Evidence-of-notion (PoC) exploit code has been made readily available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks (formerly vRealize Network Perception).
The flaw, tracked as CVE-2023-34039, is rated 9.8 out of a greatest of 10 for severity and has been explained as a case of authentication bypass owing to a absence of exclusive cryptographic crucial technology.
“A malicious actor with network entry to Aria Functions for Networks could bypass SSH authentication to obtain access to the Aria Operations for Networks CLI,” VMware mentioned before this 7 days.
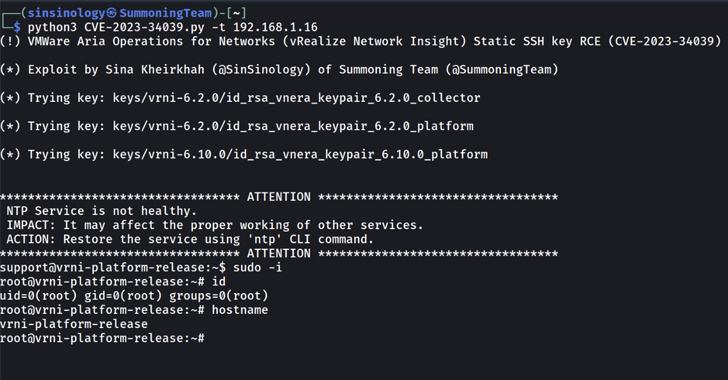
Summoning Team’s Sina Kheirkhah, who printed the PoC following an examining the patch by VMware, said the root trigger can be traced back to a bash script containing a process named refresh_ssh_keys(), which is accountable for overwriting the present-day SSH keys for the support and ubuntu people in the authorized_keys file.
“There is SSH authentication in put however, VMware forgot to regenerate the keys,” Kheirkhah stated. “VMware’s Aria Functions for Networks had hard-coded its keys from variation 6. to 6.10.”

VMware’s most recent fixes also tackle CVE-2023-20890, an arbitrary file publish vulnerability impacting Aria Operations for Networks that could be abused by an adversary with administrative obtain to generate information to arbitrary places and reach distant code execution.
In other words, a threat actor could leverage the PoC to attain admin accessibility to the machine and exploit CVE-2023-20890 to operate arbitrary payloads, earning it crucial that consumers apply the updates to protected towards potential threats.
The launch of the PoC coincides with the virtualization technology large issuing fixes for an substantial-severity SAML token signature bypass flaw (CVE-2023-20900, CVSS rating: 7.5) throughout quite a few Windows and Linux variations of VMware Tools.
“A malicious actor with person-in-the-center (MITM) network positioning in the virtual machine network may perhaps be capable to bypass SAML token signature verification, to execute VMware Resources Visitor Functions,” the enterprise claimed in an advisory launched Thursday.
Peter Stöckli of GitHub Security Lab has been credited with reporting the flaw, which has an effect on the following variations –
- VMware Instruments for Windows (12.x.x, 11.x.x, 10.3.x) – Set in 12.3.
- VMware Instruments for Linux (10.3.x) – Set in 10.3.26
- Open up-source implementation of VMware Instruments for Linux or open up-vm-resources (12.x.x, 11.x.x, 10.3.x) – Preset in 12.3. (to be dispersed by Linux vendors)
The improvement also comes as Fortinet FortiGuard Labs warned of continued exploitation of Adobe ColdFusion Vulnerabilities by menace actors to deploy cryptocurrency miners and hybrid bots these types of as Satan DDoS (aka Lucifer) and RudeMiner (aka SpreadMiner) that are able of carrying out cryptojacking and dispersed denial-of-assistance (DDoS) assaults.
Also deployed is a backdoor named BillGates (aka Setag), which is known for hijacking units, thieving delicate information, and initiating DDoS attacks.
Discovered this short article interesting? Follow us on Twitter and LinkedIn to read through a lot more exclusive written content we put up.
Some parts of this article are sourced from:
thehackernews.com

 Okta Warns of Social Engineering Attacks Targeting Super Administrator Privileges
Okta Warns of Social Engineering Attacks Targeting Super Administrator Privileges