A recent marketing campaign carried out by Earth Preta indicates that country-state teams aligned with China are getting ever more proficient at bypassing security answers.
The danger actor, active because at least 2012, is tracked by the broader cybersecurity community underneath Bronze President, HoneyMyte, Mustang Panda, RedDelta, and Red Lich.
Attack chains mounted by the group begin with a spear-phishing email to deploy a wide assortment of tools for backdoor obtain, command-and-manage (C2), and details exfiltration.
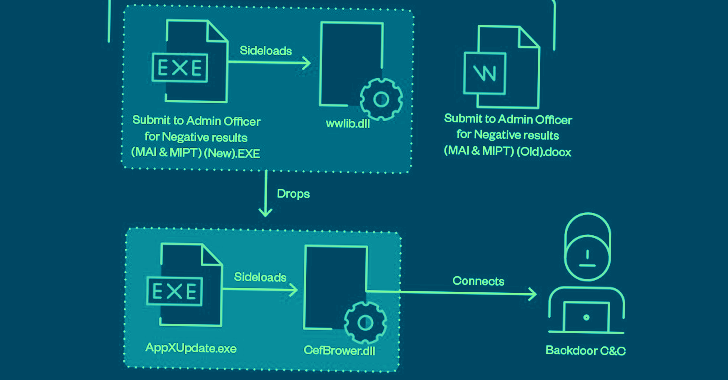
These messages arrive bearing with malicious lure archives distributed by means of Dropbox or Google Travel back links that employ DLL side-loading, LNK shortcut documents, and bogus file extensions as arrival vectors to receive a foothold and fall backdoors like TONEINS, TONESHELL, PUBLOAD, and MQsTTang (aka QMAGENT).
Similar infection chains making use of Google Travel one-way links have been observed offering Cobalt Strike as early as April 2021.
“Earth Preta tends to disguise destructive payloads in bogus documents, disguising them as reputable kinds — a technique that has been confirmed helpful for averting detection,” Craze Micro said in a new evaluation printed Thursday.
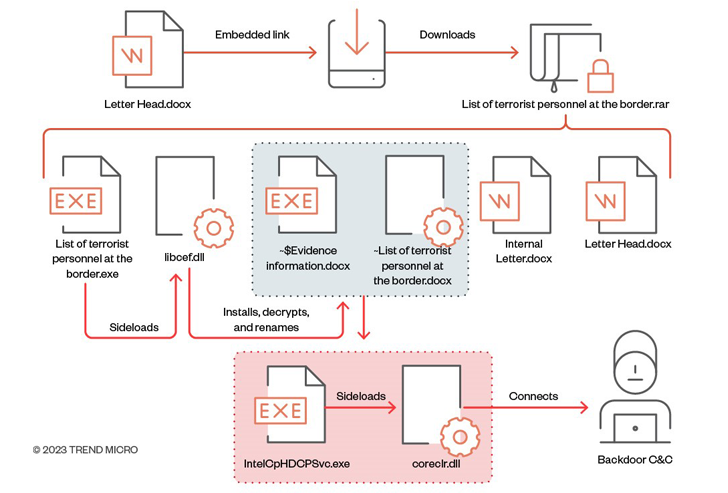
This entry position process, which was initial noticed late very last 12 months, has since acquired a slight tweak wherein the down load backlink to the archive is embedded inside an additional decoy doc and the file is password-safeguarded in an try to sidestep email gateway solutions.
“The files can then be extracted inside by means of the password furnished in the doc,” the scientists stated. “By employing this technique, the destructive actor powering the attack can effectively bypass scanning products and services.”
First access to the victim’s setting is adopted by account discovery and privilege escalation phases, with Mustang Panda leveraging personalized applications like ABPASS and CCPASS to circumvent User Account Command (UAC) in Windows 10.
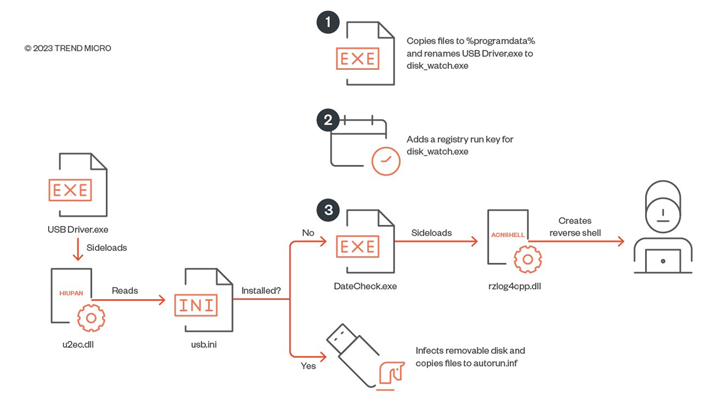
Additionally, the danger actor has been noticed deploying malware these kinds of as “USB Driver.exe” (HIUPAN or MISTCLOAK) and “rzlog4cpp.dll” (ACNSHELL or BLUEHAZE) to install on their own to detachable disks and build a reverse shell with the intention of laterally shifting throughout the network.
WEBINARDiscover the Concealed Dangers of Third-Bash SaaS Apps
Are you knowledgeable of the hazards linked with 3rd-occasion app obtain to your company’s SaaS applications? Sign up for our webinar to understand about the styles of permissions remaining granted and how to decrease risk.
RESERVE YOUR SEAT
Other utilities deployed consist of CLEXEC, a backdoor able of executing commands and clearing party logs COOLCLIENT and TROCLIENT, implants that are developed to history keystrokes as well as go through and delete documents and PlugX.
“Apart from nicely-identified authentic equipment, the menace actors also crafted hugely customized tools utilised for exfiltration,” the scientists mentioned. This comprises NUPAKAGE and ZPAKAGE, both of which are outfitted to obtain Microsoft Office data files.
The findings the moment yet again spotlight the greater operational tempo of Chinese cyber espionage actors and their constant investment decision in advancing their cyber weaponry to evade detection.
“Earth Preta is a able and structured menace actor that is repeatedly honing its TTPs, strengthening its progress abilities, and constructing a versatile arsenal of tools and malware,” the scientists concluded.
Observed this posting appealing? Abide by us on Twitter and LinkedIn to read through additional exceptional written content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Fifth of Execs Admit Security Flaws Cost Them New Biz
Fifth of Execs Admit Security Flaws Cost Them New Biz