High-profile federal government entities in Southeast Asia are the target of a cyber espionage marketing campaign undertaken by a Chinese danger actor regarded as Sharp Panda considering that late final calendar year.
The intrusions are characterised by the use of a new variation of the Soul modular framework, marking a departure from the group’s attack chains observed in 2021.
Israeli cybersecurity business Test Point claimed the “lengthy-functioning” things to do have historically singled out international locations these types of as Vietnam, Thailand, and Indonesia. Sharp Panda was to start with documented by the business in June 2021, describing it as a “very-arranged operation that positioned considerable effort and hard work into remaining less than the radar.”
Apparently, the use of the Soul backdoor was comprehensive by Broadcom’s Symantec in Oct 2021 in connection to an unattributed espionage operation concentrating on protection, health care, and ICT sectors in Southeast Asia.
The implant’s origins, according to research printed by Fortinet FortiGuard Labs in February 2022, date as far back as Oct 2017, with the malware repurposing code from Gh0st RAT and other publicly out there equipment.
The attack chain in-depth by Test Stage starts with a spear-phishing email containing a lure document that leverages the Royal Highway Wealthy Textual content Structure (RTF) weaponizer to fall a downloader by exploiting one particular of a number of vulnerabilities in the Microsoft Equation Editor.
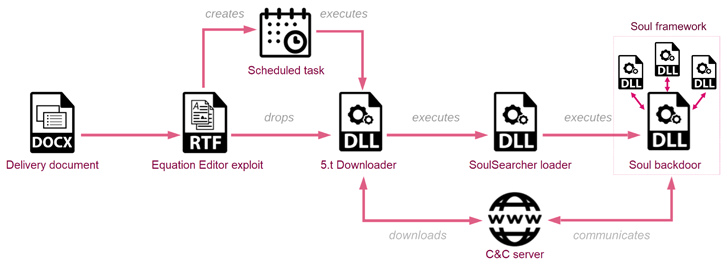
The downloader, in convert, is created to retrieve a loader recognised as SoulSearcher from a geofenced command-and-manage (C&C) server that only responds to requests originating from IP addresses corresponding to the qualified international locations.
The loader is then accountable for downloading, decrypting, and executing the Soul backdoor and its other factors, thus enabling the adversary to harvest a extensive array of info.
“The Soul key module is dependable for speaking with the C&C server and its major intent is to obtain and load in memory further modules,” Check out Point stated.
Find the Hottest Malware Evasion Practices and Avoidance Strategies
Prepared to bust the 9 most perilous myths about file-centered assaults? Be a part of our forthcoming webinar and turn out to be a hero in the struggle against individual zero bacterial infections and zero-day security events!
RESERVE YOUR SEAT
“Apparently, the backdoor configuration incorporates a ‘radio silence’-like characteristic, the place the actors can specify specific hrs in a 7 days when the backdoor is not permitted to communicate with the C&C server.”
The findings are still a further sign of the device sharing that is common among Chinese advanced persistent danger (APT) groups to aid intelligence collecting.
“Whilst the Soul framework has been in use given that at least 2017, the menace actors behind it have been frequently updating and refining its architecture and capabilities,” the company reported.
It further more observed that the marketing campaign is most likely “staged by state-of-the-art Chinese-backed danger actors, whose other equipment, capabilities and place within just the broader network of espionage actions are however to be explored.”
Discovered this write-up appealing? Stick to us on Twitter and LinkedIn to read through much more distinctive content we publish.
Some parts of this article are sourced from:
thehackernews.com


 CISA’s KEV Catalog Updated with 3 New Flaws Threatening IT Management Systems
CISA’s KEV Catalog Updated with 3 New Flaws Threatening IT Management Systems