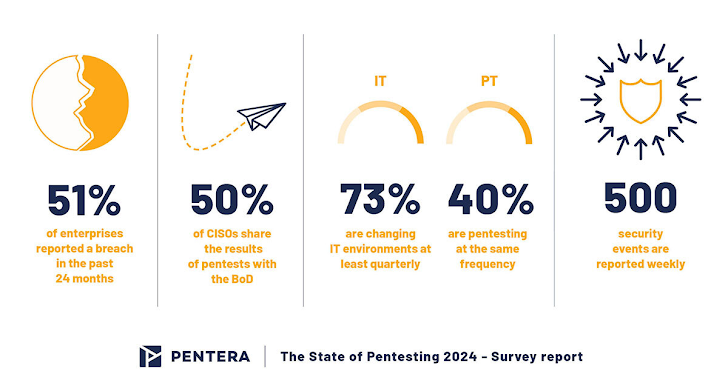
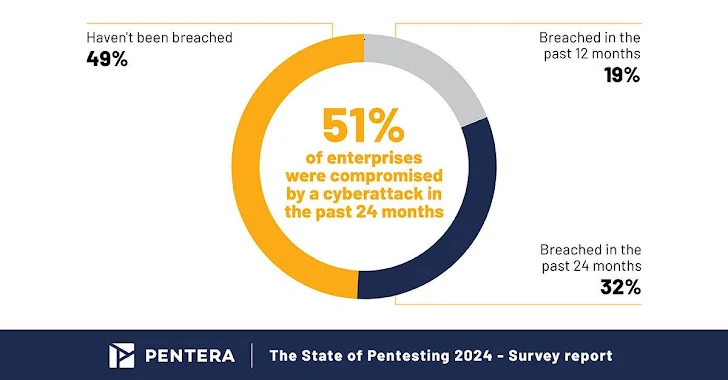
About the past two a long time, a shocking 51% of organizations surveyed in a main business report have been compromised by a cyberattack. Certainly, over 50 percent.
And this, in a globe the place enterprises deploy an regular of 53 diverse security methods to safeguard their digital domain.
Alarming? Totally.
A latest study of CISOs and CIOs, commissioned by Pentera and performed by World Surveyz Study, delivers a quantifiable glimpse into this evolving battlefield, revealing a stark contrast concerning the escalating hazards and the tightening price range constraints below which cybersecurity pros function.
With this report, Pentera has at the time again taken a magnifying glass to the condition of pentesting to launch its once-a-year report about today’s pentesting techniques. Partaking with 450 security executives from North The usa, LATAM, APAC, and EMEA—all in VP or C-level positions at organizations with in excess of 1,000 employees—the report paints a recent image of fashionable security validation techniques across the enterprise.
Critical results incorporate:
- The impression of a breach is high:
- 43% noted unplanned downtime
- 36% reported info exposure
- 31% documented money decline
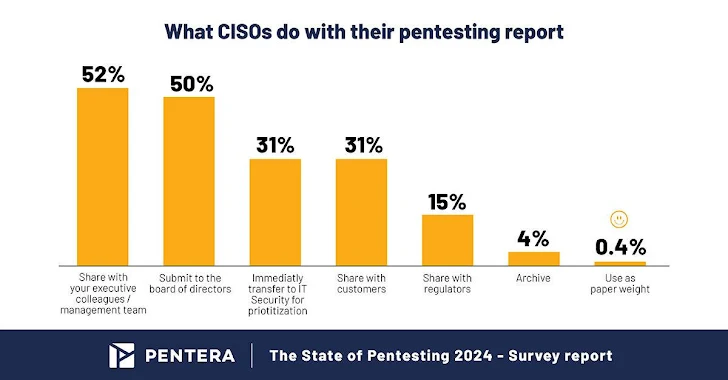
- As Board of Administrators (BoDs) develop into extra cyber conscious, more than 50% of CISOs now share their pentesting stories with their BoDs.
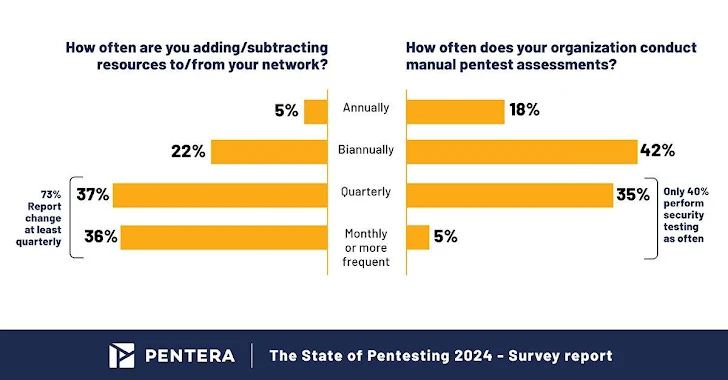
- You can find a notable hole among the fee of transform in IT environments and the frequency of security tests, leaving organizations’ digital property untested for prolonged periods of time.
