The open up-source remote accessibility trojan acknowledged as Quasar RAT has been noticed leveraging DLL facet-loading to fly less than the radar and stealthily siphon information from compromised Windows hosts.
“This system capitalizes on the inherent believe in these documents command inside the Windows surroundings,” Uptycs researchers Tejaswini Sandapolla and Karthickkumar Kathiresan said in a report printed previous 7 days, detailing the malware’s reliance on ctfmon.exe and calc.exe as part of the attack chain.
Also regarded by the names CinaRAT or Yggdrasil, Quasar RAT is a C#-primarily based remote administration resource capable of gathering method information and facts, a checklist of managing applications, data files, keystrokes, screenshots, and executing arbitrary shell instructions.

DLL facet-loading is a popular approach adopted by lots of risk actors to execute their individual payloads by planting a spoofed DLL file with a title that a benign executable is recognized to be hunting for.
“Adversaries probable use facet-loading as a usually means of masking steps they carry out underneath a respectable, dependable, and likely elevated process or software process,” MITRE notes in its clarification of the attack system.
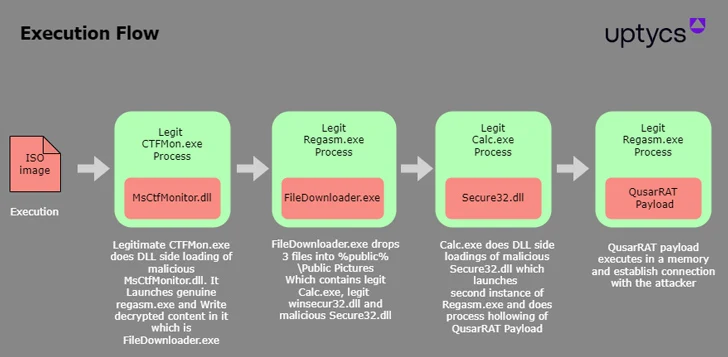
The starting issue of the attack documented by Uptycs is an ISO impression file that has a few data files: A genuine binary named ctfmon.exe that’s renamed as eBill-997358806.exe, a MsCtfMonitor.dll file that is renamed as keep an eye on.ini, and a destructive MsCtfMonitor.dll.
“When the binary file ‘eBill-997358806.exe’ is run, it initiates the loading of a file titled ‘MsCtfMonitor.dll’ (identify masqueraded) through DLL aspect-loading strategy, within just which destructive code is hid,” the scientists explained.

The concealed code is an additional executable “FileDownloader.exe” which is injected into Regasm.exe, the Windows Assembly Registration Resource, in purchase to launch the next stage, an genuine calc.exe file that loads the rogue Protected32.dll once again as a result of DLL aspect-loading and start the remaining Quasar RAT payload.
The trojan, for its part, establishes connections with a distant server to ship procedure facts and even sets up a reverse proxy for distant obtain to the endpoint.
The id of the danger actor and the exact initial obtain vector utilized to pull off the attack is unclear, but it truly is very likely to be disseminated by usually means of phishing e-mail, generating it vital that consumers be on the guard for dubious e-mail, links, or attachments.
Found this post intriguing? Comply with us on Twitter and LinkedIn to read through additional unique content material we post.
Some parts of this article are sourced from:
thehackernews.com


 Europol Dismantles Ragnar Locker Ransomware Infrastructure, Nabs Key Developer
Europol Dismantles Ragnar Locker Ransomware Infrastructure, Nabs Key Developer