Cybersecurity scientists have in-depth the techniques of a “rising” cybercriminal gang named “Examine The Handbook” (RTM) Locker that capabilities as a private ransomware-as-a-assistance (RaaS) provider and carries out opportunistic attacks to generate illicit earnings.
“The ‘Read The Manual’ Locker gang makes use of affiliate marketers to ransom victims, all of whom are compelled to abide by the gang’s rigorous policies,” cybersecurity company Trellix stated in a report shared with The Hacker Information.
“The business-like established up of the team, wherever affiliate marketers are needed to continue being lively or notify the gang of their leave, shows the organizational maturity of the group, as has also been noticed in other groups, such as Conti.”
RTM, initial documented by ESET in February 2017, begun off in 2015 as a banking malware focusing on organizations in Russia via push-by downloads, spam, and phishing e-mail. Attack chains mounted by the team have given that progressed to deploy a ransomware payload on compromised hosts.
In March 2021, the Russian-talking team was attributed to an extortion and blackmail campaign that deployed a trifecta of threats, like a fiscal trojan, legit remote accessibility equipment, and a ransomware pressure termed Quoter.
Trellix instructed The Hacker News that there is no marriage among Quoter and the RTM Locker ransomware executable utilised in the most up-to-date attacks.
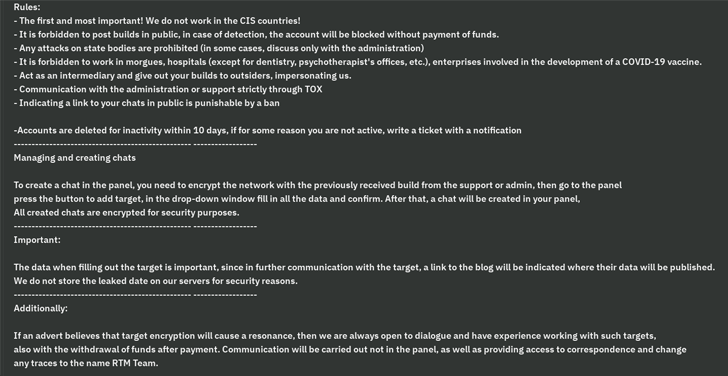
A vital trait of the menace actor is its capacity to function below the shadows by intentionally steering clear of superior-profile targets that could attract awareness to its things to do. To that end, CIS nations, as properly as morgues, hospitals, COVID-19 vaccine-linked firms, critical infrastructure, law enforcement, and other distinguished companies are off-limitations for the team.
“The RTM gang’s intention is to catch the attention of as tiny notice as attainable, which is wherever the rules support them to avoid hitting large-worth targets,” security researcher Max Kersten claimed. “Their administration of affiliate marketers to achieve that intention requires some stage of sophistication, however it is really not a higher level for every se.”
Approaching WEBINARMaster the Art of Dark Web Intelligence Accumulating
Find out the artwork of extracting danger intelligence from the dark web – Sign up for this professional-led webinar!
Help save My Seat!
RTM Locker malware builds are certain by demanding mandates that forbid affiliate marketers from leaking the samples, or else risk dealing with a ban. Amid the other policies laid out is a clause that locks out affiliate marketers must they keep on being inactive for 10 times sans a notification upfront.
“The work the gang place into avoiding drawing interest was the most abnormal,” Kersten defined. “The affiliates want to be energetic as very well, creating it more challenging for researchers to infiltrate the gang. All in all, the gang’s precise efforts in this region are better than normally observed in contrast to other ransomware groups.”
It is really suspected that the locker is executed on networks that are by now below the adversary’s regulate, indicating that the devices may possibly have been compromised by other means, these as phishing assaults, malspam, or the exploitation of internet-exposed susceptible servers.
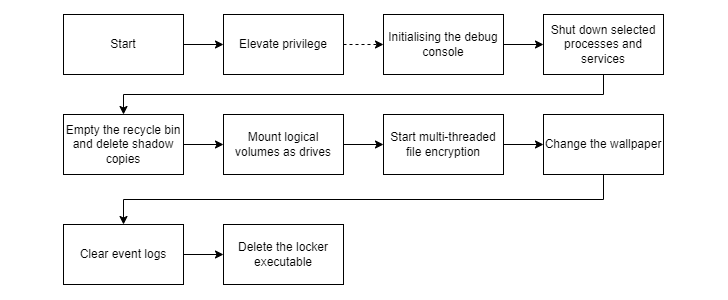
The risk actor, like other RaaS groups, makes use of extortion approaches to compel victims into paying out up. The payload, for its part, is able of elevating privileges, terminating antivirus and backup companies, and deleting shadow copies right before commencing its encryption procedure.
It’s also designed to empty the Recycle Bin to avert restoration, change the wallpaper, wipe event logs, and execute a shell command that self-deletes the locker as a last stage.
The results propose that cybercrime teams will carry on to “undertake new practices and procedures to keep away from the headlines and enable them fly under the radar of researchers and law enforcement alike,” Kersten pointed out.
Located this article fascinating? Follow us on Twitter and LinkedIn to study additional unique written content we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Pakistan-Aligned Hackers Disrupt Indian Education Sector
Pakistan-Aligned Hackers Disrupt Indian Education Sector