Substantial-profile federal government and telecom entities in Asia have been focused as aspect of an ongoing marketing campaign considering that 2021 that’s made to deploy simple backdoors and loaders for providing up coming-stage malware.
Cybersecurity company Verify Issue is monitoring the activity beneath the title Stayin’ Alive. Targets include things like organizations found in Vietnam, Uzbekistan, Pakistan, and Kazakhstan.
“The simplistic character of the equipment […] and their extensive variation suggests they are disposable, mostly utilized to download and operate further payloads,” it reported in a report posted Wednesday. “These resources share no apparent code overlaps with merchandise created by any recognized actors and do not have considerably in frequent with each and every other.”

What is notable about the campaign is that the infrastructure shares overlaps with that used by ToddyCat, a China-linked menace actor acknowledged for orchestrating cyber assaults towards govt and military services companies in Europe and Asia considering that at least December 2020.
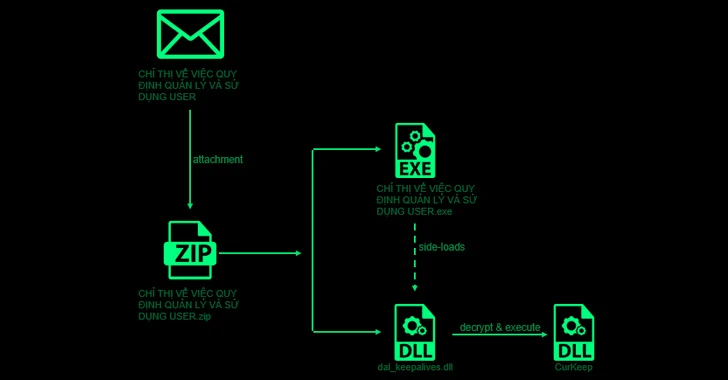
Attack chains start with a spear-phishing email that includes a ZIP file attachment with a authentic executable that leverages DLL aspect-loading to load a backdoor identified as CurKeep by usually means of a rogue DLL dal_keepalives.dll present in just the archive.
CurlKeep is designed to send information and facts about the compromised host to a remote server, execute commands sent by the server, and write server responses to a file on the program.
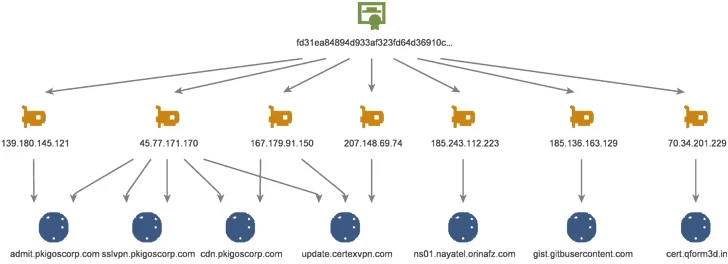
A closer examination of the command-and-manage (C2) infrastructure has exposed a regularly evolving arsenal of loader variants dubbed CurLu, CurCore, and CurLog that are able of obtaining DLL files, executing remote commands, and start a procedure associated with a freshly generated file to which data from the server is written to.

Also learned is a passive implant named StylerServ that listens on five unique ports (60810, 60811, 60812, 60813, and 60814) to acknowledge a distant link and acquire an encrypted configuration file.
While there is no conclusive proof to hook up Stayin’ Alive to ToddyCat, the conclusions exhibit that both of those intrusion sets make use of the very same infrastructure to go soon after a equivalent set of targets.
“The use of disposable loaders and downloaders, as noticed in this campaign, is getting to be much more typical even among the advanced actors,” it reported. “The use of disposable instruments would make each detection and attribution attempts far more complicated, as they are changed typically, and probably composed from scratch.”
Discovered this short article exciting? Follow us on Twitter and LinkedIn to study far more exceptional written content we publish.
Some parts of this article are sourced from:
thehackernews.com

 Two High-Risk Security Flaws Discovered in Curl Library – New Patches Released
Two High-Risk Security Flaws Discovered in Curl Library – New Patches Released