Cloudflare on Thursday explained it mitigated 1000’s of hyper-volumetric HTTP distributed denial-of-provider (DDoS) assaults that exploited a recently disclosed flaw identified as HTTP/2 Speedy Reset, 89 of which exceeded 100 million requests for every 2nd (RPS).
“The marketing campaign contributed to an over-all enhance of 65% in HTTP DDoS attack website traffic in Q3 compared to the former quarter,” the web infrastructure and security business stated in a report shared with The Hacker Information. “In the same way, L3/4 DDoS assaults also amplified by 14%.”
The complete selection of HTTP DDoS attack requests in the quarter surged to 8.9 trillion, up from 5.4 trillion in Q2 2023 and 4.7 trillion in Q1 2023. The quantity of attack requests in Q4 2022 stood at 6.5 trillion.

HTTP/2 Immediate Reset (CVE-2023-44487) arrived to light-weight previously this month following an industry-wide coordinated disclosure that delved into DDoS attacks orchestrated by an not known actor by leveraging the flaw to target different suppliers these kinds of as Amazon Web Services (AWS), Cloudflare, and Google Cloud.
Fastly, in a disclosure of its have on Wednesday, stated it countered a comparable attack that peaked at a volume of about 250 million RPS and a length of about a few minutes.
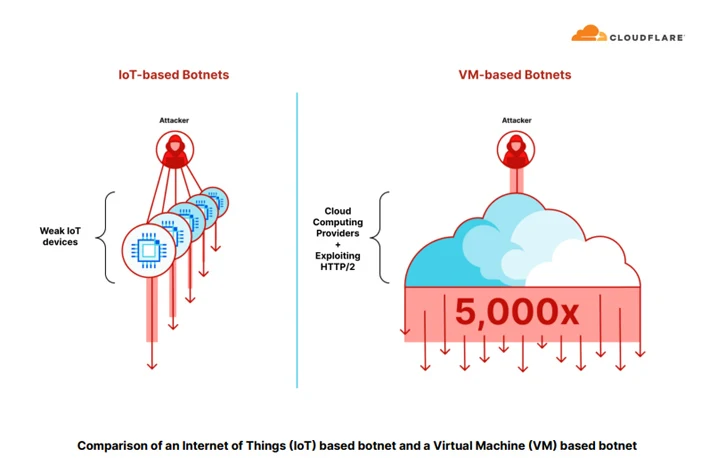

“Botnets that leverage cloud computing platforms and exploit HTTP/2 are ready to make up to x5,000 extra power for each botnet node,” Cloudflare observed. “This permitted them to launch hyper-volumetric DDoS assaults with a small botnet ranging 5-20 thousand nodes alone.”
Some of the major industries focused by HTTP DDoS assaults contain gaming, IT, cryptocurrency, laptop computer software, and telecom, with the U.S., China, Brazil, Germany, and Indonesia accounting for the largest resources of application layer (L7) DDoS assaults.
On the other hand, the U.S., Singapore, China, Vietnam, and Canada emerged as the most important targets of HTTP DDoS assaults.

“For the 2nd consecutive quarter, DNS-primarily based DDoS assaults were being the most typical,” the organization said. “Virtually 47% of all attacks have been DNS-based mostly. This signifies a 44% maximize compared to the former quarter. SYN floods keep on being in 2nd put, followed by RST floods, UDP floods, and Mirai assaults.”
An additional notable adjust is the lessen in ransom DDoS assaults, which Cloudflare reported “is for the reason that risk actors have understood that organizations will not spend them.”
The disclosure arrives amid internet site visitors fluctuations and a spike in DDoS assaults in the aftermath of the Israel-Hamas war, with Cloudflare repelling several attack makes an attempt aimed at Israeli and Palestinian internet sites.
Identified this write-up appealing? Adhere to us on Twitter and LinkedIn to read extra exclusive written content we publish.
Some parts of this article are sourced from:
thehackernews.com