A risk actor regarded as Prolific Puma has been keeping a low profile and working an underground website link shortening services that is provided to other danger actors for at least over the previous four a long time.
Prolific Puma results in “domain names with an RDGA [registered domain generation algorithm] and use these domains to give a website link shortening assistance to other destructive actors, encouraging them evade detection whilst they distribute phishing, ripoffs, and malware,” Infoblox said in a new evaluation pieced with each other from Domain Name Procedure (DNS) analytics.
With destructive actors identified to use connection shorteners for phishing assaults, the adversary performs an crucial job in the cybercrime offer chain, registering between 35,000 to 75,000 special domain names since April 2022. Prolific Puma is also a DNS threat actor for leveraging DNS infrastructure for nefarious applications.
A noteworthy aspect of the threat actor’s operations is the use of an American domain registrar and web hosting corporation named NameSilo for registration and title servers due to its affordability and an API that facilitates bulk registration.

Prolific Puma, which does not publicize its shortening services on underground markets, has also been observed resorting to strategic growing older to park registered domains for quite a few months prior to hosting their company with nameless providers.
“Prolific Puma domains are alphanumeric, pseudo-random, with variable size, commonly 3 or 4 characters prolonged, but we have also observed SLD labels as very long as 7 figures,” Infoblox discussed.
Additionally, the danger actor has registered hundreds of domains in the U.S. prime-stage domain (usTLD) because May well 2023, repeatedly using an email address containing a reference to the tune OCT 33 by a psychedelic soul band termed Black Pumas: blackpumaoct33@ukr[.]net.
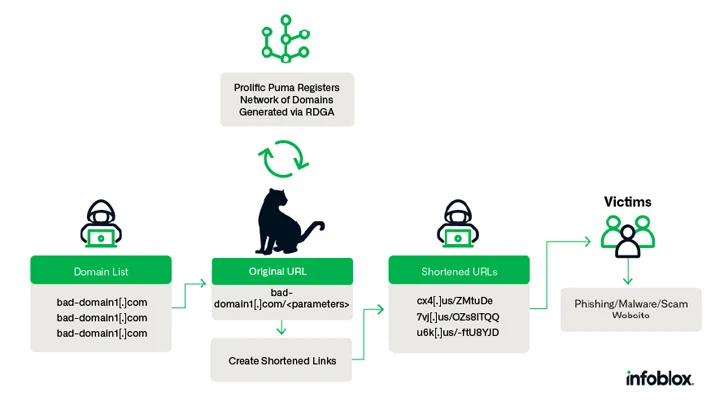
The real-planet id and origins of Prolific Puma remains unknown as nonetheless. That stated, a number of threat actors are said to be using the supplying to acquire people to phishing and scam sites, CAPTCHA difficulties, and even other shortened inbound links established by a different provider.
In a person instance of a phishing-cum-malware attack documented by Infoblox, victims clicking on a shortened url are taken to a landing page that requests them to supply personal particulars and make a payment, and in the long run infect their systems with browser plugin malware.
The disclosure comes weeks immediately after the organization exposed a further persistent DNS menace actor codenamed Open Tangle that leverages a big infrastructure of lookalike domains of legit financial institutions to target consumers for phishing and smishing assaults.
“Prolific Puma demonstrates how the DNS can be abused to assist legal activity and continue being undetected for several years,” it reported.
Kopeechka Hacking Resource Floods On the web Platforms with Bogus Accounts
The growth also follows a new report from Craze Micro, which identified that lesser-qualified cybercriminals are employing a new software referred to as Kopeechka (indicating “penny” in Russian) to automate the creation of hundreds of bogus social media accounts in just a couple seconds.
“The provider has been lively considering that the commencing of 2019 and supplies simple account registering solutions for well-known social media platforms, together with Instagram, Telegram, Facebook, and X (previously Twitter),” security researcher Cedric Pernet claimed.
Kopeechka presents two kinds of distinct email addresses to enable with the mass-registration course of action: email addresses hosted in 39 domains owned by the danger actor and those that are hosted on far more well-known email hosting expert services these types of as Gmail, Hotmail, Outlook, Rambler, and Zoho Mail.

“Kopeechka does not basically provide obtain to the true mailboxes,” Pernet discussed. “When end users ask for for mailboxes to make social media accounts, they only get the email handle reference and the certain email that contains the confirmation code or URL.”
It is really suspected that these email addresses are possibly compromised or produced by the Kopeechka actors by themselves.
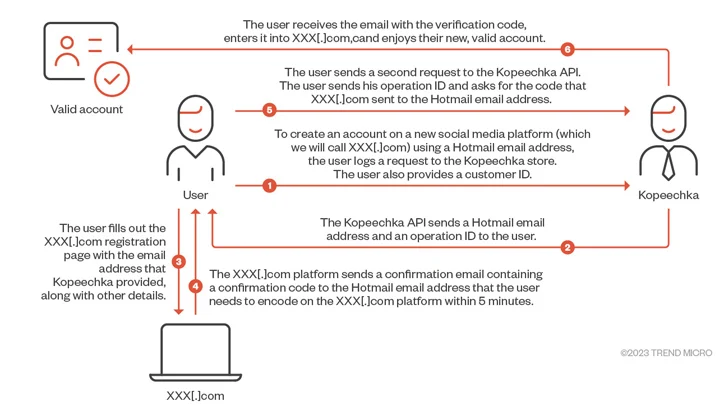
With on line services incorporating phone quantity verification to finish registration, Kopeechka allows its buyers to opt for from 16 various on line SMS companies, most of which originate from Russia.
In addition to accelerating cybercrime and equipping menace actors to start full-fledged functions at scale, this sort of equipment – produced as part of the “as-a-support” small business model – highlight the professionalization of the felony ecosystem.
“Kopeechka’s expert services can facilitate an uncomplicated and cost-effective way to mass-create accounts online, which could be helpful to cybercriminals,” Pernet mentioned.
“Whilst Kopeechka is generally made use of for a number of accounts creation, it can also be made use of by cybercriminals who want to incorporate a diploma of anonymity to their actions, as they do not want to use any of their own email addresses to build accounts on social media platforms.”
Uncovered this write-up exciting? Follow us on Twitter and LinkedIn to go through additional exclusive written content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Hands on Review: LayerX’s Enterprise Browser Security Extension
Hands on Review: LayerX’s Enterprise Browser Security Extension