- With an common of 500 remediation gatherings for each week, productive prioritization is a person of the most critical components for security groups.
Security Breaches Persist Even with Investments
The 2024 report reveals that enterprises have an typical of 53 security alternatives, yet they are having difficulties to preserve the Confidentiality, Integrity, Availability (CIA) triad. As element of security procedures and techniques, this triad protects data systems and facts from many threats, making certain that information is safe, dependable, and accessible to the correct individuals.
This fact is underscored by the fact that 51% of CISOs surveyed admitted to a cybersecurity breach in the past two several years. These types of breaches have led to sizeable operational disruptions, which include unplanned downtime, info publicity, and economic losses. Only 7% of enterprises avoided considerable impression resulting from a breach. These incidents exhibit the relevance of possessing robust cybersecurity defenses.
Enterprises knowledgeable a approximately equivalent distribution of assaults across their IT infrastructure like distant equipment, on-premise, and cloud environments, pointing to the will need to often examination and safe each of these domains. The heightened profile of the cloud as an attack concentrate on is reliable with other industry studies. Crowdstrike’s World-wide Danger Report for 2024 noted a 75% improve in cloud intrusions YoY. They projected that in the coming years, as much more businesses progress with their cloud migration initiatives and change toward predominantly cloud or cloud-native deployments, this determine will improve.
Greater Government and Board Involvement
In mild of substantial-profile breaches producing headlines, there’s a notable surge in cybersecurity oversight from the top. About 50 % of the CISOs now frequently report pentest outcomes to their boards of administrators, highlighting the strategic relevance of cybersecurity to the company. CISOs are ever more applying pentest studies as a way to far better connect cybersecurity threats to their government teams and boards.
On top of that, 31% of CISOs share pentest results with buyers, acknowledging the importance of transparency in controlling 3rd-get together and provide chain pitfalls. Adopting this exercise not only builds rely on but also promotes a lifestyle of openness about cybersecurity challenges and measures.
Closing the Pentesting Hole
The survey highlights a disconcerting hole among the frequency of IT environment adjustments and the cadence of security testing. Even though 73% of corporations report producing quarterly IT modifications only 40% match this tempo with their pentesting initiatives. This leaves organizations open to risk for extended periods.
On ordinary, enterprises dedicate $164,400 to manual pentesting, symbolizing 12.9% of their once-a-year IT security funds. With 60% of corporations pentesting twice a 12 months at most, this is a substantial financial commitment and a sizable portion of the budget for a security exercise that presents just a snap-shot evaluation of the security posture. Offered the value of pentests in direction of improving IT resilience, it truly is well worth thinking of remedies that supply scalable ongoing pentesting.
Patch Best Isn’t Real looking
Over and above remediation actions, security groups are tasked with a varied set of duties that extend them to their restrictions.
Versus this backdrop, businesses are flooded with security functions. With about 60% of enterprises reporting they acquire at least 500 incidents necessitating remediation weekly, patch perfection has never been a lot more elusive. It is significantly obvious that the artwork of prioritization is a person that security groups will need to have to find out to preserve their organization’s perfectly-safeguarded. Security groups who are able to successfully fully grasp the context of a vulnerability, its compensating controls, and the facts it leads to will be the ones to keep in the recreation.
What do These Findings Necessarily mean?
The Condition of Pentesting Study of 2024, by Pentera, underscores a critical juncture for cybersecurity: As threats proceed to evolve, quite a few security methods are unsuccessful to mitigate them, requiring CISOs to extra constantly validate the security of their infrastructure.
The insights from this study are not just statistics—they are a contact to motion for better, extra effective cybersecurity practices that align with the economical and operational realities of our time.
Unpack important results from the 2024 Condition of Pentesting Survey in this webinar. Join us as we investigate the conclusions, go over techniques to manage cybersecurity, prioritize duties, and learn how to connect your security posture to management a lot more successfully.
Download the 2024 State of Pentesting Survey or sign-up below to go to the reside webinar.
Identified this write-up interesting? This write-up is a contributed piece from a single of our valued partners. Comply with us on Twitter and LinkedIn to read much more distinctive content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 MITRE Corporation Breached by Nation-State Hackers Exploiting Ivanti Flaws
MITRE Corporation Breached by Nation-State Hackers Exploiting Ivanti Flaws