The menace actors powering ShellBot are leveraging IP addresses remodeled into its hexadecimal notation to infiltrate badly managed Linux SSH servers and deploy the DDoS malware.
“The in general stream remains the very same, but the obtain URL utilised by the risk actor to put in ShellBot has changed from a common IP handle to a hexadecimal worth,” the AhnLab Security Emergency response Center (ASEC) explained in a new report released now.
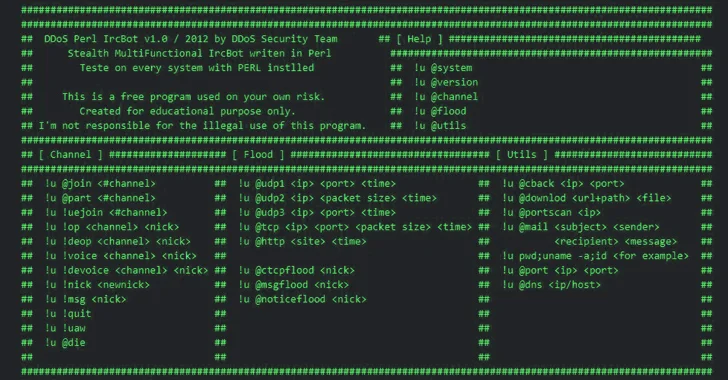
ShellBot, also recognised by the name PerlBot, is recognised to breach servers that have weak SSH qualifications by suggests of a dictionary attack, with the malware employed as a conduit to phase DDoS assaults and supply cryptocurrency miners.

Made in Perl, the malware uses the IRC protocol to converse with a command-and-management (C2) server.
The hottest set of noticed attacks involving ShellBot has been discovered to set up the malware making use of hexadecimal IP addresses – hxxp://0x2763da4e/ which corresponds to 39.99.218[.]78 – in what is actually seen as an attempt to evade URL-based detection signatures.
“Owing to the usage of curl for the obtain and its potential to help hexadecimal just like web browsers, ShellBot can be downloaded correctly on a Linux method surroundings and executed via Perl,” ASEC said.
The enhancement is a sign that ShellBot proceeds to witness regular use to launch attacks versus Linux devices.
With ShellBot capable of staying used to install extra malware or start diverse varieties of attacks from the compromised server, it can be encouraged that users swap to solid passwords and periodically improve them to resist brute-pressure and dictionary assaults.

The disclosure also comes as ASEC unveiled that attackers are weaponizing irregular certificates with unusually extensive strings for Subject Name and Issuer Title fields in a bid to distribute details stealer malware these kinds of as Lumma Stealer and a variant of RedLine Stealer recognised as RecordBreaker.
“These forms of malware are distributed by way of malicious pages that are simply available by means of look for engines (Search engine optimisation poisoning), posing a risk to a extensive selection of unspecified end users,” ASEC claimed. “These destructive pages principally use key terms linked to illegal plans this sort of as serials, keygens, and cracks.”
Located this write-up intriguing? Observe us on Twitter and LinkedIn to study more exceptional written content we publish.
Some parts of this article are sourced from:
thehackernews.com

 How to Guard Your Data from Exposure in ChatGPT
How to Guard Your Data from Exposure in ChatGPT