Id products and services company Okta has disclosed that it detected “additional risk actor exercise” in link with the October 2023 breach of its assistance scenario management technique.
“The menace actor downloaded the names and email addresses of all Okta purchaser guidance method users,” the enterprise claimed in a statement shared with The Hacker Information.
“All Okta Workforce Id Cloud (WIC) and Purchaser Identification Solution (CIS) buyers are impacted except clients in our FedRamp High and DoD IL4 environments (these environments use a independent support system NOT accessed by the threat actor). The Auth0/CIC assist case administration procedure was not impacted by this incident.”
News of the expanded scope of the breach was to start with reported by Bloomberg.

The company also explained to the publication that when it does not have any evidence of the stolen data staying actively misused, it has taken the phase of notifying all customers of likely phishing and social engineering dangers.
It also stated that it “pushed new security features to our platforms and presented customers with certain tips to protect towards likely targeted assaults versus their Okta directors.”
Okta, which has enlisted the aid of a electronic forensics company to assistance its investigation, more reported it “will also notify people that have had their details downloaded.”
The improvement arrives more than 3 weeks right after the id and authentication management provider said the breach, which took area in between September 28 to October 17, 2023, influenced 1% – i.e., 134 – of its 18,400 consumers.
The identity of the menace actors powering the attack versus Okta’s systems is at this time not regarded, even though a infamous cybercrime group referred to as Scattered Spider has qualified the organization as lately as August 2023 to get hold of elevated administrator permissions by pulling off subtle social engineering attacks.

In accordance to a report printed by ReliaQuest very last week, Scattered Spider infiltrated an unnamed company and attained access to an IT administrator’s account by using Okta single sign-on (SSO), followed by laterally shifting from the id-as-a-service (IDaaS) supplier to their on-premises assets in considerably less than just one hour.
The formidable and nimble adversary, in the latest months, has also advanced into an affiliate for the BlackCat ransomware operation, infiltrating cloud and on-premises environments to deploy file-encrypting malware for producing illicit gains.
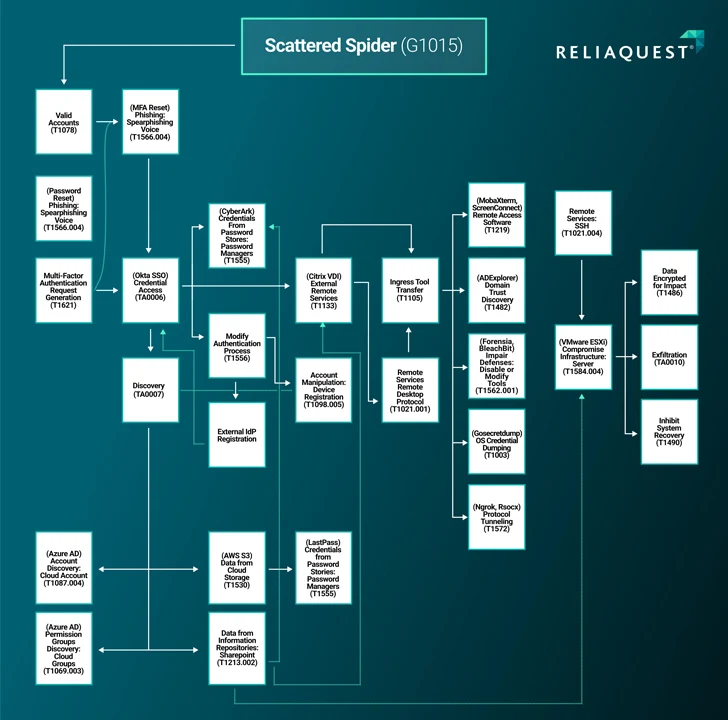
“The group’s ongoing action is a testament to the abilities of a very skilled danger actor or group acquiring an intricate comprehension of cloud and on-premises environments, enabling them to navigate with sophistication,” ReliaQuest researcher James Xiang said.
Identified this short article exciting? Adhere to us on Twitter and LinkedIn to examine much more exceptional content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 DJVU Ransomware’s Latest Variant ‘Xaro’ Disguised as Cracked Software
DJVU Ransomware’s Latest Variant ‘Xaro’ Disguised as Cracked Software