The Chinese threat actor acknowledged as APT31 (aka Bronze Vinewood, Judgement Panda, or Violet Storm) has been connected to a established of state-of-the-art backdoors that are capable of exfiltrating harvested delicate details to Dropbox.
The malware is part of a broader assortment of far more than 15 implants that have been place to use by the adversary in assaults focusing on industrial corporations in Eastern Europe in 2022.
“The attackers aimed to establish a permanent channel for details exfiltration, together with data saved on air-gapped systems,” Kaspersky mentioned in an assessment spotlighting APT31’s formerly undocumented tradecraft.

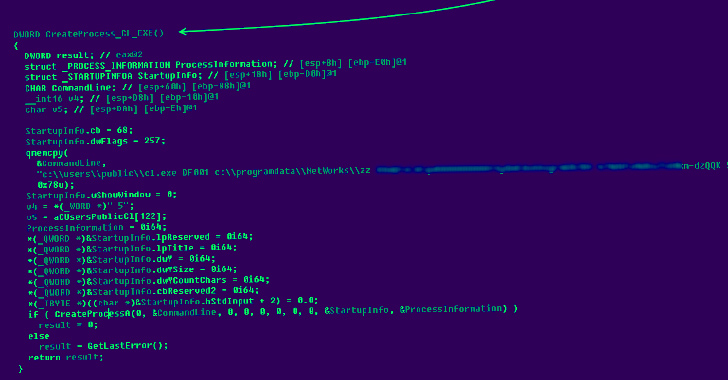
The intrusions make use of a three-phase malware stack, every targeted on disparate factors of the attack chain: setting up persistence, accumulating sensitive knowledge, and transmitting the information and facts to a distant server underneath the attackers’ regulate.
Some variants of the 2nd-phase backdoors also come with functions created to appear up file names in the Microsoft Outlook folder, execute distant instructions, and employ the 3rd-step part to finish the information exfiltration step in the kind of RAR archive data files.
“The first step is used for persistence, the deployment and startup of the second-action malware module, which is accountable for uploading the information gathered to the server by contacting the 3rd-action implant and cleaning up,” the Russian cybersecurity organization mentioned.
In what is actually a novel twist, APT31 is mentioned to have utilized a command-and-regulate (C2) within the corporate perimeter and leveraged it as a proxy to siphon knowledge from units that lacked direct access to the internet, indicating apparent makes an attempt to solitary out air-gapped hosts.

Kaspersky explained it also spotted further instruments employed by the attacker to manually upload the information to Yandex Disk and other momentary file-sharing companies this sort of as extraimage, imgbb, imgshare, schollz, and zippyimage, amid many others. A third similar implant is configured to mail the details by using the Yandex email support.
The results spotlight the meticulous planning and the potential of the menace actor to adapt and spin up new abilities in their cyber espionage pursuits.
“Abusing well-known cloud-based mostly data storages could enable the danger actor(s) to evade security steps,” the corporation said. “At the same time, it opens up the possibility for stolen data to be leaked a next time in the function that a 3rd occasion gets obtain to a storage utilized by the risk actor(s).”
Identified this report attention-grabbing? Abide by us on Twitter and LinkedIn to read additional special content material we publish.
Some parts of this article are sourced from:
thehackernews.com

 New SystemBC Malware Variant Targets South African Power Company
New SystemBC Malware Variant Targets South African Power Company