Media businesses and large-profile experts in North Korean affairs have been at the acquiring stop of a new marketing campaign orchestrated by a risk actor recognised as ScarCruft in December 2023.
“ScarCruft has been experimenting with new infection chains, together with the use of a complex menace study report as a decoy, very likely focusing on people of threat intelligence like cybersecurity experts,” SentinelOne researchers Aleksandar Milenkoski and Tom Hegel explained in a report shared with The Hacker News.
The North Korea-linked adversary, also recognized by the name APT37, InkySquid, RedEyes, Ricochet Chollima, and Ruby Sleet, is assessed to be aspect of the Ministry of Point out Security (MSS), placing it apart from Lazarus Group and Kimsuky, which are things within just the Reconnaissance Common Bureau (RGB).

The group is acknowledged for its targeting of governments and defectors, leveraging spear-phishing lures to produce RokRAT and other backdoors with the top objective of covert intelligence collecting in pursuit of North Korea’s strategic interests.
In August 2023, ScarCruft was joined to an attack on Russian missile engineering business NPO Mashinostroyeniya alongside Lazarus Group in what has been considered as a “remarkably fascinating strategic espionage mission” intended to profit its controversial missile plan.
Previously this week, North Korean state media described that the country had carried out a test of its “underwater nuclear weapons procedure” in reaction to drills by the U.S., South Korea, and Japan, describing the workout routines as a threat to its nationwide security.
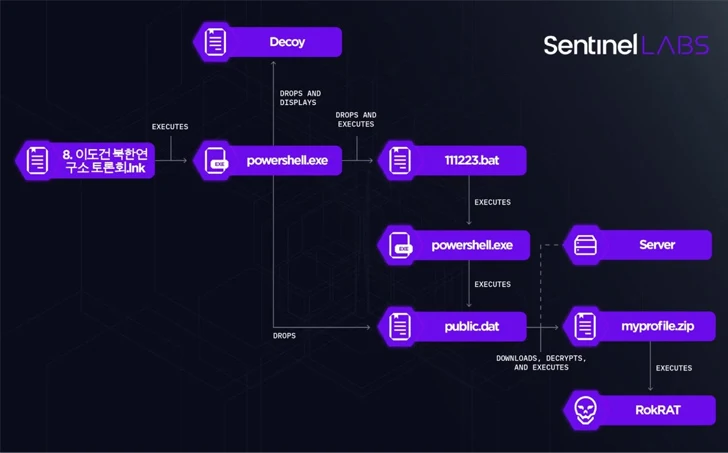
The most recent attack chain observed by SentinelOne specific an qualified in North Korean affairs by posing as a member of the North Korea Research Institute, urging the receiver to open a ZIP archive file that contains presentation products.
Though 7 of the nine information in the archive are benign, two of them are destructive Windows shortcut (LNK) information, mirroring a multi-stage an infection sequence earlier disclosed by Test Place in May 2023 to distribute the RokRAT backdoor.
There is evidence to recommend that some of the people today who were being targeted about December 13, 2023, were also beforehand singled out a thirty day period prior on November 16, 2023.
SentinelOne stated its investigation also uncovered malware – two LNK files (“inteligence.lnk” and “news.lnk”) as well as shellcode variants offering RokRAT – that’s reported to be element of the threat actor’s organizing and testing procedures.

While the former shortcut file just opens the legitimate Notepad software, the shellcode executed by means of news.lnk paves the way for the deployment of RokRAT, despite the fact that this an infection technique is nonetheless to be noticed in the wild, indicating its probably use for long run strategies.
The growth is a sign that the nation-condition hacking crew is actively tweaking its modus operandi possible in an effort and hard work to circumvent detection in reaction to general public disclosure about its tactics and methods.
“ScarCruft remains fully commited to attaining strategic intelligence and quite possibly intends to obtain insights into non-community cyber menace intelligence and protection approaches,” the researchers reported.
“This enables the adversary to get a better knowledge of how the international local community perceives developments in North Korea, therefore contributing to North Korea’s decision-earning procedures.”
Identified this short article exciting? Stick to us on Twitter and LinkedIn to read through extra exceptional content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Hackers Hijack Popular Java and Android Apps via Abandoned Libraries
Hackers Hijack Popular Java and Android Apps via Abandoned Libraries