An examination of the indicators of compromise (IoCs) involved with the JumpCloud hack has uncovered evidence pointing to the involvement of North Korean point out-sponsored groups, in a model that is reminiscent of the source chain attack focusing on 3CX.
The conclusions occur from SentinelOne, which mapped out the infrastructure pertaining to the intrusion to uncover underlying styles. It can be truly worth noting that JumpCloud, previous week, attributed the attack to an unnamed “innovative country-state sponsored risk actor.”
“The North Korean danger actors reveal a large degree of creative imagination and strategic consciousness in their focusing on procedures,” SentinelOne security researcher Tom Hegel explained to The Hacker News. “The study results reveal a thriving and multifaceted tactic utilized by these actors to infiltrate developer environments.”
“They actively search for obtain to applications and networks that can provide as gateways to additional in depth possibilities. Their tendency to execute numerous degrees of offer chain intrusions before partaking in financially determined theft is noteworthy.”
In a connected progress, CrowdStrike, which is doing the job with JumpCloud to probe the incident, pinned the attack to a North Korean actor recognized as Labyrinth Chollima, a sub cluster in the notorious Lazarus Team, in accordance to Reuters.
The infiltration was employed as a “springboard” to goal cryptocurrency businesses, the information agency said, indicating an endeavor on element of the adversary to crank out unlawful revenues for the sanctions-hit country.
The revelations also coincide with a small-quantity social engineering marketing campaign identified by GitHub that targets the own accounts of employees of technology companies, utilizing a combine of repository invitations and destructive npm deal dependencies. The specific accounts are affiliated with blockchain, cryptocurrency, or on the web gambling sectors.
The Microsoft subsidiary attributed the marketing campaign to a North Korean hacking team it tracks under the title Jade Sleet (aka TraderTraitor).
“Jade Sleet typically targets buyers associated with cryptocurrency and other blockchain-associated corporations, but also targets suppliers employed by people corporations,” GitHub’s Alexis Wales stated.
The attack chains contain environment up bogus personas on GitHub and other social media expert services these types of as LinkedIn, Slack, and Telegram, while in some situations the danger actor is thought to have taken management of reputable accounts.
Under the assumed persona, Jade Sleet initiates speak to with the targets and invites them to collaborate on a GitHub repository, convincing the victims into cloning and operating the contents, which attribute decoy application with destructive npm dependencies that act as to start with-phase malware to obtain and execute next-stage payloads on the infected equipment.
Future WEBINARShield In opposition to Insider Threats: Grasp SaaS Security Posture Management
Anxious about insider threats? We’ve acquired you covered! Be a part of this webinar to take a look at realistic strategies and the techniques of proactive security with SaaS Security Posture Administration.
Be a part of Right now
The destructive npm deals, for every GitHub, are part of a campaign that to start with arrived to light previous month, when Phylum thorough a supply chain menace involving a unique execution chain that employs a pair of fraudulent modules to fetch an not known piece of malware from a distant server.
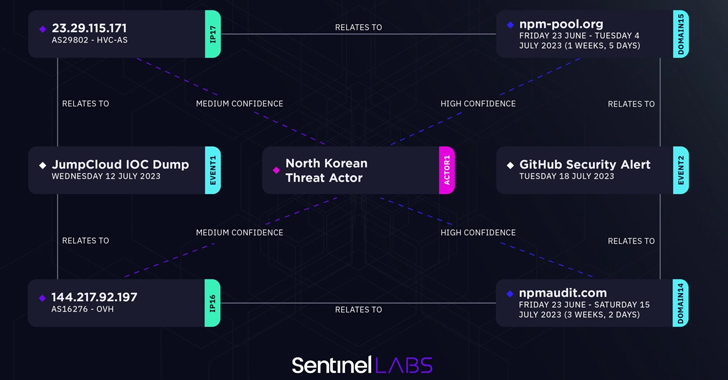
SentinelOne, in its most recent evaluation, stated 144.217.92[.]197, an IP address connected to the JumpCloud attack, resolves to npmaudit[.]com, a single of the 8 domains detailed by GitHub as utilized to fetch the next-stage malware. A second IP deal with 23.29.115[.]171 maps to npm-pool[.]org.
“It is obvious that North Korean risk actors are constantly adapting and discovering novel solutions to infiltrate focused networks,” Hegel stated. “The JumpCloud intrusion serves as a distinct illustration of their inclination in the direction of source chain targeting, which yields a multitude of probable subsequent intrusions.”
“The DPRK demonstrates a profound comprehending of the rewards derived from meticulously deciding upon large-benefit targets as a pivot place to perform supply chain assaults into fruitful networks,” Hegel extra.
Identified this post attention-grabbing? Abide by us on Twitter and LinkedIn to read through far more exceptional material we put up.
Some parts of this article are sourced from:
thehackernews.com

 A Few More Reasons Why RDP is Insecure (Surprise!)
A Few More Reasons Why RDP is Insecure (Surprise!)