Cybersecurity scientists have unearthed a new impact operation concentrating on Ukraine that leverages spam emails to propagate war-linked disinformation.
The exercise has been joined to Russia-aligned danger actors by Slovak cybersecurity company ESET, which also discovered a spear-phishing marketing campaign aimed at a Ukrainian defense firm in October 2023 and a European Union agency in November 2023 with an intention to harvest Microsoft login qualifications utilizing pretend landing pages.
Operation Texonto, as the complete marketing campaign has been codenamed, has not been attributed to a specific threat actor, while some elements of it, especially the spear-phishing assaults, overlap with COLDRIVER, which has a heritage of harvesting qualifications through bogus sign-in internet pages.
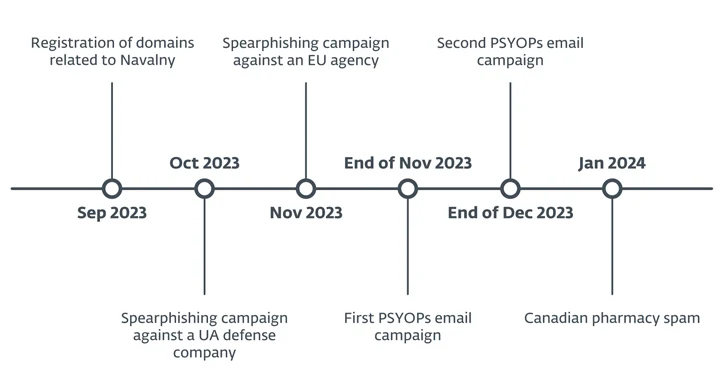
The disinformation operation took location in excess of two waves in November and December 2023, with the email messages bearing PDF attachments and material linked to heating interruptions, drug shortages, and food shortages.

The November wave specific no significantly less than a number of hundred recipients in Ukraine, such as the federal government, energy organizations, and men and women. It can be now not identified how the goal listing was made.
“What is interesting to notice is that the email was despatched from a domain masquerading as the Ministry of Agrarian Plan and Foods of Ukraine, while the written content is about drug shortages and the PDF is misusing the brand of the Ministry of Wellness of Ukraine,” ESET explained in a report shared with The Hacker News.
“It is quite possibly a error from the attackers or, at minimum, displays they did not care about all particulars.”
The next disinformation email campaign that commenced on December 25, 2023, is notable for growing its focusing on beyond Ukraine to include Ukrainian speakers in other European nations owing to the fact that all the messages are in Ukrainian.
These messages, whilst wishing recipients a joyful getaway period, also adopted a darker tone, likely as much as to suggest that they ampute just one of their arms or legs to steer clear of armed forces deployment. “A few of minutes of discomfort, but then a happy lifetime!,” the email goes.
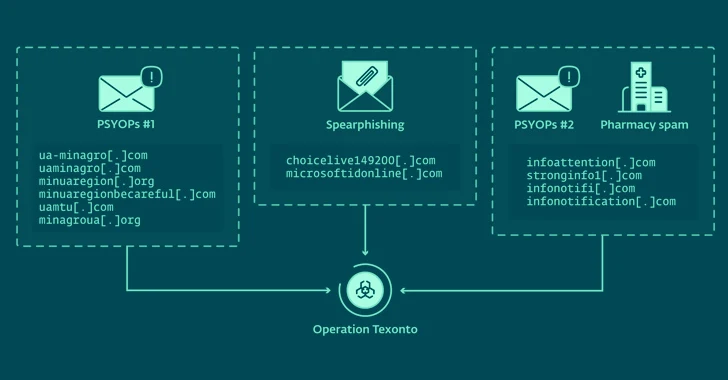
ESET reported one of the domains employed to propagate the phishing email messages in December 2023, infonotification[.]com, also engaged in sending hundreds of spam messages commencing January 7, 2024, redirecting possible victims to a fake Canadian pharmacy web-site.
It is exactly unclear why this email server was repurposed to propagate a pharmacy rip-off, but it really is suspected that the danger actors decided to monetize their infrastructure for monetary attain just after realizing that their domains have been detected by defenders.
“Operation Texonto displays but an additional use of technologies to try out to impact the war,” the company mentioned.

The development will come as Meta, in its quarterly Adversarial Danger Report, explained it took down a few networks throughout its platforms originating from China, Myanmar, and Ukraine that engaged in coordinated inauthentic habits (CIB).
Even though none of the networks ended up from Russia, social media analytics company Graphika claimed publishing volumes by Russian point out-controlled media has declined 55% from pre-war ranges and engagement has plummeted 94% as opposed to two decades back.
“Russian point out media stores have amplified their concentration on non-political infotainment articles and self-promotional narratives about Russia considering the fact that the start of the war,” it said. “This could replicate a broader off-system work to cater to domestic Russian audiences immediately after many Western international locations blocked the stores in 2022.”
Located this posting intriguing? Comply with us on Twitter and LinkedIn to study far more distinctive information we post.
Some parts of this article are sourced from:
thehackernews.com

 VMware Alert: Uninstall EAP Now – Critical Flaw Puts Active Directory at Risk
VMware Alert: Uninstall EAP Now – Critical Flaw Puts Active Directory at Risk