This new item offers SaaS discovery and risk evaluation coupled with a free of charge consumer obtain critique in a distinctive “freemium” product
Securing employees’ SaaS utilization is turning out to be progressively essential for most cloud-based businesses. While several tools are accessible to deal with this have to have, they generally employ distinct approaches and systems, major to avoidable confusion and complexity. Enter Wing Security’s new “Critical SSPM” (SaaS Security Posture Management) tool, which aims to simplify the procedure of securing SaaS use across the firm. Its business enterprise approach is basic: self-onboard, test the product or service, and if amazed, up grade to unlock extra critical security abilities.
What is important SaaS security?
In accordance to Wing, 3 standard but essential abilities are necessary for companies aiming to secure their SaaS: discovery, evaluation, and management. These align with regulatory security requirements such as ISO 27001 and SOC, which emphasize seller and third-celebration risk assessment courses, as perfectly as controlling person obtain to critical small business instruments.
1. Uncover: You can’t secure what you won’t be able to see
Shadow IT is not a novel issue but rather an evolving 1. With the constant raise in SaaS utilization and the capability for people to bypass security guidelines like MFA and SSO when onboarding SaaS programs, the new confront of shadow IT is SaaS-primarily based. The process is simple: staff need to have to total a enterprise process and often demand a device to aid it. They lookup for a resolution on the internet, using firm credentials to log in, especially when most products and services will not involve credit rating card data to get commenced. SaaS, remaining the present day provide chain, clearly requires a security option due to its decentralized and ungoverned nature.
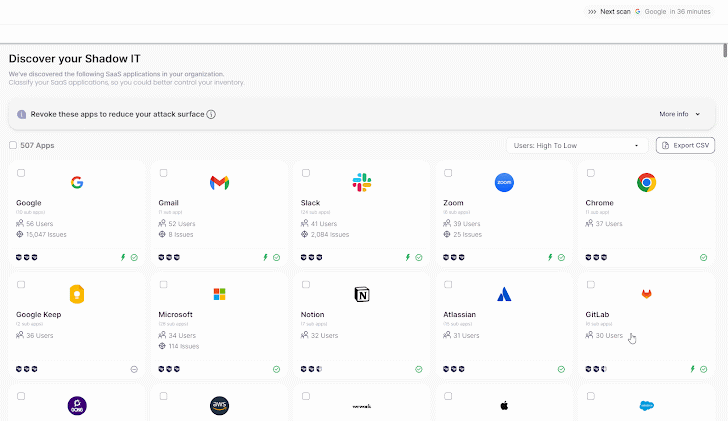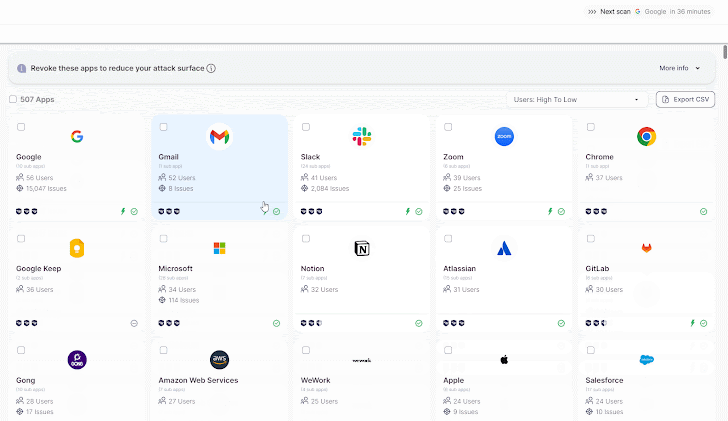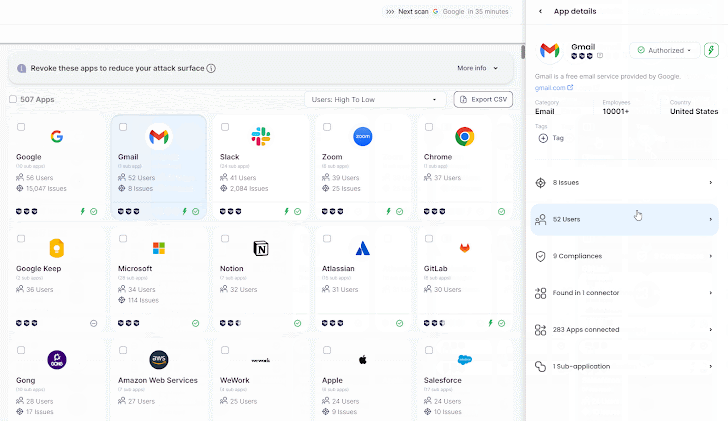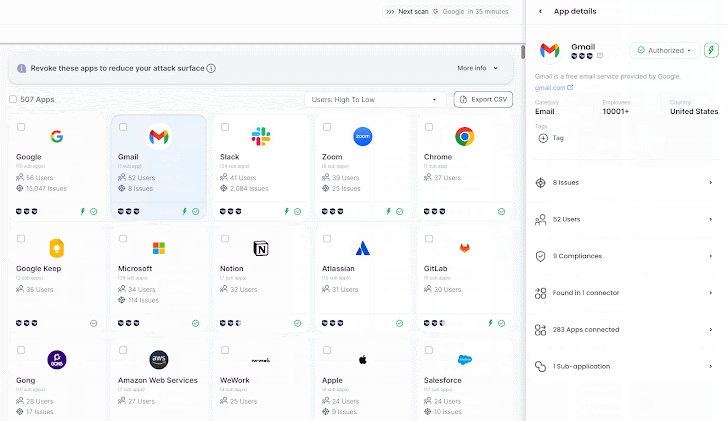 Wing’s SaaS discovery
Wing’s SaaS discovery
2. Assess risk: Not all pitfalls are equal, conserve precious time
The moment the shadow element is solved, companies are left with an in depth list of programs, normally numbering in the hundreds. This begs the question: what now? Without having an automatic process for assessing the dangers associated with all the SaaS applications joined to the firm, uncovering shadow SaaS can be much more bewildering and burdensome than valuable. This highlights the great importance of assessing the security position of these programs and determining a threshold that needs interest.
SaaS discovery need to go hand in hand with some diploma of seller or third-social gathering risk evaluation. Wing’s new products tier combines SaaS discovery with an automated processes for pinpointing an application’s SaaS security score. This risk info is extracted from a large SaaS databases of around 280,000 SaaS on report, cross-checked with the facts from hundreds of Wing’s consumers and their SaaS environments. Paying shoppers reward from broader and deeper SaaS risk assessments, such as in close proximity to-true-time danger intelligence alerts.
