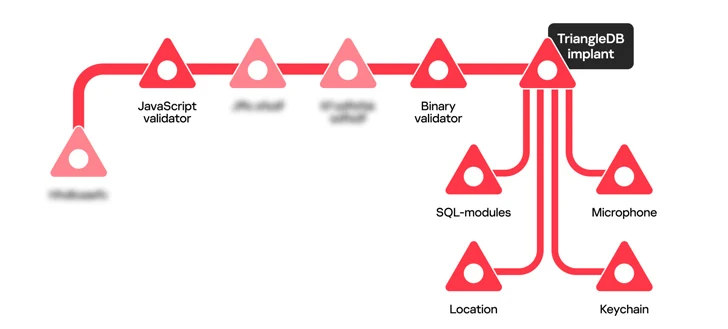
The TriangleDB implant applied to concentrate on Apple iOS equipment packs in at least four distinctive modules to report microphone, extract iCloud Keychain, steal facts from SQLite databases utilised by a variety of applications, and estimate the victim’s place.
The results occur from Kaspersky, which detailed the fantastic lengths the adversary powering the marketing campaign, dubbed Operation Triangulation, went to conceal and go over up its tracks though clandestinely hoovering sensitive info from the compromised units.
The complex attack to start with arrived to light in June 2023, when it emerged that iOS have been targeted by a zero-click exploit weaponizing then zero-working day security flaws (CVE-2023-32434 and CVE-2023-32435) that leverages the iMessage system to produce a destructive attachment that can acquire comprehensive control more than the unit and user facts.
The scale and the identification of the danger actor is presently not known, whilst Kaspersky by itself turned 1 of the targets at the get started of the 12 months, prompting it to investigate the a variety of elements of what it said in a totally-showcased sophisticated persistent danger (APT) system.
The core of the attack framework constitutes a backdoor termed TriangleDB that is deployed immediately after the attackers obtain root privileges on the target iOS gadget by exploiting CVE-2023-32434, a kernel vulnerability that could be abused to execute arbitrary code.

Now, according to the Russian cybersecurity company, the deployment of the implant is preceded by two validator stages, specifically JavaScript Validator and Binary Validator, that are executed to establish if the concentrate on system is not linked with a investigation atmosphere.
“These validators accumulate numerous details about the target system and deliver it to the C2 server,” Kaspersky researchers Georgy Kucherin, Leonid Bezvershenko, and Valentin Pashkov explained in a technical report released Monday.
“This information is then applied to evaluate if the iPhone or iPad to be implanted with TriangleDB could be a analysis product. By carrying out such checks, attackers can make absolutely sure that their zero-day exploits and the implant do not get burned.”
By way of history: The starting stage of the attack chain is an invisible iMessage attachment that a sufferer receives, which triggers a zero-click exploit chain designed to stealthily open up a exclusive URL containing obfuscated JavaScript as nicely as an encrypted payload.
The payload is the JavaScript validator that, aside from conducting several arithmetic functions and checking for the presence of Media Source API and WebAssembly, performs a browser fingerprinting strategy named canvas fingerprinting by drawing a yellow triangle on a pink track record with WebGL and calculating its checksum.
The information and facts collected following this stage is transmitted to a remote server in order to receive, in return, an unknown upcoming-stage malware. Also sent immediately after a collection of undetermined methods is a Binary Validator, a Mach-O binary file that carries out the under operations –
- Get rid of crash logs from the /non-public/var/cellular/Library/Logs/CrashReporter listing to erase traces of possible exploitation
- Delete evidence of the destructive iMessage attachment despatched from 36 distinctive attacker-controlled Gmail, Outlook, and Yahoo email addresses
- Get a record of procedures functioning on the device and the network interfaces
- Check if the target gadget is jailbroken
- Flip on individualized ad monitoring
- Gather information and facts about the machine (username, phone quantity, IMEI, and Apple ID), and
- Retrieve a list of mounted applications
“What is attention-grabbing about these steps is that the validator implements them equally for iOS and macOS programs,” the researchers claimed, including the results of the aforementioned actions are encrypted and exfiltrated to a command-and-command (C2) server to fetch the TriangleDB implant.

1 of the very initial methods taken by the backdoor is to establish communication with the C2 server and mail a heartbeat, subsequently obtaining instructions that delete crash log and databases data files to protect up the forensic path and hamper investigation.
Also issued to the implant are instructions to periodically exfiltrate documents from the /personal/var/tmp directory that incorporate location, iCloud Keychain, SQL-associated, and microphone-recorded facts.
A noteworthy characteristic of the microphone-recording module is its potential to suspend recording when the unit display screen is turned on, indicating the risk actor’s intention to fly underneath the radar.
What is extra, the locale-checking module is orchestrated to use GSM knowledge, this kind of as cellular region code (MCC), mobile network code (MNC), and site area code (LAC), to triangulate the victim’s location when GPS information is not obtainable.
“The adversary powering Triangulation took good care to stay away from detection,” the researchers claimed. “The attackers also showed a wonderful knowing of iOS internals, as they used personal undocumented APIs in the training course of the attack.”
Observed this short article interesting? Adhere to us on Twitter and LinkedIn to examine much more exceptional content material we post.
Some parts of this article are sourced from:
thehackernews.com

 Backdoor Implant on Hacked Cisco Devices Modified to Evade Detection
Backdoor Implant on Hacked Cisco Devices Modified to Evade Detection