Many security vulnerabilities have been disclosed in the TCP/IP network protocol stack of an open up-supply reference implementation of the Unified Extensible Firmware Interface (UEFI) specification made use of commonly in present day computer systems.
Collectively dubbed PixieFail by Quarkslab, the 9 issues reside in the TianoCore EFI Progress Package II (EDK II) and could be exploited to reach remote code execution, denial-of-services (DoS), DNS cache poisoning, and leakage of delicate details.
UEFI firmware – which is liable for booting the running program – from AMI, Intel, Insyde, and Phoenix Systems are impacted by the shortcomings.
EDK II incorporates its personal TCP/IP stack referred to as NetworkPkg to empower network functionalities obtainable during the preliminary Preboot eXecution Ecosystem (PXE, pronounced “pixie”) stage, which makes it possible for for management responsibilities in the absence of a managing functioning process.

In other phrases, it is a client-server interface to boot a product from its network interface card (NIC) and enables networked computers that are not still loaded with an running procedure to be configured and booted remotely by an administrator.
The code to PXE is incorporated as aspect of the UEFI firmware on the motherboard or within the NIC firmware read through-only memory (ROM).
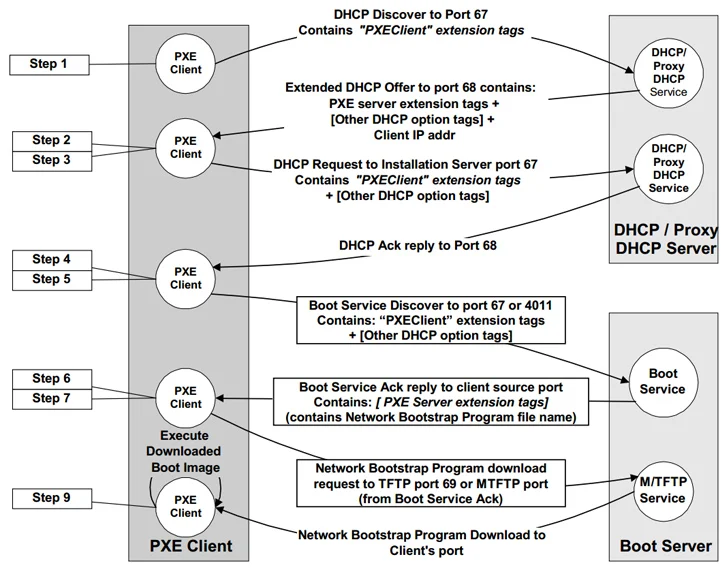
The issues recognized by Quarkslab inside of the EDKII’s NetworkPkg encompass overflow bugs, out-of-bounds browse, infinite loops, and the use of weak pseudorandom quantity generator (PRNG) that outcome in DNS and DHCP poisoning assaults, information and facts leakage, denial of services, and knowledge insertion assaults at the IPv4 and IPv6 layer.
The list of flaws is as follows –
- CVE-2023-45229 (CVSS rating: 6.5) – Integer underflow when processing IA_NA/IA_TA choices in a DHCPv6 Publicize information
- CVE-2023-45230 (CVSS rating: 8.3) – Buffer overflow in the DHCPv6 shopper by way of a very long Server ID possibility
- CVE-2023-45231 (CVSS score: 6.5) – Out-of-bounds browse when dealing with a ND Redirect message with truncated possibilities
- CVE-2023-45232 (CVSS score: 7.5) – Infinite loop when parsing mysterious selections in the Destination Selections header
- CVE-2023-45233 (CVSS score: 7.5) – Infinite loop when parsing a PadN choice in the Vacation spot Alternatives header
- CVE-2023-45234 (CVSS score: 8.3) – Buffer overflow when processing DNS Servers solution in a DHCPv6 Publicize information
- CVE-2023-45235 (CVSS rating: 8.3) – Buffer overflow when handling Server ID possibility from a DHCPv6 proxy Publicize message
- CVE-2023-45236 (CVSS score: 5.8) – Predictable TCP Original Sequence Numbers
- CVE-2023-45237 (CVSS rating: 5.3) – Use of a weak pseudorandom quantity generator

“The effect and exploitability of these vulnerabilities count on the distinct firmware create and the default PXE boot configuration,” the CERT Coordination Middle (CERT/CC) mentioned in an advisory.
“An attacker inside the nearby network (and, in certain situations remotely) could exploit these weaknesses to execute remote code, initiate DoS attacks, perform DNS cache poisoning, or extract delicate details.”
Identified this posting fascinating? Follow us on Twitter and LinkedIn to study extra distinctive content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Iranian Hackers Masquerade as Journalists to Spy on Israel-Hamas War Experts
Iranian Hackers Masquerade as Journalists to Spy on Israel-Hamas War Experts