A innovative Facebook phishing marketing campaign has been observed exploiting a zero-day flaw in Salesforce’s email providers, making it possible for threat actors to craft specific phishing messages employing the company’s area and infrastructure.
“People phishing campaigns cleverly evade typical detection solutions by chaining the Salesforce vulnerability and legacy quirks in Facebook’s Web Game titles system,” Guardio Labs scientists Oleg Zaytsev and Nati Tal said in a report shared with The Hacker Information.
The email messages masquerade as coming from Meta, whilst getting sent from an email handle with a “@salesforce.com” area. They find to trick recipients into clicking on a url by saying that their Facebook accounts are undergoing a “comprehensive investigation” owing to “suspicions of engaging in impersonation.”
The aim is to immediate users to a rogue landing website page that’s built to capture the victim’s account credentials and two-variable authentication (2FA) codes. What helps make the attack noteworthy is that the phishing kit is hosted as a sport less than the Facebook apps system utilizing the domain applications.fb[.]com.

“So it truly is a no-brainer why we have witnessed this email slipping via common anti-spam and anti-phishing mechanisms. It includes legit back links (to facebook.com) and is despatched from a legit email handle of @salesforce.com, one particular of the world’s main CRM suppliers,” the scientists described.
It’s worthy of pointing out that Meta retired the Web Games aspect in July 2020, whilst it can be possible to retain assist for legacy games that have been produced prior to its deprecation.
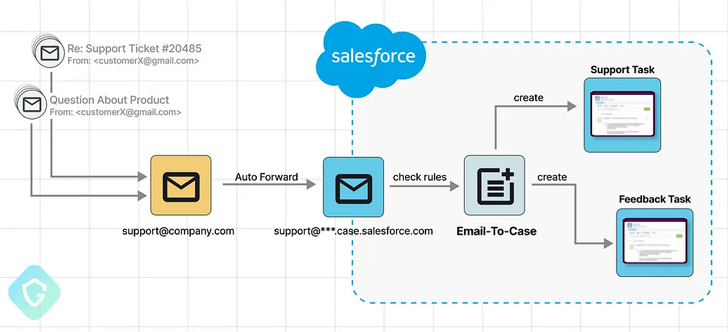
Although sending out emails using a salesforce.com entails a validation action, Guardio Labs said the scheme cleverly gets all-around these protective actions by configuring an Email-to-Scenario inbound routing email deal with that uses the salesforce.com domain and location it up as the organization-wide email handle.
“This triggers the verification circulation that sends the email to this routing deal with, ending up as a new undertaking in our program,” the scientists said, incorporating it prospects to a scenario exactly where a salesforce.com email handle can be confirmed merely by clicking on the link accompanying the ask for to incorporate the actor-controlled deal with.

“From in this article you just go on and build any variety of phishing plan, even focusing on Salesforce prospects right with these kinds of e-mail. And the higher than will close up in the victim’s inbox, bypassing anti-spam and anti-phishing mechanisms, and even marked as Critical by Google.”
Subsequent liable disclosure on June 28, 2023, Salesforce dealt with the zero-day as of July 28, 2023, with new checks that avoid the use of email addresses from the @salesforce.com area.
The progress will come as Cofense warned of elevated phishing exercise that employs Google Accelerated Cell Internet pages (AMP) URLs to bypass security checks and conduct credential theft.
“The prevalence of phishing assaults and scams stays superior, with negative actors consistently testing the restrictions of email distribution infrastructure and existing security measures,” the scientists said.
“A regarding facet of this ongoing battle is the exploitation of seemingly authentic companies, this kind of as CRMs, advertising and marketing platforms, and cloud-based mostly workspaces, to carry out destructive pursuits.”
Located this short article fascinating? Comply with us on Twitter and LinkedIn to read through a lot more distinctive information we put up.
Some parts of this article are sourced from:
thehackernews.com


 Top Industries Significantly Impacted by Illicit Telegram Networks
Top Industries Significantly Impacted by Illicit Telegram Networks