Spoiler Warn: Companies with 10,000 SaaS people that use M365 and Google Workspace normal above 4,371 further linked applications.
SaaS-to-SaaS (3rd-occasion) application installations are escalating nonstop at companies close to the entire world. When an employee demands an added app to raise their efficiency or productivity, they seldom feel 2 times just before setting up. Most staff members do not even recognize that this SaaS-to-SaaS connectivity, which demands scopes like the capability to browse, update, create, and delete information, increases their organization’s attack surface area in a substantial way.
Third-occasion app connections ordinarily just take location exterior the check out of the security team, are not vetted to have an understanding of the degree of risk they pose.
Adaptive Shield’s newest report, Uncovering the Risks & Realities of Third-Party Linked Apps, dives into the data on this topic. It assessments the ordinary quantity of SaaS-to-SaaS applications companies have, and the amount of risk they existing. Here are the prime 5 findings.
Discovering #1: Linked Apps Operate Deep
The report focuses on Google Workspace and Microsoft 365 (M365), as it paints a apparent image of the scope of applications that are integrating with the two applications.
On normal, a corporation with 10,000 SaaS consumers making use of M365 has 2,033 apps related to its suite of programs. Firms of that dimensions using Google Workspace have extra than three-instances the amount, averaging 6,710 connected applications.
Even scaled-down corporations aren’t immune. The report discovered that organizations employing M365 typical .2 apps per user, when those people making use of Google Workspace normal .6 purposes per consumer.
Acquiring #2: The More Workers, the Much more Apps
In distinction to most development curves, the analysis shows that the number of apps per user doesn’t degree off or plateau the moment achieving a critical mass of buyers. Relatively, the amount of applications continues to expand with the quantity of users.
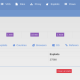
As witnessed in determine 1, firms working with Google Workspace with 10,000-20,000 employees ordinary virtually 14,000 special connected programs. This ongoing expansion is surprising to security groups, and helps make it nearly extremely hard for them to manually find out and take care of the substantial quantity of programs.
 Determine 1: Common variety of applications built-in with Google Workspace by customers
Determine 1: Common variety of applications built-in with Google Workspace by customers
For the full 2023 SaaS-to-SaaS Accessibility Report, click right here.
Locating #3: SaaS-to-SaaS Application Risk is Large
When third-celebration applications integrate with core SaaS applications, they attain entry utilizing an OAuth process. As part of this approach, purposes request unique scopes. These scopes hand more than a ton of electrical power to the apps.
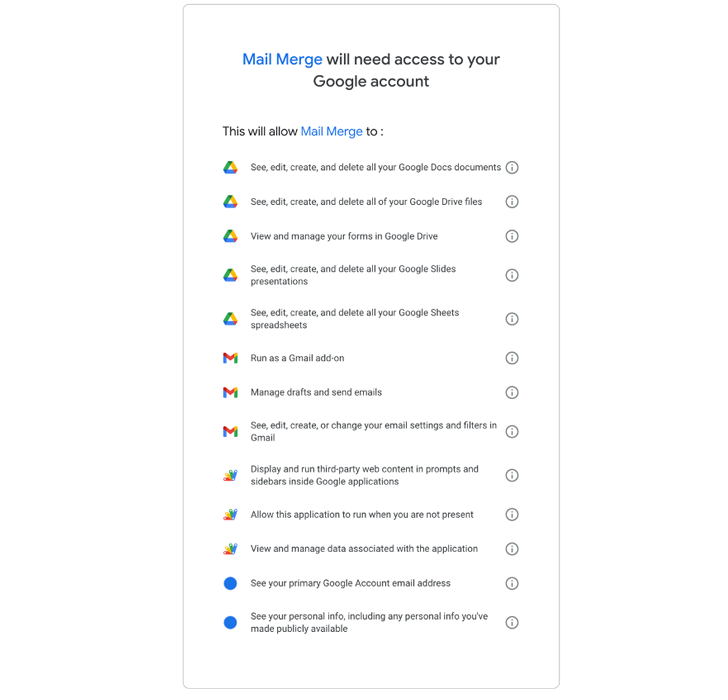
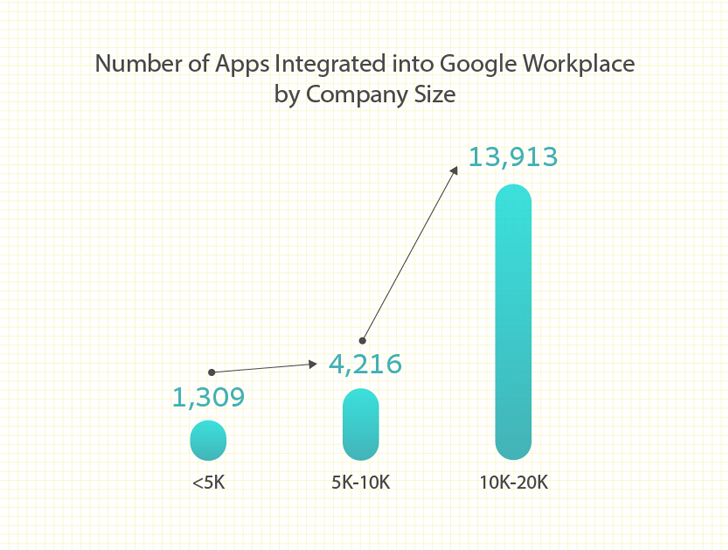
Amongst high-risk scopes, 15% of M365 purposes ask for the authority to delete all information that the user can access. It gets even scarier in Google Workspace programs, where by 40% of higher-risk scopes obtain the means to delete all Google Push files.
