French cloud computing agency OVHcloud reported it mitigated a record-breaking dispersed denial-of-support (DDoS) attack in April 2024 that achieved a packet fee of 840 million packets per 2nd (Mpps).
This is just earlier mentioned the past record of 809 million Mpps claimed by Akamai as targeting a large European financial institution in June 2020.
The 840 Mpps DDoS attack is said to have been a blend of a TCP ACK flood that originated from 5,000 source IPs and a DNS reflection attack leveraging about 15,000 DNS servers to amplify the website traffic.
“When the attack was distributed throughout the world, 2/3 of total packets entered from only 4 [points of presence], all located in the U.S. with 3 of them currently being on the west coast,” OVHcloud observed. “This highlights the capability of the adversary to send a massive packet fee by only a handful of peerings, which can prove pretty problematic.”

The company reported it has noticed a substantial uptick in DDoS attacks in terms of the two frequency and depth starting 2023, adding people achieving over 1 terabit for each 2nd (Tbps) have develop into a normal occurrence.
“In the past 18 months, we went from 1+ Tbps assaults currently being rather scarce, then weekly, to virtually every day (averaged out more than one 7 days),” OVHcloud’s Sebastien Meriot reported. “The highest bit price we noticed for the duration of that time period was ~2.5 Tbps.”
Compared with usual DDoS attacks that depend on sending a flood of junk traffic to targets with an purpose to exhaust available bandwidth, packet charge assaults get the job done by overloading the packet processing engines of networking devices shut to the vacation spot, these kinds of as load balancers.
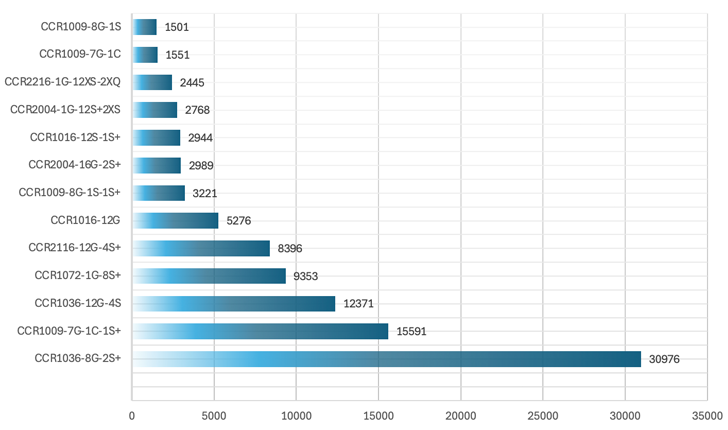
Information collected by the firm exhibits that DDoS attacks leveraging packet prices increased than 100 Mpps have witnessed a sharp enhance for the similar time period of time, with lots of of them emanating from compromised MikroTik Cloud Main Router (CCR) gadgets. As several as 99,382 MikroTik routers are accessible around the internet.
These routers, other than exposing an administration interface, run on outdated variations of the operating process, earning them inclined to identified security vulnerabilities in RouterOS. It truly is suspected that threat actors are likely weaponizing the working system’s Bandwidth check function to pull off the attacks.

It is really estimated that even hijacking 1% of the uncovered products into a DDoS botnet could theoretically give adversaries adequate capabilities to launch layer 7 attacks reaching 2.28 billion packets for every next (Gpps).
It bears noting at this phase that MikroTik routers have been leveraged for building strong botnets this kind of as Mēris and even used for launching botnet-as-a-service operations.
“Relying on the range of compromised units and their actual abilities, this could be a new period for packet rate attacks: with botnets perhaps able of issuing billions of packets per second, it could severely obstacle how anti-DDoS infrastructures are developed and scaled,” Meriot claimed.
Uncovered this short article exciting? Stick to us on Twitter and LinkedIn to browse additional unique material we article.
Some parts of this article are sourced from:
thehackernews.com


 Blueprint for Success: Implementing a CTEM Operation
Blueprint for Success: Implementing a CTEM Operation