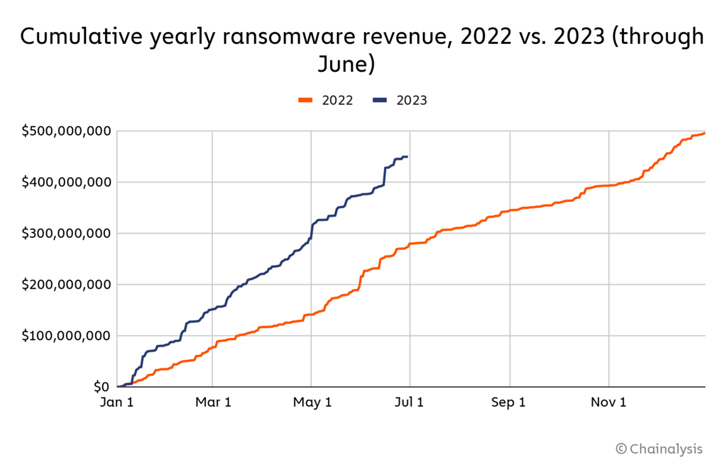
Ransomware has emerged as the only cryptocurrency-based crime to increase in 2023, with cybercriminals extorting just about $175.8 million a lot more than they did a 12 months in the past, according to conclusions from Chainalysis.
“Ransomware attackers are on rate for their second-major yr at any time, obtaining extorted at minimum $449.1 million by means of June,” the blockchain analytics organization mentioned in a midyear crypto criminal offense report shared with The Hacker Information. “If this pace proceeds, ransomware attackers will extort $898.6 million from victims in 2023, trailing only 2021’s $939.9 million.”
In distinction, crypto ripoffs have pulled in 77% much less revenue than they did by means of June of 2022, largely pushed by the abrupt exit of VidiLook, which pays end users VDL tokens in return for watching digital advertisements that then can be exchanged for significant benefits. So have the inflows to illicit addresses associated with malware, darknet markets, child abuse materials, and fraud shops.
The improvement, pursuing a decrease in ransomware revenues in 2022, marks a reversal of kinds, with Chainalysis attributing it to the return of major activity looking after a downturn final 12 months and the rising selection of thriving small assaults carried by groups like Dharma and Phobos.
On the other conclude of the spectrum lie innovative teams like Cl0p (or Clop), BlackCat, and Black Basta, which are inclined to be additional selective in their focusing on, even though also hanging more substantial companies to desire higher ransoms. Cl0p’s typical payment dimension for the initial 50 percent of 2023 stands at $1,730,486, in contrast to Dharma’s $275.
Cl0p, in certain, has been on a rampage in the latest months, exploiting security flaws in MOVEit Transfer software to breach 257 corporations throughout the world to date, for every Emsisoft researcher Brett Callow. A lot more than 17.7 million people are claimed to be impacted as a result of the ransomware attacks.
“Clop’s choice for targeting larger sized corporations (>$5 million/year income) and capitalizing on more recent-but-disclosed vulnerabilities has been the major driver of its achievements in the initial 50 % of 2023,” Sophos researcher David Wallace claimed in a report previously this 7 days, calling the team a “loud, adaptable, persistent player.”
Impending WEBINARShield Versus Insider Threats: Learn SaaS Security Posture Management
Fearful about insider threats? We’ve got you protected! Be a part of this webinar to examine sensible tactics and the insider secrets of proactive security with SaaS Security Posture Administration.
Be part of Now
Although legislation enforcement attempts to actively pursue ransomware teams and sanction providers supplying cashout products and services, coupled with the availability of decryptors, have emboldened victims to not spend up, it truly is suspected that the craze “may be prompting ransomware attackers to maximize the dimensions of their ransom needs” to extract funds from corporations who are nonetheless eager to settle.
Last but not the very least, the Russia-Ukraine War is also claimed to have been a contributing issue to the decline in ransomware assaults in 2022, causing the Conti operation to shut shop soon after declaring support for Russia.
“The conflict most likely displaced ransomware operators and diverted them away from economically influenced cyber intrusions,” Chainalysis reported. “It stands to rationale that the conflict disrupted ransomware operators’ skill to conduct assaults or maybe even their mandate for such attacks,” specially looking at that a greater part of ransomware actors are tied to Russia.
Identified this report appealing? Observe us on Twitter and LinkedIn to browse more distinctive content we article.
Some parts of this article are sourced from:
thehackernews.com


 The Risks and Preventions of AI in Business: Safeguarding Against Potential Pitfalls
The Risks and Preventions of AI in Business: Safeguarding Against Potential Pitfalls