Microsoft is warning of an increase in adversary-in-the-middle (AiTM) phishing techniques, which are staying propagated as portion of the phishing-as-a-provider (PhaaS) cybercrime product.
In addition to an uptick in AiTM-capable PhaaS platforms, the tech large famous that existing phishing services like PerSwaysion are incorporating AiTM abilities.
“This enhancement in the PhaaS ecosystem enables attackers to conduct substantial-quantity phishing strategies that try to circumvent MFA protections at scale,” the Microsoft Risk Intelligence staff mentioned in a sequence of posts on X (previously Twitter).

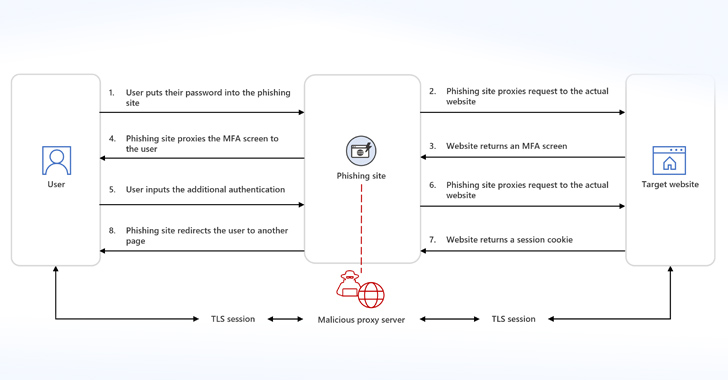
Phishing kits with AiTM capabilities operate in two techniques, one particular of which worries the use of reverse proxy servers (i.e., the phishing site) to relay targeted traffic to and from the customer and genuine website and stealthily capture consumer qualifications, two-variable authentication codes, and session cookies.
A next method requires synchronous relay servers.
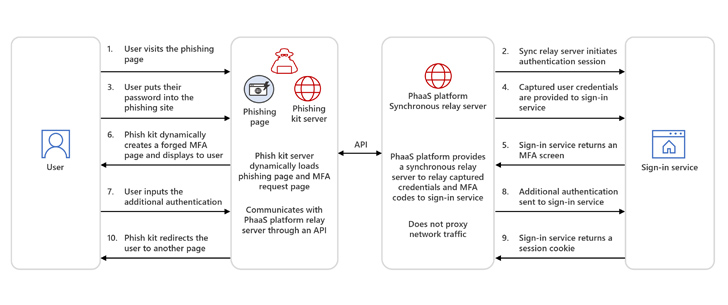
“In AiTM by way of synchronous relay servers the target is offered with a copy or mimic of a indication-in site, like classic phishing attacks,” Microsoft mentioned. “Storm-1295, the actor team guiding the Greatness PhaaS platform, delivers synchronous relay providers to other attackers.”
Greatness was to start with documented by Cisco Talos in Could 2023 as a services that allows cybercriminals concentrate on organization end users of the Microsoft 365 cloud assistance applying convincing decoy and login webpages. It truly is mentioned to have been energetic due to the fact at minimum mid-2022.

The ultimate goal of these types of assaults is to siphon session cookies, enabling menace actors to obtain privileged techniques without reauthentication.
“Circumventing MFA is the objective that determined attackers to acquire AiTM session cookie theft procedures,” the tech big mentioned. “In contrast to classic phishing attacks, incident reaction treatments for AiTM demand revocation of stolen session cookies.”
Discovered this report intriguing? Comply with us on Twitter and LinkedIn to browse a lot more unique material we publish.
Some parts of this article are sourced from:
thehackernews.com

 Experts Uncover How Cybercriminals Could Exploit Microsoft Entra ID for Elevated Privilege
Experts Uncover How Cybercriminals Could Exploit Microsoft Entra ID for Elevated Privilege