The operators of Raspberry Robin are now using two new one particular-working day exploits to reach area privilege escalation, even as the malware carries on to be refined and improved to make it stealthier than ahead of.
This signifies that “Raspberry Robin has entry to an exploit vendor or its authors produce the exploits them selves in a small interval of time,” Check Position claimed in a report this 7 days.
Raspberry Robin (aka QNAP worm), initial documented in 2021, is an evasive malware family which is known to act as 1 of the best first access facilitators for other destructive payloads, which include ransomware.
Attributed to a risk actor named Storm-0856 (earlier DEV-0856), it is really propagated by using many entry vectors, including infected USB drives, with Microsoft describing it as component of a “complex and interconnected malware ecosystem” with ties to other e-crime teams like Evil Corp, Silence, and TA505.

Raspberry Robin’s use of one particular-day exploits this sort of as CVE-2020-1054 and CVE-2021-1732 for privilege escalation was beforehand highlighted by Test Issue in April 2023.
The cybersecurity organization, which detected “huge waves of assaults” considering the fact that October 2023, claimed the risk actors have applied added anti-assessment and obfuscation procedures to make it more difficult to detect and evaluate.
“Most importantly, Raspberry Robin proceeds to use unique exploits for vulnerabilities both right before or only a short time immediately after they had been publicly disclosed,” it pointed out.
“Those a single-day exploits ended up not publicly disclosed at the time of their use. An exploit for just one of the vulnerabilities, CVE-2023-36802, was also made use of in the wild as a zero-day and was bought on the dark web.”
A report from Cyfirma late very last 12 months exposed that an exploit for CVE-2023-36802 was getting advertised on dark web forums in February 2023. This was 7 months in advance of Microsoft and CISA unveiled an advisory on active exploitation. It was patched by the Windows maker in September 2023.
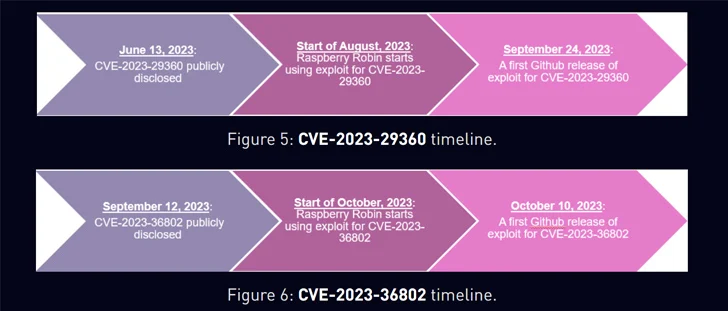
Raspberry Robin is stated to have begun employing an exploit for the flaw someday in Oct 2023, the exact same thirty day period a community exploit code was produced available, as properly as for CVE-2023-29360 in August. The latter was publicly disclosed in June 2023, but an exploit for the bug did not seem right until September 2023.

It can be assessed that the risk actors obtain these exploits somewhat than building them in-house owing to the fact that they are made use of as an exterior 64-little bit executable and are not as greatly obfuscated as the malware’s main module.
“Raspberry Robin’s capability to quickly integrate freshly disclosed exploits into its arsenal further demonstrates a sizeable menace stage, exploiting vulnerabilities ahead of several organizations have used patches,” the company stated.
One of the other major modifications worries the initial accessibility pathway by itself, leveraging rogue RAR archive documents containing Raspberry Robin samples that are hosted on Discord.
Also modified in the more recent variants is the lateral movement logic, which now makes use of PAExec.exe as an alternative of PsExec.exe, and the command-and-manage (C2) interaction method by randomly choosing a V3 onion deal with from a record of 60 hardcoded onion addresses.
“It commences with making an attempt to call genuine and perfectly-recognised Tor domains and checking if it gets any response,” Check Point spelled out. “If there is no reaction, Raspberry Robin isn’t going to try to converse with the real C2 servers.”
Discovered this posting appealing? Abide by us on Twitter and LinkedIn to browse far more unique content we publish.
Some parts of this article are sourced from:
thehackernews.com


 MoqHao Android Malware Evolves with Auto-Execution Capability
MoqHao Android Malware Evolves with Auto-Execution Capability