In the very last ten years, there has been a developing disconnect involving front-line analysts and senior administration in IT and Cybersecurity. Very well-documented issues going through contemporary analysts revolve around a superior quantity of alerts, wrong positives, weak visibility of technological environments, and analysts investing much too a great deal time on manual responsibilities.
The Effects of Alert Tiredness and False Positives
Analysts are confused with alerts. The knock-on outcome of this is that fatigued analysts are at risk of lacking critical information in incidents, and typically perform time-consuming triaging responsibilities manually only to end up copying and pasting a generic closing remark into a phony beneficial inform.
It is possible that there will normally be wrong positives. And many would argue that a untrue constructive is much better than a bogus unfavorable. But for proactive steps to be manufactured, we have to go closer to the coronary heart of an incident. That calls for diving into how analysts perform the triage and investigation process.
SHQ Response System for Triage and Investigation
A regular triage process is typically manual, and leverages analysts to carry out person log lookups for contextual data. From this information and facts, they commence to piece with each other a tale of what has occurred and offer an thought of the overall risk scale.
The SHQ Reaction Platform makes use of Synthetic Intelligence (AI) for log correlation, pulling data from different sources and visualizing it in a single incident site. From this, critical info is offered across a distinct timeline, and artifacts are updated on the portal automatically.
By acquiring the most essential knowledge introduced in a person position, an investigating analyst can slice by means of the noise and stay in one particular interface. They no for a longer time will need to pivot throughout numerous log resources or carry out manual SIEM queries to get the suitable logs to then recognize the story of a security incident.
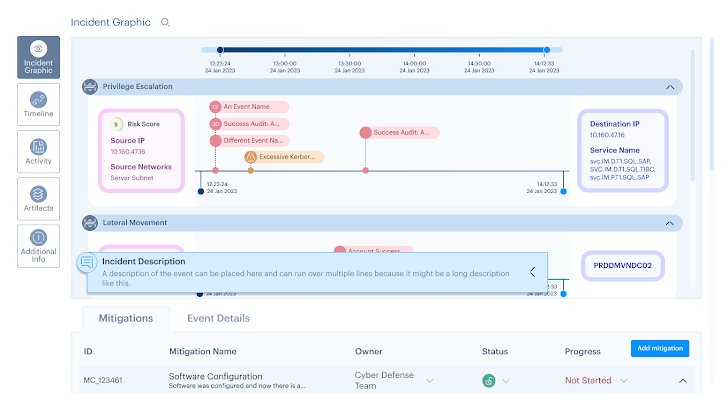 Determine 1: Incident Graphic, SHQ Response System ©2024 SecurityHQ
Determine 1: Incident Graphic, SHQ Response System ©2024 SecurityHQ
The timeline operate also lets an analyst to look into the logic powering an alert or use circumstance induce. This is demonstrated with the relevant Indicators of Compromise (IoCs), which can be quickly blocked making use of back again-conclusion built-in instruments.
Incident Response System for Senior Stakeholders
Overcome analysts swamped by bogus positives is endemic. Head of Worldwide SOC functions at SecurityHQ, Deodatta Wandhekar, put it greatest by explaining that:
‘Sixty per cent of SOC Incidents are repeat findings that maintain re-surfacing because of to underlying unmitigated pitfalls. The actors could be different nevertheless, the risk is primarily the same. This is producing substantial alert fatigue.’
Just one will have to take into account how to bridge this hole, with equally a apparent emphasis on company goals and risk urge for food, though retaining a amount of complex depth.
Risk Register for Collaboration & Tactic
SecurityHQ’s constructed-in Risk Sign-up enables analysts and small business leaders to operate jointly to push mitigation routines, using the technical acumen of operational personnel to inform strategic company conclusions.
This enables analysts to participate in a role in steering a cybersecurity software. By obtaining a degree of technical possession, a a lot more collaborative tactic is fostered between operational analysts and management workers. It also will allow after-overworked analysts to evidently see the fruits of their labor mirrored in wider organization procedures.
Up coming Measures
SecurityHQ as equally a consultative companion, and as the operator of these types of a system, contributes to creating a superior connection concerning management and analysts by delivering an intuitive, and govt-friendly, risk sign up.
From in this article, the concentration on proactive ways and roadmaps about merely ‘firefighting’ and closing incidents inside of a Provider Stage Agreement (SLA) generates the possibility for significant transform in a corporation.
For a lot more information and facts, talk to an pro listed here. If you suspect a security incident, report an incident in this article.
Observe: This posting was expertly penned by Tim Chambers, Senior Cyber Security Manager at SecurityHQ
Located this report fascinating? This article is a contributed piece from a person of our valued partners. Comply with us on Twitter and LinkedIn to browse more distinctive written content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Severe Vulnerabilities in Cinterion Cellular Modems Pose Risks to Various Industries
Severe Vulnerabilities in Cinterion Cellular Modems Pose Risks to Various Industries