Govt entities in Asia-Pacific and North The usa are being specific by an unidentified danger actor with an off-the-shelf malware downloader recognized as PureCrypter to produce an array of details stealers and ransomware.
“The PureCrypter campaign makes use of the domain of a compromised non-gain group as a command-and-handle (C2) to deliver a secondary payload,” Menlo Security researcher Abhay Yadav stated.
The various varieties of malware propagated applying PureCrypter contain RedLine Stealer, Agent Tesla, Eternity, Blackmoon (aka KRBanker), and Philadelphia ransomware.
Very first documented in June 2022, PureCrypter is advertised for sale by its creator for $59 for a single-month access (or $245 for a one particular-off lifetime buy) and is capable of distributing a multitude of malware.
In December 2022, PureCoder – the developer behind the plan – expanded the slate of offerings to include things like a logger and info stealer recognized as PureLogs, which is intended to siphon details from web browsers, crypto wallets, and email clients. It fees $99 a calendar year (or $199 for lifetime accessibility).
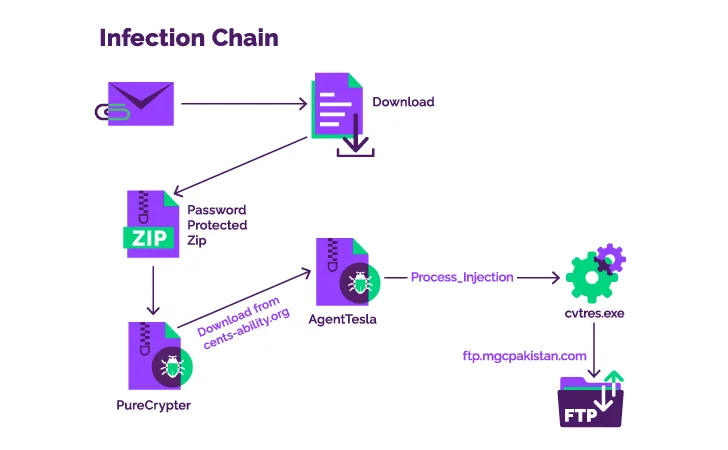
The infection sequence detailed by Menlo Security commences with a phishing email containing a Discord URL that factors to the very first-stage element, a password-protected ZIP archive that, in change, loads the PureCrypter malware.
The loader, for its element, reaches out to the site of the breached non-income entity to fetch the secondary payload, which is a .NET-based mostly keylogger named Agent Tesla.
The backdoor then establishes a connection to an FTP server located in Pakistan to exfiltrate the harvested knowledge, indicating that compromised qualifications might have been made use of to execute the action.
Uncovered this post fascinating? Comply with us on Twitter and LinkedIn to examine much more special information we put up.
Some parts of this article are sourced from:
thehackernews.com


 PlugX Trojan Disguised as Legitimate Windows Debugger Tool in Latest Attacks
PlugX Trojan Disguised as Legitimate Windows Debugger Tool in Latest Attacks