3. Regulate: Ensure people only have necessary accessibility
Exploring all SaaS in use (and not in use) and comprehending their challenges is only 50 percent the fight the other 50 percent includes SaaS customers. They grant purposes accessibility and permissions to organization data, making decisions concerning read/create permissions for the numerous programs they use. On typical, every employee utilizes 28 SaaS applications at any presented time, which translates to hundreds, if not hundreds, of SaaS applications with access to business details.
Conducting periodic consumer access critiques across vital enterprise purposes is not just a regulatory requirement but also highly recommended for retaining a safe posture. Controlling who has access to which application can avert sensitive info from slipping into the completely wrong hands and appreciably lower the opportunity attack area, as employees are normally the initial targets for destructive actors. A extended list of consumers and their permissions and roles throughout different purposes can be frustrating, which is why Wing aids in prioritizing users based mostly on their permissions, their roles and by encouraging the the very least privilege concept. This ensures that all customers, other than authorised admins, have only standard accessibility to SaaS purposes.
 Wing’s Person Access Assessment
Wing’s Person Access Assessment
In summary – These three capabilities are crucial for starting a proper SaaS security program, but they don’t ensure entire protection or control. Mature security organizations will call for extra. Data security attributes, automated remediation paths and far more management about person privileges and behaviors are only probable with Wing’s whole answer. That claimed, these are an important starting up level for people businesses who don’t however have SaaS security in location or are thinking about which tools and ways to get started off with.
How is this different from a POC or interactive demo?
This new “test initial, spend later on” strategy differs from the regular POC mainly in its wholly no-contact mother nature. Buyers can self-onboard the solution by agreeing to Wing’s legal circumstances, devoid of the have to have to interact with a human representative or gross sales personnel, unless they decide on to. When the free item is deliberately constrained in features and capabilities, it supplies a beginning place for these curious about or seeking SaaS security. Contrary to on the web demos, this process involves the genuine processing of your facts and can truly improve your security posture by delivering visibility into your firm’s genuine SaaS utilization and by making it possible for you to assess the magnitude of your SaaS attack floor. A freemium tactic in security-linked solutions is unheard of, producing this an possibility for all those who desire to exam the product just before committing.
Found this write-up intriguing? Abide by us on Twitter and LinkedIn to read through far more special written content we post.
Some parts of this article are sourced from:
thehackernews.com


 Iran’s MuddyWater Targets Israel in New Spear-Phishing Cyber Campaign
Iran’s MuddyWater Targets Israel in New Spear-Phishing Cyber Campaign