The Russia-linked danger actor acknowledged as COLDRIVER has been observed evolving its tradecraft to go outside of credential harvesting to produce its 1st-at any time customized malware written in the Rust programming language.
Google’s Menace Investigation Team (TAG), which shared facts of the most recent exercise, mentioned the attack chains leverage PDFs as decoy paperwork to cause the infection sequence. The lures are sent from impersonation accounts.
COLDRIVER, also identified by the names Blue Callisto, BlueCharlie (or TAG-53), Calisto (alternately spelled Callisto), Gossamer Bear, Star Blizzard (formerly SEABORGIUM), TA446, and UNC4057, is regarded to be lively given that 2019, focusing on a large assortment of sectors.
This contains academia, protection, governmental corporations, NGOs, believe tanks, political outfits, and, just lately, defense-industrial targets and strength facilities.

“Targets in the U.K. and U.S. surface to have been most influenced by Star Blizzard activity, however action has also been noticed towards targets in other NATO countries, and nations around the world neighboring Russia,” the U.S. governing administration disclosed final month.
Spear-phishing campaigns mounted by the group are built to engage and develop belief with the potential victims with the greatest objective of sharing bogus indicator-in webpages in purchase to harvest their qualifications and attain access to the accounts.
Microsoft, in an examination of the COLDRIVER’s practices, identified as out its use of server-side scripts to prevent automatic scanning of the actor-controlled infrastructure and figure out targets of curiosity, in advance of redirecting them to the phishing landing pages.
The most current results from Google TAG exhibit that the menace actor has been employing benign PDF files as a beginning place as much back again as November 2022 to entice the targets into opening the files.
“COLDRIVER presents these files as a new op-ed or other type of posting that the impersonation account is wanting to publish, inquiring for suggestions from the goal,” the tech giant mentioned. “When the consumer opens the benign PDF, the textual content seems encrypted.”
In the event the recipient responds to the information stating they are not able to read the doc, the threat actor responds with a connection to a purported decryption resource (“Proton-decrypter.exe”) hosted on a cloud storage service.
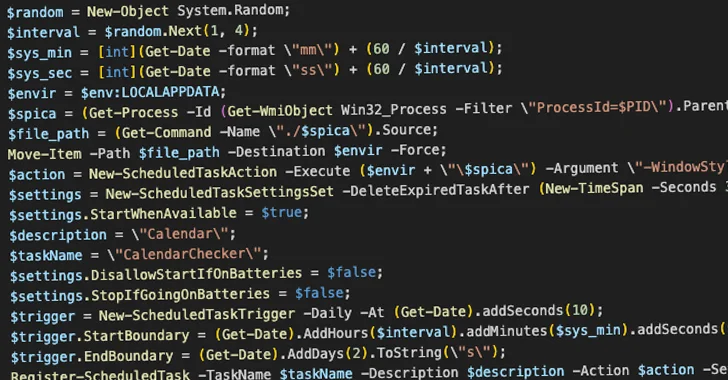
The alternative of the title “Proton-decrypter.exe” is notable because Microsoft had earlier disclosed that the adversary predominantly works by using Proton Travel to mail the PDF lures through the phishing messages.
In actuality, the decryptor is a backdoor named SPICA that grants COLDRIVER covert obtain to the device, while simultaneously exhibiting a decoy doc to keep up the ruse.
Prior results from WithSecure (formerly F-Secure) have unveiled the menace actor’s use of a lightweight backdoor referred to as Scout, a malware instrument from the HackingTeam Distant Manage System (RCS) Galileo hacking system, as aspect of phishing strategies observed in early 2016.
Scout is “supposed to be made use of as an initial reconnaissance device to assemble standard system information and screenshots from a compromised laptop, as perfectly as help the installation of more malware,” the Finnish cybersecurity enterprise observed at the time.
SPICA, which is the 1st custom made malware created and made use of by COLDRIVER, takes advantage of JSON more than WebSockets for command-and-manage (C2), facilitating the execution of arbitrary shell commands, theft of cookies from web browsers, uploading and downloading data files, and enumerating and exfiltrating data files. Persistence is accomplished by usually means of a scheduled task.
“At the time executed, SPICA decodes an embedded PDF, writes it to disk, and opens it as a decoy for the consumer,” Google TAG claimed. “In the history, it establishes persistence and begins the main C2 loop, waiting around for commands to execute.”

There is proof to propose that the country-state actor’s use of the implant goes again to November 2022, with the cybersecurity arm a number of variants of the “encrypted” PDF lure, indicating that there could be distinctive variations of SPICA to to match the lure document despatched to targets.
As section of its initiatives to disrupt the marketing campaign and reduce more exploitation, Google TAG claimed it additional all recognised internet websites, domains, and files involved with the hacking crew to Protected Searching blocklists.
The enhancement comes about a month immediately after the U.K. and the U.S. governments sanctioned two Russian associates of COLDRIVER, Ruslan Aleksandrovich Peretyatko and Andrey Stanislavovich Korinets, for their involvement in conducting the spear-phishing operations.
French cybersecurity company Sekoia has considering that publicized hyperlinks between Korinets and known infrastructure made use of by the group, which contains dozens of phishing domains and many servers.
“Calisto contributes to Russian intelligence attempts to assistance Moscow’s strategic pursuits,” the company reported. “It appears to be that domain registration was one of [Korinets’] key skills, plausibly utilised by Russian intelligence, either right or by means of a contractor partnership.”
Uncovered this article exciting? Abide by us on Twitter and LinkedIn to examine additional unique content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 TensorFlow CI/CD Flaw Exposed Supply Chain to Poisoning Attacks
TensorFlow CI/CD Flaw Exposed Supply Chain to Poisoning Attacks