The the latest wave of cyber assaults focusing on Albanian businesses involved the use of a wiper referred to as No-Justice.
The findings appear from cybersecurity corporation ClearSky, which explained the Windows-primarily based malware “crashes the operating method in a way that it can’t be rebooted.”
The intrusions have been attributed to an Iranian “psychological operation group” named Homeland Justice, which has been working because July 2022, specially orchestrating destructive assaults against Albania.
On December 24, 2023, the adversary resurfaced immediately after a hiatus, stating it truly is “again to wipe out supporters of terrorists,” describing its newest campaign as #DestroyDurresMilitaryCamp. The Albanian town of Durrës at this time hosts the dissident team People’s Mojahedin Organization of Iran (MEK).
Targets of the attack provided 1 Albania, Eagle Cellular Albania, Air Albania, and the Albanian parliament.
Two of the main applications deployed for the duration of the marketing campaign contain an executable wiper and a PowerShell script that is created to propagate the former to other devices in the focus on network following enabling Windows Remote Administration (WinRM).

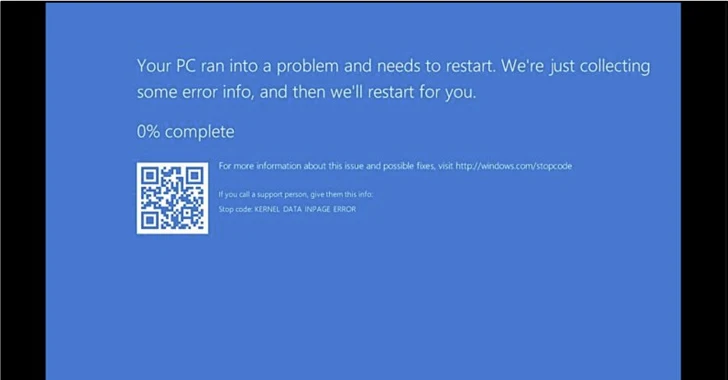
The No-Justice wiper (NACL.exe) is a 220.34 KB binary that requires administrator privileges to erase the information on the pc.
This is attained by eradicating the boot signature from the Master Boot File (MBR), which refers to the initially sector of any really hard disk that identifies wherever the running procedure is located in the disk so that it can be loaded into a computer’s RAM.
Also delivered about the course of the attack are respectable tools like Plink (aka PuTTY Link), RevSocks, and the Windows 2000 useful resource kit to aid reconnaissance, lateral motion, and persistent distant access.
The development arrives as pro-Iranian menace actors this kind of as Cyber Av3ngers, Cyber Toufan, Haghjoyan, and YareGomnam Team have increasingly set their sights on Israel and the U.S. amid continuing geopolitical tensions in the Center East.
“Teams this kind of as Cyber Av3ngers and Cyber Toufan show up to be adopting a narrative of retaliation in their cyber attacks,” Check out Point disclosed final thirty day period.
“By opportunistically concentrating on U.S. entities applying Israeli technology, these hacktivist proxies test to realize a twin retaliation approach – claiming to focus on each Israel and the U.S. in a solitary, orchestrated cyber assault.”

Cyber Toufan, in specific, has been linked to a deluge of hack-and-leak functions focusing on around 100 businesses, wiping infected hosts and releasing stolen info on their Telegram channel.
“They have brought about so substantially hurt that several of the orgs – just about a third, in actuality, haven’t been equipped to recover,” security researcher Kevin Beaumont explained. “Some of these are still totally offline over a thirty day period later on, and the wiped victims are a mix of personal firms and Israeli state govt entities.”
Final month, the Israel Countrywide Cyber Directorate (INCD) claimed it truly is at this time monitoring roughly 15 hacker groups related with Iran, Hamas, and Hezbollah that are maliciously operating in Israeli cyberspace considering the fact that the onset of the Israel-Hamas war in Oct 2023.
The agency even more observed that the strategies and ways employed share similarities with those people used in the Ukraine-Russia war, leveraging psychological warfare and wiper malware to damage facts.
Discovered this post attention-grabbing? Comply with us on Twitter and LinkedIn to browse much more exceptional information we submit.
Some parts of this article are sourced from:
thehackernews.com


 SpectralBlur: New macOS Backdoor Threat from North Korean Hackers
SpectralBlur: New macOS Backdoor Threat from North Korean Hackers