Russian risk actors have been quite possibly joined to what is been explained as the “biggest cyber attack in opposition to Danish critical infrastructure,” in which 22 corporations linked with the operation of the country’s electrical power sector have been qualified in May 2023.
“22 simultaneous, profitable cyberattacks against Danish critical infrastructure are not commonplace,” Denmark’s SektorCERT mentioned [PDF]. “The attackers knew in progress who they were being heading to focus on and obtained it ideal each and every time. Not the moment did a shot miss the target.”
The agency said it discovered evidence connecting 1 or additional assaults to Russia’s GRU navy intelligence agency, which is also tracked under the name Sandworm and has a observe record of orchestrating disruptive cyber assaults on industrial management programs. This assessment is based mostly on artifacts speaking with IP addresses that have been traced to the hacking crew.
The unparalleled and coordinated cyber attacks took location on May possibly 11 by exploiting CVE-2023-28771 (CVSS score: 9.8), a critical command injection flaw impacting Zyxel firewalls that was disclosed in late April 2023.

On the 11 companies that had been successfully infiltrated, the threat actors executed destructive code to perform reconnaissance of the firewall configurations and identify the following study course of motion.
“This sort of coordination necessitates preparing and means,” SektorCERT said in a specific timeline of activities. “The gain of attacking simultaneously is that the information and facts about one particular attack are not able to unfold to the other targets right before it is too late.”
“This places the electrical power of information sharing out of perform due to the fact no one particular can be warned in advance about the ongoing attack considering that anyone is attacked at the identical time. It is unusual – and exceptionally helpful.”
A 2nd wave of assaults targeting additional companies was subsequently recorded from May perhaps 22 to 25 by an attack group with earlier unseen cyber weapons, boosting the chance that two diverse risk actors were being concerned in the campaign.
That explained, it is really currently unclear if the teams collaborated with each individual other, labored for the similar employer, or were performing independently.
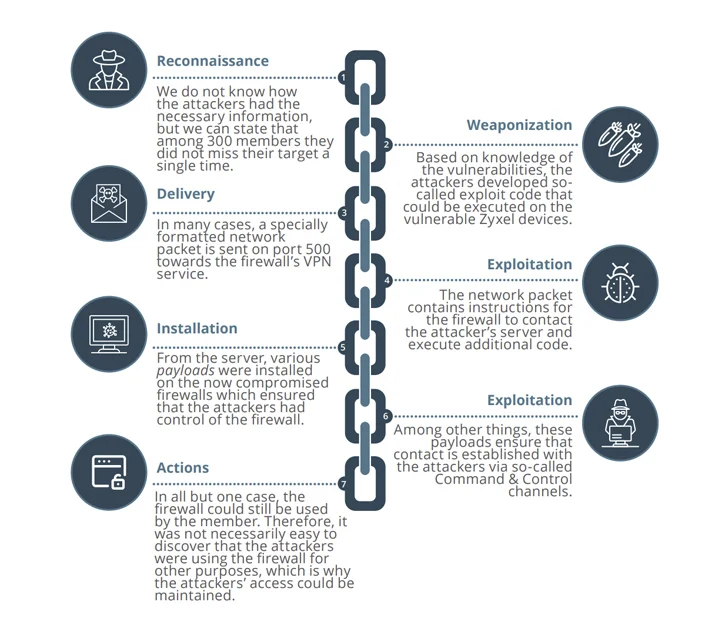
These attacks are suspected to have weaponized two more critical bugs in Zyxel equipment (CVE-2023-33009 and CVE-2023-33010, CVSS scores: 9.8) as zero-times to co-choose the firewalls into Mirai and MooBot botnets, specified that patches for them ended up launched by the corporation on Might 24, 2023.
The compromised gadgets, in some instances, ended up made use of to perform dispersed denial-of-provider (DDoS) assaults towards unnamed firms in the U.S. and Hong Kong.
“Immediately after the exploit code for some of the vulnerabilities became publicly recognised close to 30/5, attack attempts against the Danish critical infrastructure exploded – especially from IP addresses in Poland and Ukraine,” SektorCERT explained.
The onslaught of attacks prompted the affected entities to disconnect from the internet and go into island manner, the agency more included.

But it’s not only country-point out actors. The strength sector is also more and more becoming a concentration for ransomware groups, with first accessibility brokers (IABs) actively advertising unauthorized accessibility to nuclear electrical power companies, in accordance to a report from Resecurity earlier this 7 days.
The growth comes as Censys discovered 6 hosts belonging to NTC Vulkan, a Moscow-centered IT contractor that is alleged to have provided offensive cyber instruments to Russian intelligence agencies, such as Sandworm.
Moreover, the exploration uncovered a connection to a team called Raccoon Security by using an NTC Vulkan certificate.
“Racoon Security is a brand of NTC Vulkan and that it is probable that Raccoon Security’s actions include things like either former or current participation in the earlier-pointed out leaked initiatives contracted by the GRU,” Matt Lembright, director of Federal Programs at Censys, said.
Discovered this post attention-grabbing? Abide by us on Twitter and LinkedIn to browse more unique content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 U.S. Takes Down IPStorm Botnet, Russian-Moldovan Mastermind Pleads Guilty
U.S. Takes Down IPStorm Botnet, Russian-Moldovan Mastermind Pleads Guilty