The distant entry trojan (RAT) identified as Remcos RAT has been observed getting propagated by means of webhards by disguising it as adult-themed game titles in South Korea.
WebHard, short for web hard drive, is a preferred on the net file storage method applied to add, down load, and share documents in the region.
When webhards have been used in the past to supply njRAT, UDP RAT, and DDoS botnet malware, the AhnLab Security Crisis Response Center’s (ASEC) most up-to-date evaluation exhibits that the procedure has been adopted to distribute Remcos RAT.

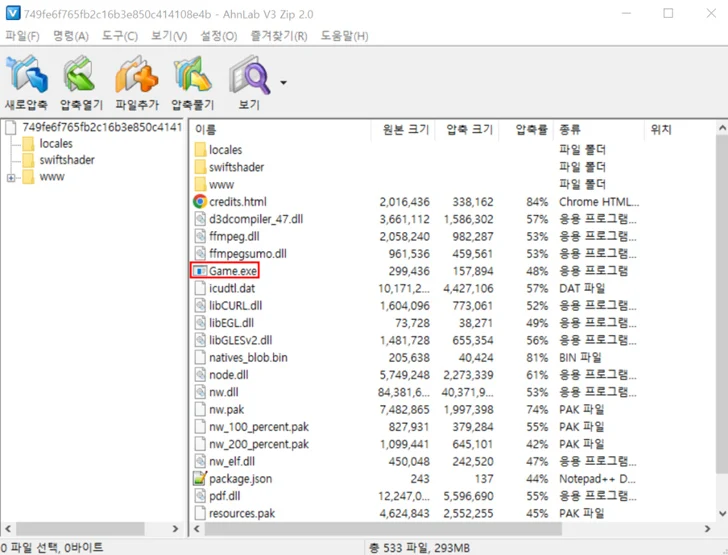
In these assaults, consumers are tricked into opening booby-trapped files by passing them off as grownup video games, which, when introduced, execute destructive Visible Primary scripts in get to operate an intermediate binary named “ffmpeg.exe.”
This success in the retrieval of Remcos RAT from an actor-managed server.
A subtle RAT, Remcos (aka Distant Control and Surveillance) facilitates unauthorized remote regulate and surveillance of compromised hosts, enabling threat actors to exfiltrate delicate information.
This malware, despite the fact that at first marketed by Germany-based firm Breaking Security in 2016 as a bonafide remote administration tool, has metamorphosed into a strong weapon wielded by adversaries actors to infiltrate systems and set up unfettered control.

“Remcos RAT has progressed into a malicious device used by risk actors throughout a variety of strategies,” Cyfirma noted in an analysis in August 2023.
“The malware’s multifunctional abilities, together with keylogging, audio recording, screenshot capture, and much more, emphasize its possible to compromise user privateness, exfiltrate sensitive information, and manipulate methods. The RAT’s capacity to disable User Account Control (UAC) and build persistence more amplifies its potential effect.”
Identified this posting attention-grabbing? Observe us on Twitter and LinkedIn to read through extra unique written content we article.
Some parts of this article are sourced from:
thehackernews.com


 Case Study: The Cookie Privacy Monster in Big Global Retail
Case Study: The Cookie Privacy Monster in Big Global Retail