As shown in this permission tab, the software explicitly requests authorization to see, edit, make, and delete all Google Docs documents, Google Generate documents, Google Slides presentations, and Google Sheets spreadsheets.
For security groups accustomed to controlling the knowledge, authorization sets like these are unsettling. Contemplating that numerous programs are produced by personal developers who might not have prioritized security in their computer software development, these permissions provide risk actors with anything they want to obtain and steal or encrypt corporation knowledge. Even devoid of a danger actor, a bug in the software program can have disastrous repercussions for a firm’s data.
Figure 2: Higher-Risk Authorization Ask for from a third-occasion application
Acquiring #4: Linked Apps Also Have Tremendous Breadth
Although the report deep dives into the big two SaaS apps, it does also release investigation into Salesforce (and Slack). Salesforce averages 41 built-in apps per instance. The implication of this is noteworthy.
Salesforce is mostly applied by a little subset of the firm. In that regard, it can be comparable to Workday, Github, and ServiceNow, which are used by HR, builders, and finance teams. A usual firm with 10,000 workforce has above 350 SaaS apps in its stack, a lot of of which are made use of by lesser departments like the applications mentioned in this article.
Assuming Salesforce is normal of related programs, all those 350 apps integrating with 40 applications each individual provides an further 14,000 third-bash applications into the equation.
Getting #5: M365 and Google Workspace Have Similar Number of Substantial-Risk Apps
A single of the extra attention-grabbing takeaways was the superior volume of substantial-risk applications connecting to Microsoft as opposed to Google Workspace. Applications ask for significant-risk permissions from M365 39% of the time Google Workspace applications only request superior-risk permissions 11% of the time. In conditions of authentic figures, an typical set up in a enterprise with 10,000 SaaS end users making use of M365 will have 813 significant-risk apps, even though Google Workspace will have 738 apps that are regarded as superior-risk.
In all probability, this disparity is induced thanks to the app creation procedure. Google calls for apps requesting large-risk (it calls them Restrictive) permissions to be reviewed. The critique method is considerably less difficult for those requesting medium, or sensitive, permissions. Microsoft does not label requested scopes with severity levels. This deficiency of oversight would make it significantly easier for applications that join with M365 to request large-risk scopes.
SaaS Security is Much Far more Complicated than Most Understand
The total takeaway from looking at the report is the enormous problem of securing SaaS software. It really is apparent that security groups want visibility into the thousands of applications remaining connected to the SaaS stack, and make a expense-profit assessment for each individual significant-risk connected app.
SaaS security solutions, like Adaptive Shield, offer security teams with the visibility needed to see related apps and their scopes, among other critical SaaS security abilities. Armed with this information, security teams will be in a significantly better posture to harden their applications’ security posture and avert data from falling into the completely wrong hands.
Routine a demo to see how several SaaS-to-SaaS applications are linked to your SaaS Stack
Found this short article attention-grabbing? Stick to us on Twitter and LinkedIn to examine extra exceptional content we article.
Some parts of this article are sourced from:
thehackernews.com


 North Carolina Business Magnate Indicted in $2bn Fraud Case
North Carolina Business Magnate Indicted in $2bn Fraud Case