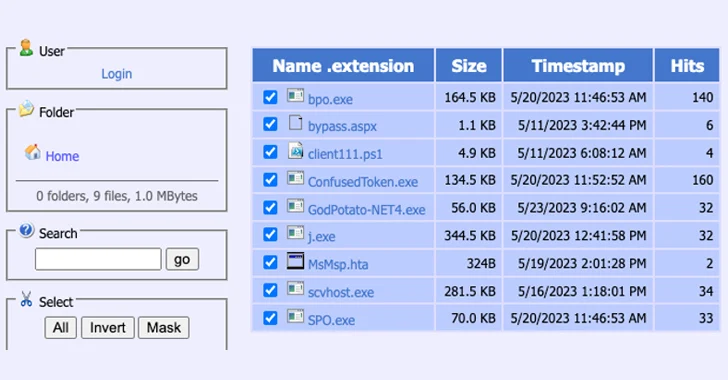
A thriving first foothold is adopted by the menace actors leveraging numerous open-source equipment and dwelling-off-the-land (LotL) techniques for privilege escalation, write-up-exploitation, and code execution.

The attack chain prospects to the deployment of a PowerShell-primarily based distant accessibility trojan (server.ps1) that will allow for remotely managing the host, which, in transform, connects to a distant server that hosts extra utilities, such as downloading scripts, reverse proxies and Cobalt Strike beacons.
The end intention of the intrusion, for every BlackBerry, is to infiltrate the web server and drop a scraper in the payment checkout company by signifies of a web shell and stealthily seize the money information entered by victims on the page.
An examination of the adversary’s infrastructure reveals that the virtual personal servers (VPS) employed for command-and-handle (C2) are picked centered on the geolocation of the victims in an hard work to evade detection.
The variety of industries and locations specific, coupled with the type of servers breached, factors to an opportunistic campaign fairly than a deliberate method.
“The attacker focuses predominantly on regional sites that gather payment details, using edge of vulnerabilities in commonly made use of technologies to achieve unauthorized access and retrieve delicate payment info entered into or stored on the web page,” BlackBerry explained.

The disclosure comes as Sophos disclosed facts of a pig butchering rip-off in which possible targets are lured into investing in bogus cryptocurrency investment decision schemes just after remaining approached on dating applications like MeetMe, netting the actors hundreds of thousands in illicit revenue.
What sets the most current operation apart is the use of liquidity mining lures, promising buyers common revenue at higher charges of return for investment in a liquidity pool, where by the digital assets are parked to aid trades on decentralized exchanges.
“These ripoffs call for no malware on the target’s gadget, and no ‘hacking’ of any form other than fraudulent sites and social engineering — convincing targets to connect their wallet to an Ethereum sensible contract that presents the scammers authorization to empty the wallet,” security researcher Sean Gallagher reported.
Found this article intriguing? Abide by us on Twitter and LinkedIn to examine more exceptional content we post.
Some parts of this article are sourced from:
thehackernews.com

 OpenRefine’s Zip Slip Vulnerability Could Let Attackers Execute Malicious Code
OpenRefine’s Zip Slip Vulnerability Could Let Attackers Execute Malicious Code