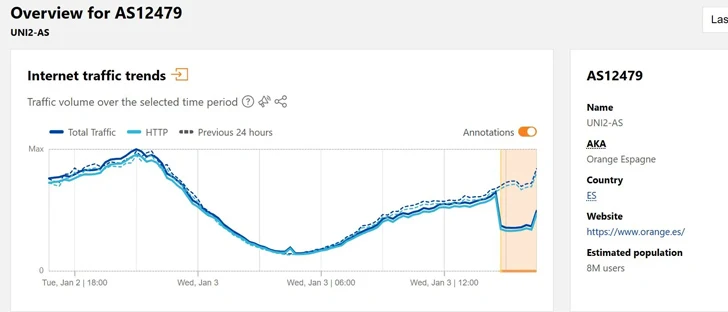
Cell network operator Orange Spain endured an internet outage for many hours on January 3 soon after a threat actor used administrator credentials captured by signifies of stealer malware to hijack the border gateway protocol (BGP) site visitors.
“The Orange account in the IP network coordination middle (RIPE) has endured poor entry that has afflicted the searching of some of our shoppers,” the company explained in a concept posted on X (formerly Twitter).
On the other hand, the organization emphasized no private details was compromised and that the incident only influenced some searching products and services.

The menace actor, who goes by the title Ms_Snow_OwO on X, claimed to have attained access to Orange Spain’s RIPE account. RIPE is a regional Internet registry (RIR) that oversees the allocation and registration of IP addresses and autonomous program (AS) figures in Europe, Central Asia, Russia, and West Asia.
“Employing the stolen account, the risk actor modified the AS amount belonging to Orange’s IP deal with, resulting in major disruptions to Orange and a 50% decline in visitors,” cybersecurity organization Hudson Rock said.
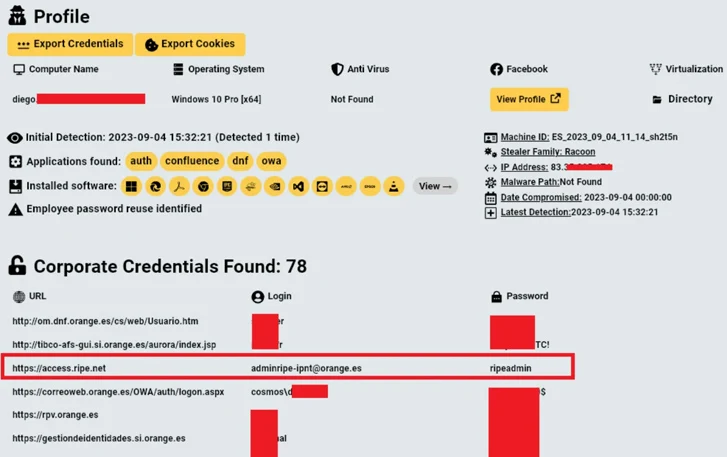
Additional investigation has discovered that the email address of the admin account is involved with the computer of an Orange Spain worker who was infiltrated by Raccoon Stealer malware on September 4, 2023.
It’s at present not acknowledged how the stealer found its way to the employee’s process, but these kinds of malware households are generally propagated by way of malvertising or phishing cons.
“Amongst the corporate qualifications recognized on the machine, the worker experienced specific credentials to ‘https://access.ripe.net’ utilizing the email address which was discovered by the danger actor ([email protected]),” the business extra.
Even worse, the password used to protected Orange’s RIPE administrator account was “ripeadmin,” which is both weak and quickly predictable.

Security researcher Kevin Beaumont even more mentioned that RIPE neither mandates two-issue authentication (2FA) nor enforces a robust password policy for its accounts, creating it ripe for abuse.
“At the moment, infostealer marketplaces are offering thousands of qualifications to access.ripe.net — properly letting you to repeat this at companies and ISPs across Europe,” Beaumont mentioned.
RIPE, which is at present investigating to see if any other accounts have been afflicted in a identical fashion, mentioned it will right reach out to afflicted account holders. It has also urged RIPE NCC Access account consumers to update their passwords and empower multi-factor authentication for their accounts.
“In the prolonged term, we are expediting the 2FA implementation to make it mandatory for all RIPE NCC Access accounts as quickly as doable and to introduce a wide range of verification mechanisms,” it additional.
The incident serves to spotlight the effects of infostealer infections, necessitating that organizations acquire steps to safe their networks from regarded first attack vectors.
Uncovered this post interesting? Observe us on Twitter and LinkedIn to study more special content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Alert: Ivanti Releases Patch for Critical Vulnerability in Endpoint Manager Solution
Alert: Ivanti Releases Patch for Critical Vulnerability in Endpoint Manager Solution