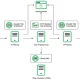
A Latin America (LATAM)-based financially motivated actor codenamed FLUXROOT has been observed leveraging Google Cloud serverless projects to orchestrate credential phishing activity, highlighting the abuse of the cloud computing model for malicious purposes.
“Serverless architectures are attractive to developers and enterprises for their flexibility, cost effectiveness, and ease of use,” Google said in its biannual Threat Horizons Report [PDF] shared with The Hacker News.
“These same features make serverless computing services for all cloud providers attractive to threat actors, who use them to deliver and communicate with their malware, host and direct users to phishing pages, and to run malware and execute malicious scripts specifically tailored to run in a serverless environment.”
The campaign involved the use of Google Cloud container URLs to host credential phishing pages with the aim of harvesting login information associated with Mercado Pago, an online payments platform popular in the LATAM region.
FLUXROOT, per Google, is the threat actor known for distributing the Grandoreiro banking trojan, with recent campaigns also taking advantage of legitimate cloud services like Microsoft Azure and Dropbox to distribute the malware.
Separately, Google’s cloud infrastructure has also been weaponized by another adversary named PINEAPPLE to propagate another stealer malware known as Astaroth (aka Guildma) as part of attacks targeting Brazilian users.
“PINEAPPLE used compromised Google Cloud instances and Google Cloud projects they created themselves to create container URLs on legitimate Google Cloud serverless domains such as cloudfunctions[.]net and run.app,” Google noted. “The URLs hosted landing pages redirecting targets to malicious infrastructure that dropped Astaroth.”
Furthermore, the threat actor is said to have attempted to bypass email gateway protections by making use of mail forwarding services that do not drop messages with failed Sender Policy Framework (SPF) records, or incorporating unexpected data in the SMTP Return-Path field in order to trigger a DNS request timeout and cause email authentication checks to fail.
The search giant said it took steps to mitigate the activities by taking down the malicious Google Cloud projects and updating its Safe Browsing lists.
The weaponization of cloud services and infrastructure by threat actors – ranging from illicit cryptocurrency mining as a consequence of weak configurations to ransomware – has been fueled by the enhanced adoption of cloud across industries.
Furthermore, the approach has the added benefit of allowing adversaries to blend into normal network activities, making detection a lot more challenging.
“Threat actors take advantage of the flexibility and ease of deployment of serverless platforms to distribute malware and host phishing pages,” the company said. “Threat actors abusing cloud services shift their tactics in response to defenders’ detection and mitigation measures.”
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
Some parts of this article are sourced from:
thehackernews.com


 How to Set up an Automated SMS Analysis Service with AI in Tines
How to Set up an Automated SMS Analysis Service with AI in Tines