The innovative persistent threat (APT) actor recognised as SideWinder has been accused of deploying a backdoor in assaults directed in opposition to Pakistan authorities companies as element of a marketing campaign that commenced in late November 2022.
“In this campaign, the SideWinder innovative persistent risk (APT) team utilised a server-based polymorphism strategy to deliver the next phase payload,” the BlackBerry Study and Intelligence Crew stated in a specialized report posted Monday.
Yet another campaign found by the Canadian cybersecurity business in early March 2023 displays that Turkey has also landed in the crosshairs of the danger actor’s collection priorities.
SideWinder has been on the radar due to the fact at the very least 2012 and it is primarily identified to goal various Southeast Asian entities situated in Pakistan, Afghanistan, Bhutan, China, Myanmar, Nepal, and Sri Lanka.
Suspected to be an Indian condition-sponsored group, SideWinder is also tracked less than the monikers APT-C-17, APT-Q-39, Hardcore Nationalist (HN2), Rattlesnake, Razor Tiger, and T-APT4.

Common attack sequences mounted by the actor entail using carefully crafted email lures and DLL facet-loading techniques to fly under the radar and deploy malware capable of granting the actors remote accessibility to the qualified programs.
Above the previous yr, SideWinder has been connected to a cyber attack aimed at Pakistan Navy War School (PNWC) as properly as an Android malware marketing campaign that leveraged rogue phone cleaner and VPN applications uploaded to the Google Participate in Retailer to harvest delicate info.
The most recent infection chain documented by BlackBerry mirrors conclusions from Chinese cybersecurity agency QiAnXin in December 2022 detailing the use of PNWC entice documents to fall a light-weight .NET-dependent backdoor (Application.dll) which is able of retrieving and executing up coming-phase malware from a remote server.
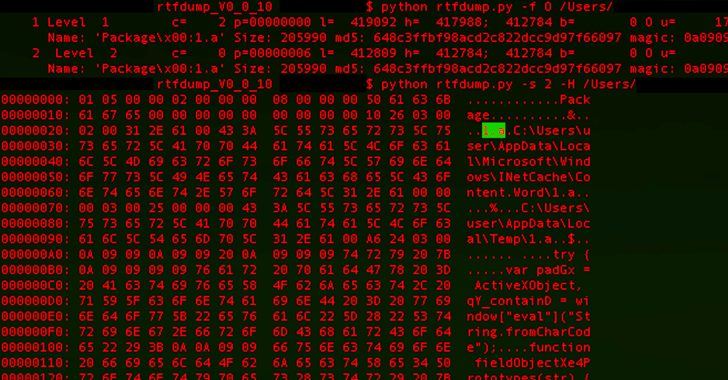
What tends to make the marketing campaign also stand out is the threat actor’s use of server-centered polymorphism as a way to possibly sidestep common signature-centered antivirus (AV) detection and distribute added payloads by responding with two different versions of an intermediate RTF file.
Specially, the PNWC doc employs a approach known as remote template injection to fetch the RTF file this kind of that it harbors the destructive code only if the ask for originates from a person in the Pakistan IP handle range.
“It is critical to be aware that in the two scenarios, only the identify of the file ‘file.rtf’ and the file type are the similar nonetheless, the contents, file measurement and the file hash are unique,” BlackBerry explained.
Impending WEBINARLearn to Quit Ransomware with Serious-Time Defense
Be part of our webinar and learn how to prevent ransomware assaults in their tracks with real-time MFA and company account safety.
Preserve My Seat!
“If the person is not in the Pakistani IP selection, the server returns an 8-byte RTF file (file.rtf) that incorporates a single string: rtf1 . However, if the person is inside the Pakistani IP range, the server then returns the RTF payload, which varies concerning 406 KB – 414 KB in size.”
The disclosure comes soon immediately after Fortinet and Group Cymru disclosed specifics of attacks perpetrated by a Pakistan-dependent threat actor recognised as SideCopy in opposition to Indian defense and military targets.
“The newest SideWinder campaign targeting Turkey overlaps with the most current developments in geopolitics particularly, in Turkey’s guidance of Pakistan and the ensuing response from India,” BlackBerry said.
Observed this article attention-grabbing? Stick to us on Twitter and LinkedIn to study a lot more exceptional articles we write-up.
Some parts of this article are sourced from:
thehackernews.com

 CISOs Worried About Personal Liability For Breaches
CISOs Worried About Personal Liability For Breaches