Irrespective of the disruption to its infrastructure, the threat actors driving the QakBot malware have been joined to an ongoing phishing marketing campaign because early August 2023 that led to the delivery of Ransom Knight (aka Cyclops) ransomware and Remcos RAT.
This suggests that “the legislation enforcement procedure may not have impacted Qakbot operators’ spam shipping infrastructure but instead only their command-and-management (C2) servers,” Cisco Talos researcher Guilherme Venere reported in a new report printed now.
The exercise has been attributed with reasonable self-assurance by the cybersecurity organization to QakBot affiliates. There is no evidence to date that the danger actors have resumed distributing the malware loader alone submit-infrastructure takedown.

QakBot, also termed QBot and Pinkslipbot, originated as a Windows-primarily based banking trojan in 2007 and subsequently made abilities to provide more payloads, together with ransomware. In late August 2023, the notorious malware procedure was dealt a blow as section of an operation named Duck Hunt.
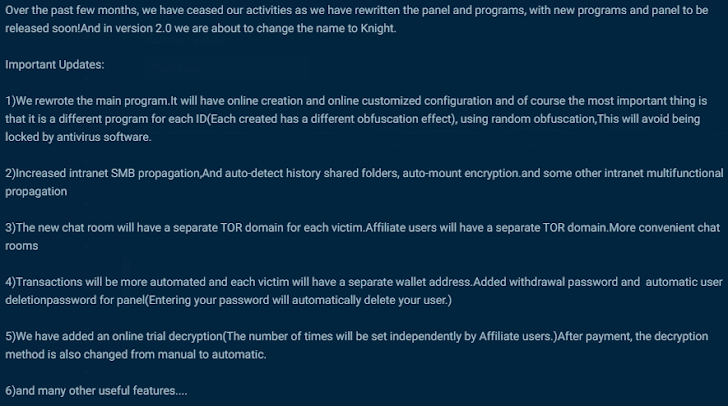
The newest action, which commenced just just before the takedown, commences with a destructive LNK file probable dispersed via phishing e-mail that, when introduced, detonates the infection and ultimately deploys the Ransom Knight ransomware, a the latest rebrand of the Cyclops ransomware-as-a-support (RaaS) scheme.
The ZIP archives made up of the LNK information have also been observed incorporating Excel insert-in (.XLL) documents to propagate the Remcos RAT, which facilitates persistent backdoor obtain to the endpoints.

Some of the file names being utilised in the campaign are created in Italian, which suggests the attackers are focusing on customers in that location.
“Although we have not observed the danger actors distributing Qakbot post-infrastructure takedown, we evaluate the malware will most likely continue to pose a major threat relocating ahead,” Venere reported.
“Presented the operators remain energetic, they may perhaps decide on to rebuild Qakbot infrastructure to thoroughly resume their pre-takedown exercise.”
Uncovered this article intriguing? Observe us on Twitter and LinkedIn to go through more special content we publish.
Some parts of this article are sourced from:
thehackernews.com


 Cisco Releases Urgent Patch to Fix Critical Flaw in Emergency Responder Systems
Cisco Releases Urgent Patch to Fix Critical Flaw in Emergency Responder Systems