Cybersecurity scientists have disclosed a security flaw in the Opera web browser for Microsoft Windows and Apple macOS that could be exploited to execute any file on the fundamental running method.
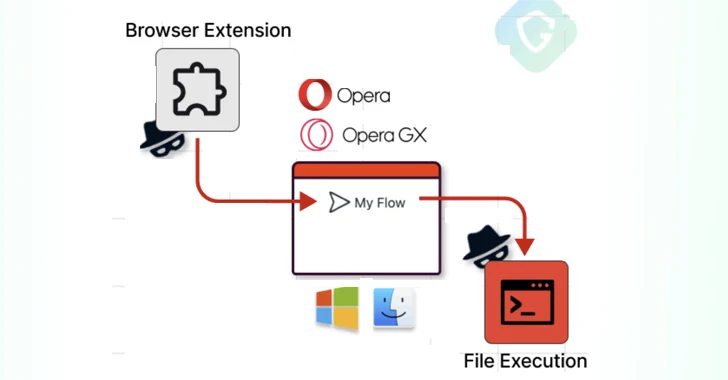
The distant code execution vulnerability has been codenamed MyFlaw by the Guardio Labs study workforce owing to the point that it will take gain of a feature termed My Stream that tends to make it possible to sync messages and documents amongst cell and desktop devices.
“This is obtained through a controlled browser extension, properly bypassing the browser’s sandbox and the total browser approach,” the enterprise claimed in a assertion shared with The Hacker News.
The issue impacts equally the Opera browser and Opera GX. Subsequent accountable disclosure on November 17, 2023, it was dealt with as aspect of updates delivered on November 22, 2023.
My Movement options a chat-like interface to trade notes and documents, the latter of which can be opened by means of a web interface, which means a file can be executed outside of the browser’s security boundaries.

It is pre-set up in the browser and facilitated by implies of a built-in (or inner) browser extension referred to as “Opera Contact Track record,” which is dependable for speaking with its mobile counterpart.
This also implies that the extension will come with its individual manifest file specifying all the demanded permissions and its actions, which includes a assets known as externally_connectable that declares which other web internet pages and extensions can hook up to it.
“This exposes the messaging API to any page that matches the URL styles you specify,” Google notes in its documentation. “The URL sample will have to consist of at least a second-stage domain.”
In the scenario of Opera, the domains that can chat to the extension need to match the patterns “*.movement.opera.com” and “.movement.op-test.net” – each controlled by the browser seller itself.
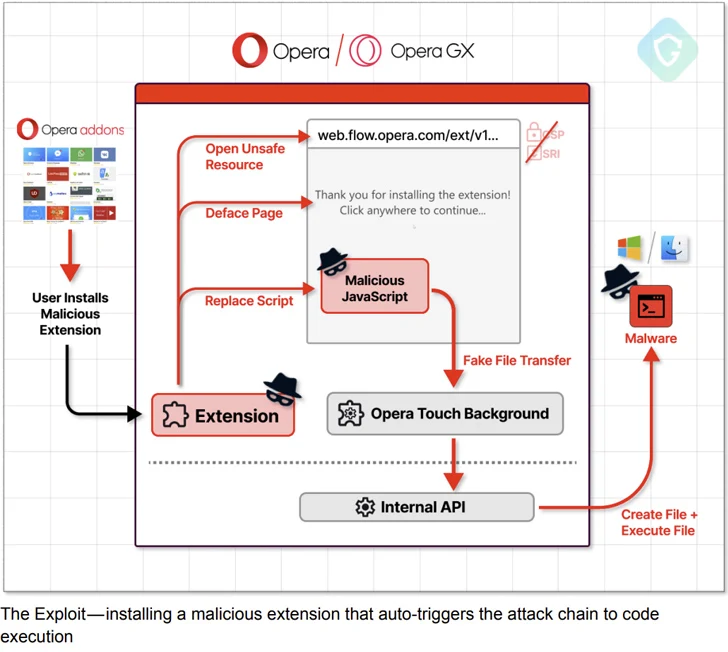
Guardio Labs mentioned it was able to unearth a “extended-neglected” version of the My Move landing web site hosted on the domain “web.movement.opera.com” utilizing the urlscan.io web-site scanner software.
“The site by itself seems quite the very same as the existing just one in manufacturing, but variations lie below the hood: Not only that it lacks the [content security policy] meta tag, but it also retains a script tag contacting for a JavaScript file with out any integrity look at,” the enterprise reported.
“This is accurately what an attacker wants – an unsafe, overlooked, vulnerable to code injection asset, and most importantly, has entry to (pretty) substantial authorization native browser API.”
The attack chain then hinges, developing a specifically crafted extension that masquerades as a cellular unit to pair with the victim’s laptop or computer and transmit an encrypted malicious payload by way of the modified JavaScript file to the host for subsequent execution by prompting the person to simply click anywhere on the display.

The findings highlight the growing complexity of browser-centered attacks and the different vectors that can be exploited by danger actors to their edge.
“Even with functioning in sandboxed environments, extensions can be potent applications for hackers, enabling them to steal info and breach browser security boundaries,” the corporation instructed The Hacker News.
“This underscores the have to have for inner design adjustments at Opera and enhancements in Chromium’s infrastructure. For instance, disabling third-occasion extension permissions on devoted output domains, very similar to Chrome’s web keep, is advised but has not but been implemented by Opera.”
When attained for comment, Opera claimed it moved quickly to close the security hole and apply a take care of on the server facet and that it’s having methods to stop this sort of issues from going on once more.
“Our current composition takes advantage of an HTML standard, and is the most secure solution that does not break vital operation,” the corporation claimed. “Soon after Guardio alerted us to this vulnerability, we eliminated the trigger of these issues and we are building confident that related complications will not seem in the upcoming.”
“We would like to thank Guardio Labs for their do the job on uncovering and promptly alerting us to this vulnerability. This collaboration demonstrates how we function with each other with security authorities and scientists all over the planet to enhance our own endeavours at sustaining and bettering the security of our goods and making certain our consumers have a risk-free on line encounter.”
Discovered this short article fascinating? Stick to us on Twitter and LinkedIn to examine extra exclusive information we publish.
Some parts of this article are sourced from:
thehackernews.com

 High-Severity Flaws Uncovered in Bosch Thermostats and Smart Nutrunners
High-Severity Flaws Uncovered in Bosch Thermostats and Smart Nutrunners