Security vulnerabilities uncovered in Honda’s e-commerce system could have been exploited to achieve unrestricted accessibility to sensitive seller information.
“Broken/lacking obtain controls produced it doable to entry all facts on the system, even when logged in as a examination account,” security researcher Eaton Zveare said in a report published final week.
The platform is developed for the sale of electrical power products, maritime, garden and garden organizations. It does not effects the Japanese company’s vehicle division.
The hack, in a nutshell, exploits a password reset mechanism on a single of Honda’s websites, Power Machines Tech Specific (PETE), to reset the password connected with any account and obtain comprehensive admin-degree access.

This is made doable thanks to the actuality that the API enables any person to mail a password reset request only by just understanding the username or email tackle and without having acquiring to enter a password tied to that account.
Armed with this functionality, a malicious actor could sign in and takeover a further account, and subsequently take gain of the sequential character of the vendor web site URLs (i.e., “admin.pedealer.honda[.]com/dealersite/
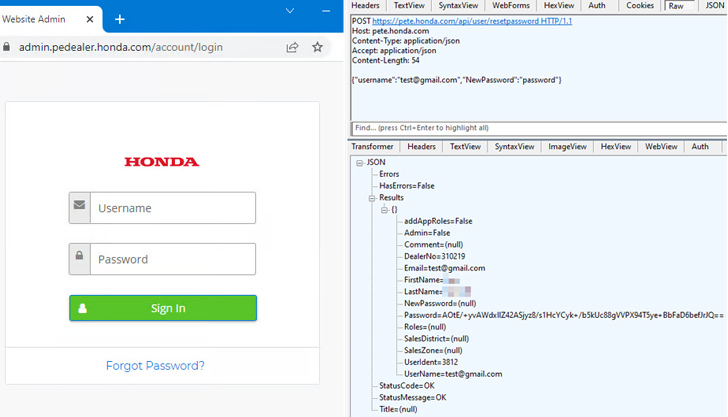
“Just by incrementing that ID, I could get access to every dealers’ data,” Zveare explained. “The fundamental JavaScript code can take that ID and utilizes it in API phone calls to fetch data and exhibit it on the web site. Fortunately, this discovery rendered the require to reset any extra passwords moot.”
To make matters even worse, the style and design flaw could have been used to access a dealer’s shoppers, edit their internet site and items, and worse, elevate privileges to the administrator of the overall system – a feature limited to Honda staff – by indicates of a specially crafted request to view specifics of the dealer network.
Approaching WEBINAR🔐 Mastering API Security: Understanding Your Real Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and get proactive techniques in direction of ironclad security. Sign up for our insightful webinar!
Join the Session.wn-button,.wn-label,.wn-label:immediately afterdisplay screen:inline-block.look at_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-proper-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-weight:600letter-spacing:.6pxcolor:#596cec.wn-label:just afterwidth:50pxheight:6pxcontent:”border-top:2px stable #d9deffmargin: 8px.wn-titlefont-measurement:21pxpadding:10px 0font-fat:900textual content-align:leftline-top:33px.wn-descriptiontext-align:leftfont-sizing:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-dimension:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-excess weight:500letter-spacing:.2px
In all, the weaknesses allowed for illegitimate access to 21,393 consumer orders throughout all dealers from August 2016 to March 2023 1,570 dealer web-sites (of which 1,091 are energetic), 3,588 seller accounts, 1,090 seller e-mail, and 11,034 consumer e-mails.
Threat actors could also leverage obtain to these vendor web-sites by planting skimmer or cryptocurrency mining code, thus allowing them to experience illicit gains.
The vulnerabilities, next accountable disclosure on March 16, 2023, have been dealt with by Honda as of April 3, 2023.
The disclosure arrives months after Zveare thorough security issues in Toyota’s World-wide Supplier Preparation Facts Administration System (GSPIMS) and C360 CRM that could have been leveraged to obtain a prosperity of company and buyer facts.
Found this article appealing? Follow us on Twitter and LinkedIn to read far more exclusive written content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Beware: 1,000+ Fake Cryptocurrency Sites Trap Users in Bogus Rewards Scheme
Beware: 1,000+ Fake Cryptocurrency Sites Trap Users in Bogus Rewards Scheme