Menace actors are utilizing an open-resource rootkit termed Reptile to target Linux programs in South Korea.
“As opposed to other rootkit malware that ordinarily only supply concealment capabilities, Reptile goes a phase even more by giving a reverse shell, permitting threat actors to quickly get regulate of systems,” the AhnLab Security Emergency Reaction Middle (ASEC) explained in a report revealed this 7 days.
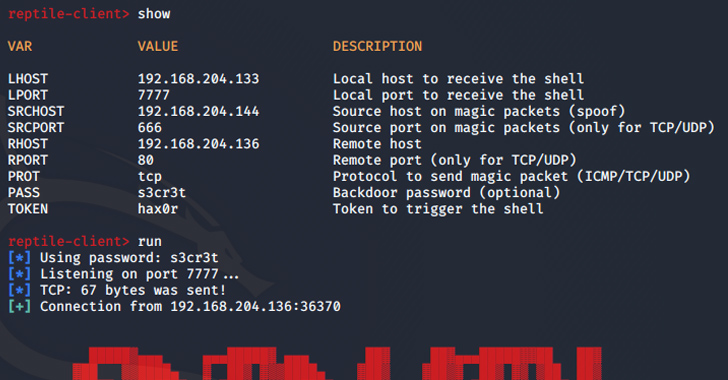
“Port knocking is a process exactly where the malware opens a certain port on an contaminated program and goes on standby. When the threat actor sends a magic packet to the program, the been given packet is employed as a foundation to create a connection with the C&C server.”
A rootkit is a destructive software package program that is made to present privileged, root-stage accessibility to a device even though concealing its presence. At minimum four different strategies have leveraged Reptile because 2022.

The to start with use of the rootkit was recorded by Trend Micro in Could 2022 in link with an intrusion established tracked as Earth Berberoka (aka GamblingPuppet), which has been identified to use the malware to hide connections and procedures relevant to a cross-platform Python trojan recognised as Pupy RAT in attacks aimed at gambling sites in China.
Then in March 2023, Google-owned Mandiant thorough a set of assaults mounted by a suspected China-linked menace actor dubbed UNC3886 that employed zero-day flaws in Fortinet appliances to deploy a amount of customized implants as well as Reptile.

ExaTrack, that identical month, exposed a Chinese hacking group’s use of a Linux malware known as Mélofée that is based on Reptile. Lastly, in June 2023, a cryptojacking operation identified by Microsoft utilized a shell script backdoor to download Reptile in purchase to obscure its little one procedures, data files, or their written content.
A nearer examination of Reptile reveals the use of a loader, which uses a resource named kmatryoshka to decrypt and load the rootkit’s kernel module into memory, just after which it opens a precise port and awaits for the attacker to transmit a magic packet to the host more than protocols such as TCP, UDP, or ICMP.

“The info received by means of the magic packet includes the C&C server deal with,” ASEC said. “Primarily based on this, a reverse shell connects to the C&C server.”
It is really truly worth noting that the use of magic packets to activate the destructive action has been noticed earlier in one more rootkit named Syslogk, which was documented by Avast very last year.
The South Korean cybersecurity company stated it also detected an attack situation in the state that included the use of Reptile, although bearing some tactical similarities to Mélofée.
“Reptile is a Linux kernel manner rootkit malware that gives a concealment aspect for information, directories, procedures, and network communications,” ASEC claimed. “Even so, Reptile by itself also offers a reverse shell, building units with Reptile set up susceptible to currently being hijacked by risk actors.”
Found this post fascinating? Abide by us on Twitter and LinkedIn to read more exclusive articles we publish.
Some parts of this article are sourced from:
thehackernews.com

 Microsoft Addresses Critical Power Platform Flaw After Delays and Criticism
Microsoft Addresses Critical Power Platform Flaw After Delays and Criticism